PSE-Strata Paloalto Networks Palo Alto Networks System Engineer Professional - Strata Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks PSE-Strata Palo Alto Networks System Engineer Professional - Strata certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two configuration items are required when the NGFW needs to act as a decryption broker for multiple transparent bridge security chains? (Choose two.)
What are three key benefits of the Palo Alto Networks platform approach to security? (Choose three)
Which CLI command allows visibility into SD-WAN events such as path Selection and path quality measurements?
Which Palo Alto Networks pre-sales tool involves approximately 4 hour interview to discuss a customer's current security posture?
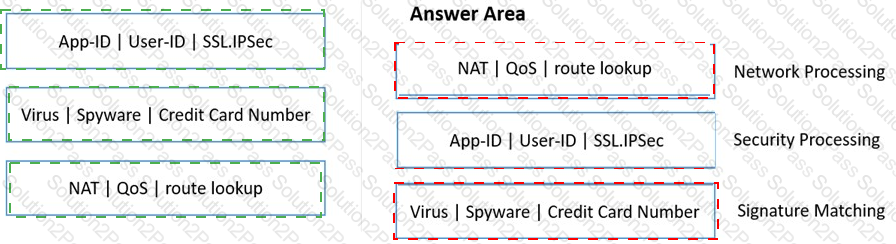
Match the functions to the appropriate processing engine within the dataplane.

Which two tabs in Panorama can be used to identify templates to define a common base configuration? (Choose two.)
A customer has business-critical applications that rely on the general web-browsing application. Which security profile can help prevent drive-by-downloads while still allowing web-browsing traffic?
What is the recommended way to ensure that firewalls have the most current set of signatures for up-to-date protection?
Which statement best describes the business value of Palo Alto Networks Zero Touch Provisioning (ZTP)?
What are two presales selling advantages of using Expedition? (Choose two.)
A customer is starting to understand their Zero Trust protect surface using the Palo Alto Networks Zero Trust reference architecture.
What are two steps in this process? (Choose two.)
Which three methods used to map users to IP addresses are supported in Palo Alto Networks firewalls? (Choose three.)
Which four steps of the cyberattack lifecycle does the Palo Alto Networks Security Operating Platform prevent? (Choose four.)
Which three components are specific to the Query Builder found in the Custom Report creation dialog of the firewall? (Choose three.)
An endpoint, inside an organization, is infected with known malware that attempts to make a command-and-control connection to a C2 server via the destination IP address
Which mechanism prevents this connection from succeeding?
Which three features are used to prevent abuse of stolen credentials? (Choose three.)
How often are the databases for Anti-virus. Application, Threats, and WildFire subscription updated?
Which three categories are identified as best practices in the Best Practice Assessment tool? (Choose three.)
Which two configuration elements can be used to prevent abuse of stolen credentials? (Choose two.)
In which two ways can PAN-OS software consume MineMeld outputs? (Choose two.)