NCS-Core Nutanix Certified Services Core Infrastructure Professional (NCS-Core 6.8) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Nutanix NCS-Core Nutanix Certified Services Core Infrastructure Professional (NCS-Core 6.8) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
While creating an image placement policy on the organizations AOS 5.15-based Nutanix cluster, the administrator wants to ensure there are no restrictions on using the selected images on clusters outside of the identified set.
What type of Policy Enforcement must the administrator choose?
After deploying an AHV cluster connected to Cisco Nexus 9k switches, unexpected network behavior is observed. The consultant needs to rule out physical network mis-cabling without returning to the datacenter.
Which command from the host should the consultant run?
An administrator needs to make sure an RF3 cluster can survive a failure of two complete racks without negatively affecting performance. The current cluster configuration consists of the following:
• 30 All Flash Nodes: distributed 10 nodes per rack across three 42U racks
• Each node is configured with 20TB usable storage all flash (Cluster Total 600TB Usable)
• Current cluster utilization is 500TB storage
• Storage containers have Erasure Coding enabled
Which configuration changes should be made to make sure the cluster meets the requirements?
In a Nutanix cluster, a Protection Domain contains 50 entities that are replicated to a remote Single Node Replication Target.
The current schedule configuration is as follows:
• Repeat every 6 hours
• Local Retention Policy 1
• Remote Retention Policy 8
• Starting time 12 am
At 8 am on Monday, the administrator discovers that a protected VM is corrupted. The latest good state was Sunday 2 pm. The administrator needs to maintain current protection.
Which strategy should the administrator use to meet these requirements?
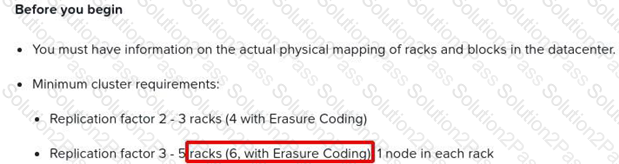
What is the minimum number of nodes required for a Nutanix Cluster to support Replication Factor 3 (RF3) on a storage container?
After installation, network ports are properly configured with the default active-backup bonding. One 10GbE port goes to switch 1, and another 10GbE port goes to switch 2.
A consultant tests failover by manually disconnecting one of the cables and notices it is taking too much time to failover, which is causing excessive packet loss.
What should be enabled to resolve this issue?
An administrator is deploying an application using Nutanix Volumes. After configuring the volume group and connecting the guest's iSCSI initiator to the volume group, they begin performance testing.
The administrator learns that performance on the virtual disk attached to the iSCSI initiator is far less than that of a virtual disk connected directly to the VM.
Which situation is causing this condition?
An administrator recently added VLAN 205 CRM in Prism Element. The workloads attached to the associated NICs are unable to establish network connectivity.
Which Layer 2 protocol allows the administrator to troubleshoot this issue from Prism Element?
During a pre-engagement call, a customer explains that network cables are missing from the boxes. The consultant examines the bill of materials more closely to verify the quantity and type required by the hardware. The rack is already equipped with one OOBM Ethernet switch and two 10GbE SFP+ ToR switches.
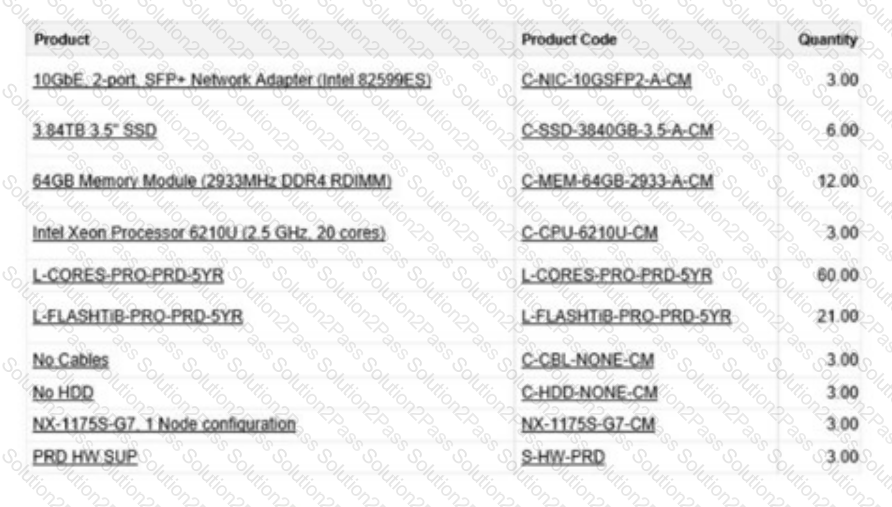
Which cables should the consultant recommend to the customer for implementing in this scenario?
An administrator needs to maximize storage potential in a six-node cluster. The container is configured with the following:
Post-process compression
Capacity deduplication
What should the administrator configure to increase space savings?
According to Nutanix best practices, which interface configuration should be used when setting up the default bond?
A consultant is using a customer’s switch for installation. Although the 10GbE ports for each of the hosts are connected to the switch, the nodes fail to be discovered.
What is causing the issue?
A customer buys ultimate licensing and wants to use the built-in Nutanix software encryption on their new AHV cluster. The customer needs to create three storage containers and asks the consultant to complete the process as fast as possible.
In which order should the cluster be deployed?
A systems administrator configures a protection domain replication between two Nutanix clusters. After the first successful replication , the administrator tests DR by clicking activate on the remote cluster.
While VMs are active on the remote cluster, the protection domain is marked as active on both clusters.
What steps are required to return both clusters to their original state?
An administrator finds that home shares cannot be configured in a new Files 3.5 deployment. Why is this happening?
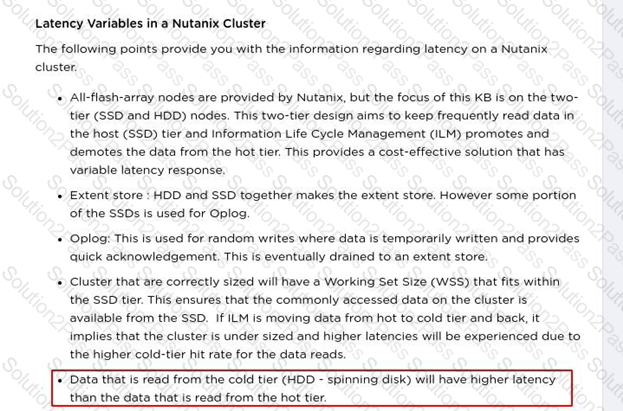
An administrator receives reports about a Nutanix environment. The investigation finds the following;
• VMs are experiencing very high latency
• Each node is equipped with a single SSD, utilized at 95%
• Each node is equipped with three HDDs, utilized at 40%
Why are the guest VMs experiencing high latency?
An administrator migrates a VM onto a new Nutanix cluster. After the migration, the administrator observes the following conditions:
• Cluster memory utilization: 64%
• Cluster CPU utilization: 19%
• Cluster storage utilization: 32%
• Average VM CPU utilization: 25%
• Average VM CPU ready%: 24%
• Average VM memory utilization: 60%
Which two changes should the administrator make to improve VM performance? (Choose two.)
A VM is exhibiting one or more of the following baseline values based on the past 30 days:
• CPU usage < 20%
• CPU ready time < 5%
• Memory usage < 50% (moderately) or < 20% (severely)
• Memory swap rate = 0 Kbps
Which type of VM is being described?
A consultant is planning an installation and needs to collect configuration items to be used during the install. The data needed from the customer are IP addresses, Gateway, DNS servers, and NTP Servers.
Which Cluster Deployment document must be completed with the customer?
The following alert appears on the file server alerts tab in the file server dashboard:
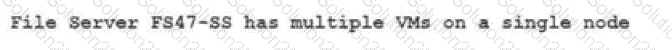
Which two events can generate this alert? (choose two)