701-100 LPI DevOps Tools Engineer Free Practice Exam Questions (2026 Updated)
Prepare effectively for your LPI 701-100 DevOps Tools Engineer certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which Ansible command is used to manage and store sensitive data in encrypted files? (Specify ONLY the command without any path or parameters.)
If a Dockerfile references the container’s base image without a specific version tag, which tag of that image is used to create the container?
Which of the following statements regarding microservices are true? (Choose three correct answers.)
A recently installed application writes log data to /opt/app/log/info.log. If Filebeat is already installed and set up for communication with a remote Logstash, what has to be done in order to submit the log data of the new application to Logstash?
Which of the following container names could have been assigned automatically by Docker?
Which statements are true regarding databases during the deployment of a new release of a service using canary deployment? (Choose two correct answers.)
Which of the following Ansible tasks copies the file example.txt to a manage system?
A Dockerfile contains the statements:
COPY data/ /data/
VOLUME /data
What happens when the resulting container is started without any additional volume configuration? (Choose two correct answers.)
Which Ansible modules can be used to change the contents of a file? (Choose three correct answers.)
Which of the following goals are favored by agile software development methodologies? (Choose two correct answers.)
Which of the following mechanisms are used for service discovery in a container environment? (Choose two correct answers.)
Consider the following Kubernetes Deployment:

With the ReplicaSet:
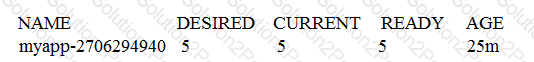
And the Pods:
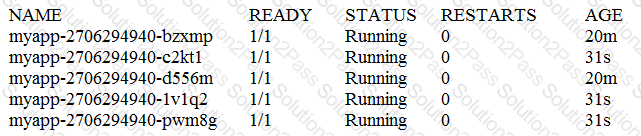
What happens if one of the Pods is terminated with the command kubect1 pod delete?
Which of the following statements describes the principal concept behind test driven development?
The following command is issued on two docker nodes:
docker network create --driver bridge isolated_nw
Afterwards, one container is started at each node with the parameter --network=isolated_nw. It turns out that the containers can not interact with each other. What must be done in order to allow the containers to interact with each other? (Choose two correct answers.)
Which of the following statements are true about Jenkins? (Choose two correct answers.)
What is the Puppet equivalent to an Ansible Playbook called?
Which configuration option in the Ansible inventory is issued control privilege escalation of the remote user?
What does the command packer validate template.json do?
