NSK300 Netskope Certified Cloud Security Architect Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Netskope NSK300 Netskope Certified Cloud Security Architect Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Review the exhibit.
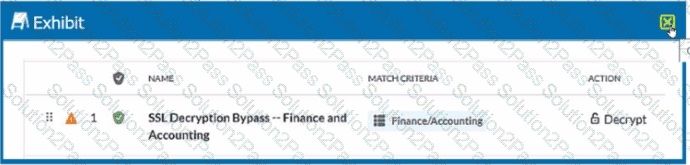
You created an SSL decryption policy to bypass the inspection of financial and accounting Web categories. However, you still see banking websites being inspected.
Referring to the exhibit, what are two possible causes of this behavior? (Choose two.)
You created a Real-time Protection policy that blocks all activities to non-corporate S3 buckets, but determine that the policy is too restrictive. Specifically, users are complaining that normal websites have stopped rendering properly.
How would you solve this problem?
Users at your company's branch office in San Francisco report that their clients are connecting, but websites and SaaS applications are slow When troubleshooting, you notice that the users are connected to a Netskope data plane in New York where your company's headquarters is located.
What is a valid reason for this behavior?
You are using Netskope CSPM for security and compliance audits across your multi-cloud environments. To decrease the load on the security operations team, you are researching how to auto-re mediate some of the security violations found in low-risk environments.
Which statement is correct in this scenario?
Your company just had a new Netskope tenant provisioned and you are asked to create a secure tenant configuration. In this scenario, which two default settings should you change? {Choose two.)
You are deploying the Netskope Client in a multi-user VDI environment and need to determine the command to deploy the MSI.
Which three parameters are required in this scenario? (Choose three.)
You want to integrate with a third-party DLP engine that requires ICAP. In this scenario, which Netskope platform component must be configured?
Your organization's software deployment team did the initial install of the Netskope Client with SCCM. As the Netskope administrator, you will be responsible for all up-to-date upgrades of the client.
Which two actions would be required to accomplish this task9 (Choose two.)
You are deploying the Netskope Client to Windows devices. The following command line would be used to install the client MSI file:

In this scenario, what is
Review the exhibit.
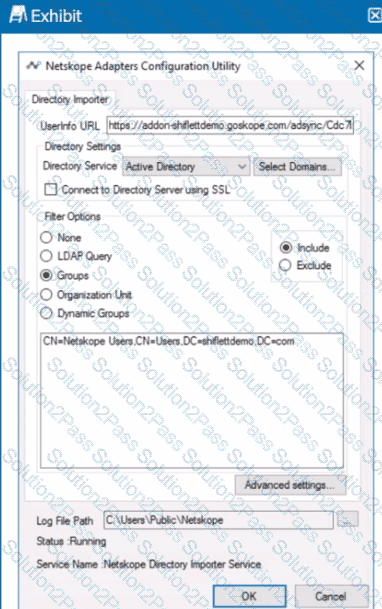
You installed Directory Importer and configured it to import specific groups ot users into your Netskope tenant as shown in the exhibit. One hour after a new user has been added to the domain, the user still has not been provisioned to Netskope.
What are three potential reasons for this failure? (Choose three.)
You are asked to create a customized restricted administrator role in your Netskope tenant for a newly hired employee. Which two statements are correct in this scenario? (Choose two.)
Users in your network are attempting to reach a website that has a self-signed certificate using a GRE tunnel to Netskope. They are currently being blocked by Netskope with an SSL error. How would you allow this traffic?
You are assisting your network administrator to troubleshoot an issue with client-based NPA.
In the Netskope UI, what information do you need from the administrator to run the NPA troubleshooter for this user? (Choose two.)
Your Netskope Client tunnel has connected to Netskope; however, the user is not receiving any steering or client configuration updates What would cause this issue?
Your customer is currently using Directory Importer with Active Directory (AD) to provision users to Nelskope. They have recently acquired three new companies (A. B. and C) and want to onboard users from the companies onto the NetsKope platform. Information about the companies is shown below.
- Company A uses Active Directory.
-- Company B uses Azure AD.
-- Company C uses Okta Universal Directory.
Which statement is correct in this scenario?
You jus! deployed and registered an NPA publisher for your first private application and need to provide access to this application for the Human Resources (HR) users group only. How would you accomplish this task?
Review the exhibit.

You are the proxy administrator for a medical devices company. You recently changed a pilot group of users from cloud app steering to all Web traffic. Pilot group users have started to report that they receive the error shown in the exhibit when attempting to access the company intranet site that is publicly available. During troubleshooting, you realize that this site uses your company's internal certificate authority for SSL certificates.
Which three statements describe ways to solve this issue? (Choose three.)
You are designing a Netskope deployment for a company with a mixture of endpoints, devices, and services.
In this scenario, what would be two considerations for using IPsec as part of the design? (Choose two.)
A company has deployed Explicit Proxy over Tunnel (EPoT) for their VDI users They have configured Forward Proxy authentication using Okta Universal Directory They have also configured a number of Real-time Protection policies that block access to different Web categories for different AD groups so. for example, marketing users are blocked from accessing gambling sites. During User Acceptance Testing, they see inconsistent results where sometimes marketing users are able to access gambling sites and sometimes they are blocked as expected They are seeing this inconsistency based on who logs into the VDI server first.
What is causing this behavior?
A recent report states that users are using non-sanctioned Cloud Storage platforms to share data Your CISO asks you for a list of aggregated users, applications, and instance IDs to increase security posture
Which Netskope tool would be used to obtain this data?
