NCP-EUC Nutanix Certified Professional - End User Computing (NCP-EUC) 6.10 Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Nutanix NCP-EUC Nutanix Certified Professional - End User Computing (NCP-EUC) 6.10 Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An administrator has been tasked with increasing security by setting permissions based on department.
Which feature can the administrator use to best accomplish this task?
A Windows IO VM fails to power on With an NVIDIA vCPU profile in ESXi 7. The VM is configured with NVIDIA profile by selecting Shared PCl Device, adding the NVIDIA GRID vCPU device. and selecting the Profile under VM settings.
The following error message is displayed in the vSphere web client:
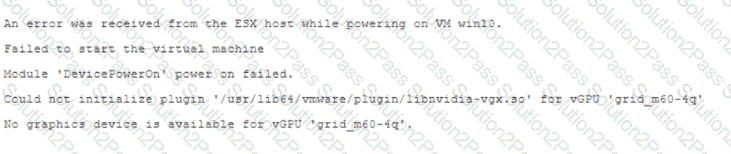
What should be done to resolve this issue?
An administrator has finished deploying the Citrix backend infrastructure to Xi Leap and needs to expose the Citrix NetScaler VPX private VIP to the internet in order for users to be able to access the Citrix VDI desktops upon a DR failover.
What should the administrator perform in order for public internet access to be allowed to the Citrix NetScaler VPX?
Recently, the vice president Of IT infrastructure was migrated from a physical computer to a virtual desktop. The administrator wants to ensure that this user has the best possible experience and wants to be notified if any CPU resource constraints.
The cluster's average CPU utilization is 20%.
What step would help the administrator to know when there are resource problems on the virtual desktop?
The operations team have been tasked with increasing overall datacenter efficiency with a target minimum of 80% CPU, memory, and storage capacity utilization. They are requesting usage data from all application owners be sent on a monthly basis to be ingested into their capacity management software.
An administrator has an implementation of four Nutanix clusters under the management of a single Prism Central Instance.
How should the administrator best provide the data needed to the operations team to ensure adherence to the datacenter utilization directive?
By default, Prism Central provides 18 predefined system report configurations that address common use cases and requirements of an organization's infrastructure management.
What is a valid action for predefined report configurations?
An administrator has been asked to enable mufti-monitor support for a graphic designer that needs to be able to use four monitors.
After on boarding the designer on to the Frame desktop, the end user does not see the ability to use all four monitors while using the Firefox web browser.
What should the administrator do to enable the ability to use all four monitors?
An administrator has finished setting up a Frame environment and has to finish preparing the Sandbox image. During the publishing andtesting phase, the administrator notices issue with the Sysprep process.
Which tool can the administrator use to prepare the Sysprep of the sandbox with error parsing?
Due to a recent unprivileged access incident, an administrator needs to better protect critical applications by preventing lateral movement within the EUC environment.
Which Flow Network Security feature will accomplish this task?
A new client has just deployed a new Frame account, During the testing phase, the security team found that they had bidirectional clipboard, capabilities, the ability to transfer files, and connectivity to unauthorized external storage devices.
What should the administrator do to secure the environment, based on the security team's feedback?
A company is planning to implement Citrix Virtual Apps and Desktops on Nutanix clusters running AHV.
The initial implementation will be sized for 1000 virtual desktops with Windows 1 1, Microsoft Office 2021 and Adobe Creative Cloud All Apps installed.
What is the correct prerequisite to implement a successful installation of the Nutanix AHV MCS Plug-in?
A company has deployed Horizon on a Nutanix cluster running the ESXi hypervisor. They are starting the configuration for the deployment of 1000 virtual desktops running Windows 10 in a Linked Clone Desktop Pool.
The company has these requirements:
• Reduced time for initial virtual desktop deployment
• Fast recompose time when updating the pool with patches and new application installs
• Provide a high level of availability to the pool
What should the company enable, that will allow this Nutanix VDI implementation to meet the stated requirements?
A new EUC environment is being designed for graphics-intensive workloads. An administrator has determined that L40S GPUs (48 GB) with L40S-12Q (12 GB) profiles will be needed. The administrator chooses an NX-9151-G9, which can fit four L40S GPUs.
How many virtual desktops per server can be estimated based on the GPU requirements?
A company has started planning for migration to Windows 11. An administrator is looking over the requirements for boot and security settings at the VM level to prepare to build new base images.
Which option can the administrator exclude from the requirements list for running Windows 11 VMs on AHV?
An administrator needs to deploy virtual desktops to a Hyper-V Nutanix cluster with writable differencing disks, The administrator will use read only master image with clones that link back to the image.
Which native feature will the cluster use to complete this task?
An administrator needs to enable Data-At-Rest Encryption on an AHV cluster. The cluster has a mix of Self-Encrypting Drives (SEDs) and standard SSDs.
Which option is supported in this scenario?
An administrator is asked to configure a container to support 2000 non-persistent linked clone desktops.
What is the optimal configuration of this container?
A company wants their Nutanix VDI environment to have these characteristics:
• 3000 non-persistent desktops
• 500 RDSH-based VMS
• 100 AppStacks
How many storage containers should an administrator create to satisfy these requirements?
Refer to the exhibit.
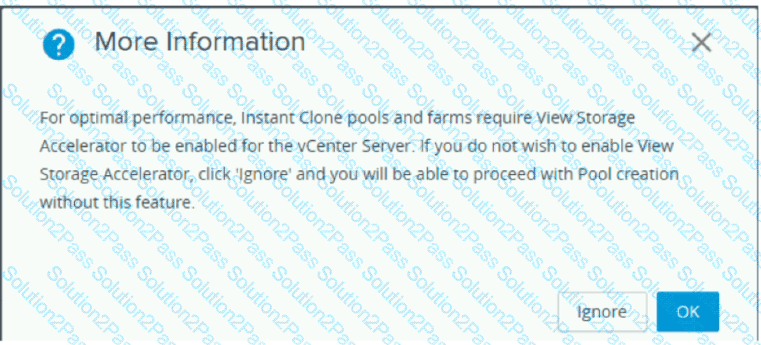
An administrator is deploying an Instant Clone desktop pool on an 8-node Nutanix cluster. The system displays a warning message, as shown in the exhibit.
What should the administrator do to resolve the issue?
A business unit requires different syslog servers for specific clusters.
Which tool can be used to set up a syslog monitoring configuration to avoid propagating the configuration to all clusters?
