JN0-232 Juniper Security, Associate (JNCIA-SEC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Juniper JN0-232 Security, Associate (JNCIA-SEC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is transit traffic in the Junos OS?
Which two statements are true about the NextGen Web Filtering (NGWF) feature on an SRX Series device? (Choose two.)
Which two statements are correct about the processing of NAT rules within a rule set? (Choose two.)
Which two characteristics of destination NAT and static NAT are correct? (Choose two.)
Which UI enables you to manage, monitor, and maintain multiple firewalls using a single interface?
Which security policy action will cause traffic to drop and a message to be sent to the source?
Which two statements are correct about NAT and security policy processing? (Choose two.)
You have a situation where legitimate traffic is incorrectly identified as malicious by your screen options.
In this scenario, what should you do?
Which two statements are correct about security zones and functional zones? (Choose two.)
What is the purpose of rate-limiting exception traffic in the Junos OS?
Which two statements about security zones are correct? (Choose two.)
Which two statements are correct about unified security policies? (Choose two.)
Click the Exhibit button.
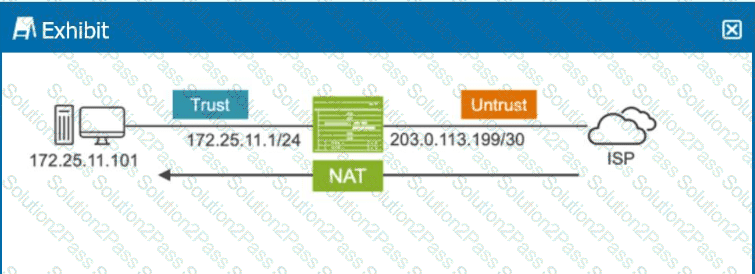
You must ensure that sessions can only be established from the external device.
Referring to the exhibit, which type of NAT is being performed?
What is the purpose of assigning logical interfaces to separate security zones in Junos OS?
Your company is acquiring a smaller company that uses the same private address range that your company currently uses in its North America division. You have a limited number of public IP addresses to use for the acquisition. You want to allow the new acquisition's users to connect to the existing services in North America.
Which two features would you enable on your SRX Series Firewall to accomplish this task? (Choose two.)
Click the Exhibit button.
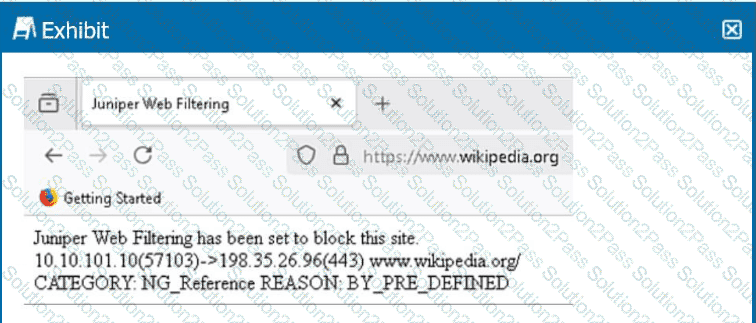
Referring to the exhibit, which two statements are correct? (Choose two.)
Click the Exhibit button.
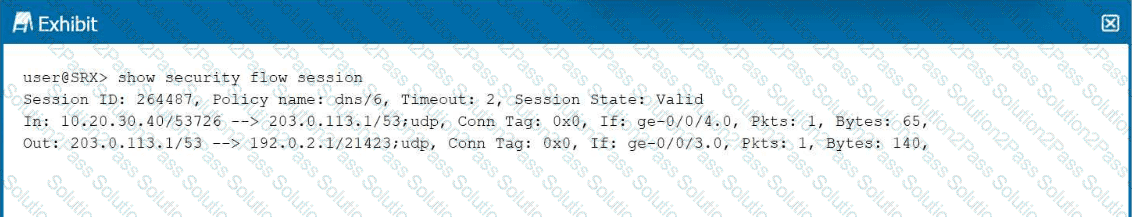
Referring to the exhibit, which two statements are correct about the traffic flow shown in the exhibit? (Choose two.)
Which two statements about destination NAT are correct? (Choose two.)
Click the Exhibit button.


Referring to the exhibit, which statement is correct?
