1z0-1104-25 Oracle Cloud Infrastructure 2025 Security Professional Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Oracle 1z0-1104-25 Oracle Cloud Infrastructure 2025 Security Professional certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Challenge 1 - Task 1
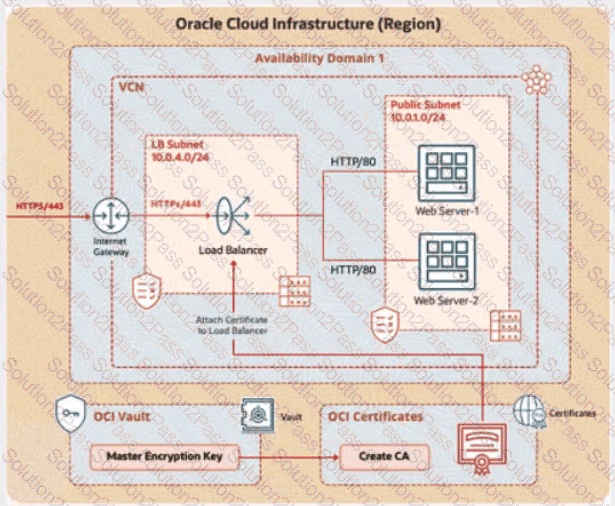
Integrate TLS Certificate Issued by the OCI Certificates Service with Load Balancer
You are a cloud engineer at a tech company that is migrating its services to Oracle Cloud Infrastructure (OCI). You are required to set up secure communication for your web application using OCI's Certificate service. You need to create a Certificate Authority (CA), issue a TLS/SSL server certificate, and configure a load balancer to use this certificate to ensure encrypted traffic between clients and the backend servers.
Review the architecture diagram, which outlines the resources you'll need to address the requirement.
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
OCI Vault to store the secret required by the program, which is created in the root compartment as PBI_Vault_SP
Task 1: Create and Configure a Virtual Cloud Network (VCN)
Create a Virtual Cloud Network (VCN) namedPBT-CERT-VCN-01with the following specifications:
VCN with a CIDR block of 10.0.0.0/16
Subnet 1 (Compute Instance):
Name:Compute-Subnet-PBT-CERT
CIDR Block:10.0.1.0/24
Subnet 2 (Load Balancer):
Name:LB-Subnet-PBT-CERT-SNET-02
CIDR Block:10.0.2.0/24
Internet Gatewayfor external connectivity
Route table and security lists:
Security List namedPBT-CERT-CS-SL-01for Subnet 1 (Compute-Subnet-PBT-CERT) to allow SSH (port 22) traffic
Security List namedPBT-CERT-LB-SL-01for Subnet 2 (LB-Subnet-PBT-CERT) to allow HTTPS (port 443) traffic
"Enter the OCID of the created VCN in the text box below.
Task 6: Create Load Balancer and Attach Certificate
Create a Load Balancer with the name PBT-CERT-LB-01 in subnet LB-Subnet-PBT-CERT-SNET-02
Create a Listener for the load balancer, where:
Name: PBT-CERT-LB_LTSN_01
Protocol: HTTPS
Port: 443
Attach the certificate PBT-CERT-01-
Attach the security list PBT-CERT-LB-SL-01 to subnet LB-Subnet-PBT-CERT-SNET-02
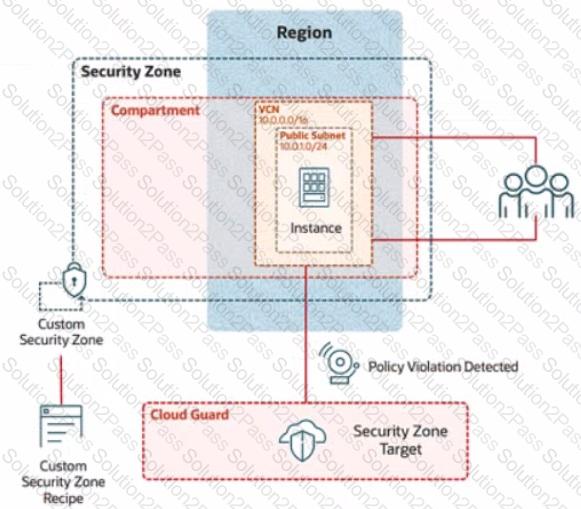
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 4: Create a Public Subnet
Create a public subnet named IAD-SP-PBT-PUBSNET-01, within the VCN IAD-SP-PBT-VCN-01
use a CIDR block of 10.0.1.0/24 and configure the subnet to use the internet Gateway
Task 3: Create a Master Encryption Key
Note: OCI Vault to store the key required by this task is created in the root compartment as PBI_Vault_SP
Create an RSA Master Encryption Key (MEK), where:
Key name: PBT-CERT-MEK-01-
For example, if your username is 99008677-lab.user01, then the MEK name should be PBT-CERT-MEK-01990086771abuser01
Ensure you eliminate special characters from the user name.
Key shape: 4096 bits
Enter the OCID of the Master Encryption Key created in the provided text box:
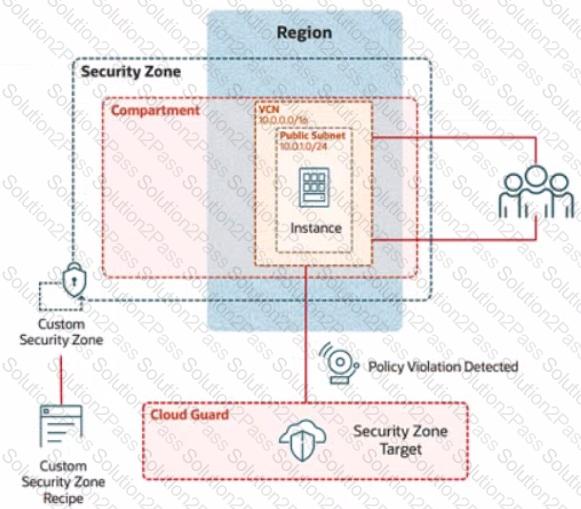
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 2: Create a Security Zone
Create a security Zone named IAD_SAP-PBT-CSZ-01 in your assigned compartement and associate it with the Custom Security Zone Recipe (IAD-SAP-PBT-CSP-01) created in the previous task.
Enter the OCID of the created Security zone in the box below.

In Oracle Cloud Infrastructure (OCI), bare metal instances provide customers with direct access to the underlying hardware. To mitigate security risks when a customer terminates a bare metal instance, OCI utilizes Root-of-Trust hardware.
What is the primary function of the Root-of-Trust hardware in this context?
A company has deployed OCI Zero Trust Packet Routing (ZPR) to secure its network. They have two compute instances, VM1-01 and VM-02, in a public subnet. VM-01 is tagged with the security attribute app:vm01, and VM-02 is tagged with app:vm02. The VCN is labeled with network:vcn01, The ZPR policy states:

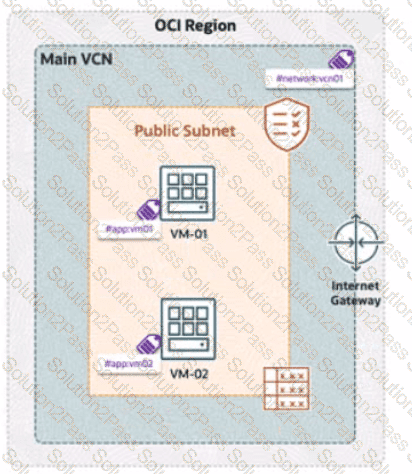
"What is the expected outcome of this policy?
"Your company is building a highly available and secure web application on OCI. Because of increasing malicious web-based attacks, the security team has mandated that web servers should not be exposed directly to the Internet.
How should you architect the solution while ensuring fault tolerance and security?
During your investigation of a load balancer issue, you discovered that all back-end servers associated with one of the affected listeners were reported as unhealthy. However, when you checked the back-end servers, they seemed to be working just fine.
What might be causing this issue?
An OCI administrator notices that a compute instance running in the production compartment is unable to create Object Storage buckets using the OCI CLI command:
oci os bucket create --name mybucket --compartment-id
The error message returned states:
"NotAuthorizedOrNotFound: You are not authorized to perform this action."
The administrator verifies that the instance has Internet access and can reach OCI endpoints.
What then could be causing the issue?
