NS0-403 Netapp NetApp Certified Hybrid Cloud Implementation Engineer Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Netapp NS0-403 NetApp Certified Hybrid Cloud Implementation Engineer certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What are three version control processes? (Choose three.)
You have a StorageGRID solution with 1 PB of object data. All data is geographically distributed and erasure coded across three sites. You are asked to create a new information lifecycle management (ILM) policy that will keep a full copy of the grid in Amazon S3.
In this scenario, which component must be configured for the ILM policy?
Your customer is using Astra Control Service to back up applications. They require a consistent copy of the data that also captures data in flight.
Which two applications will Astra support in this scenario? (Choose two.)
You are asked to accelerate your company's release cycle by adopting DevOps practices. As part of this project, you want to use infrastructure as code to deploy your storage environments during the CI/CD pipeline.
In this scenario, which tool would you use to satisfy this requirement?
As shown in the exhibit, you are installing NetApp Cloud Secure agents.
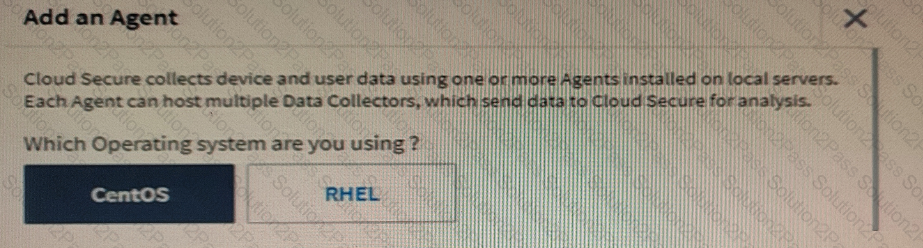
In this scenario, which component must be deployed for Cloud Secure to report findings?
A customer was running a traditional application with the data being provided by an NetApp ONTAP NFSv3 export. The customer is now migrating that same application to run with a container in a Kubernetes environment using NetApp Trident.
In this scenario, how would the customer ensure that the new container-based application has access to the same data?
As a DevOps engineer, you want a single tool that uses one automation language consistently across orchestration, application deployment, and configuration management.
In this scenario, which tool would you choose?
You have an AFF A400 system with NetApp ONTAP 9.8 installed. You want to configure the NetApp Cloud Tiering service to tier data to AWS object storage. The communication between your cluster and the AWS cloud needs to be encrypted. You have installed the FabricPool license, but your ONTAP cluster cannot reach the S3 bucket.
Which two configurations are causing the error? (Choose two.)
An organization is implementing infrastructure as code to deploy NetApp Cloud Volumes ONTAP instances.
In this scenario, what are two ways in which this implementation improves operation efficiencies? (Choose two.)
A customer made a mistake and deleted some important notes in their Jupyter notebooks. The customer wants to perform a near-instantaneous restore of a specific snapshot for a JupyterLab workspace.
Which command in the NetApp DataOps Toolkit will accomplish this task?
You are using Nvidia DeepOps to deploy Kubernetes clusters on top of NetApp ONTAP AI systems. In this scenario, which automation engine is required?
Using Astra Control, which three steps must be completed to protect your Kubernetes-based applications? (Choose three.)
You are using REST APIs to deploy and manage storage that is provided by NetApp Cloud Volumes ONTAP in Microsoft Azure. You have written a Python script that contains a POST request to the following URL: http://localhost/occm/api/azure/vsa/working-environments. However, you receive a 401 response failure message that indicates that the user is not authenticated.
In this scenario, which two steps must you perform to communicate with an endpoint? (Choose two.)
During software development, a team creates use cases, class diagrams, Unified Modeling Language models, software architecture documents, requirements documents, and design documents.
Collectively, in this scenario, what are these tangible by-products called?
A team Is Implementing automated builds of Dev/Test environments. The team must ensure consistent and repeatable environments.
In this scenario, which two actions will satisfy this requirement? (Choose two.)
You are creating an Ansible playbook to deploy a NetApp ONTAP cluster. You want to take advantage of a loop to automate the creation of several volumes.
What would accomplish this task?
A)
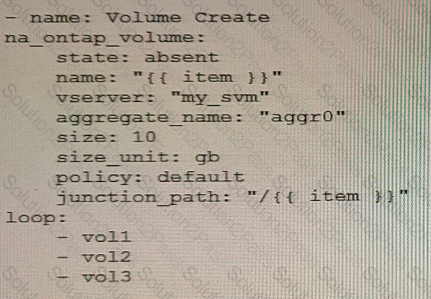
B)
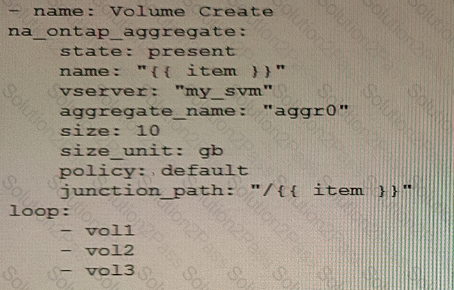
C)
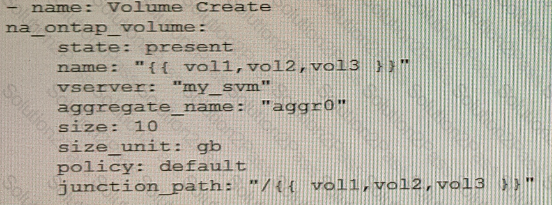
D)
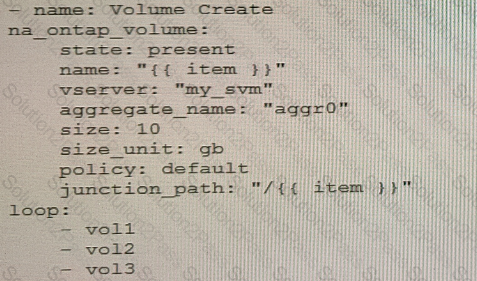
You used a Terraform configuration to create a number of resources in Google Cloud for testing your applications. You have completed the tests and you no longer need the infrastructure. You want to delete all of the resources and save costs.
In this scenario, which command would you use to satisfy the requirements?
Your organization is adopting DevOps principles to deliver innovation rapidly. Which three methods support this approach? (Choose three.)
