SSE-Engineer Paloalto Networks Palo Alto Networks Security Service Edge Engineer Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks SSE-Engineer Palo Alto Networks Security Service Edge Engineer certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
When using the traffic replication feature in Prisma Access, where is the mirrored traffic directed for analysis?
Strata Logging Service is configured to forward logs to an external syslog server; however, a month later, there is a disruption on the syslog server.
Which action will send the missing logs to the external syslog server?
Which feature within Strata Cloud Manager (SCM) allows an operations team to view applications, threats, and user insights for branch locations for both NGFW and Prisma Access simultaneously?
Which policy configuration in Prisma Access Browser (PAB) will protect an organization from malicious BYOD and minimize the impact on the user experience?
An engineer has configured IPSec tunnels for two remote network locations; however, users are experiencing intermittent connectivity issues across the tunnels.
What action will allow the engineer to receive notifications when the IPSec tunnels are down or experiencing instability?
A user connected to Prisma Access reports that traffic intermittently is denied after matching a Catch-All Deny rule at the bottom and bypassing HIP-based policies. Refreshing VPN connection restores the access.
What are two reasons for this behavior? (Choose two.)
A customer is implementing Prisma Access (Managed by Strata Cloud Manager) to connect mobile users, branch locations, and business-to- business (B2B) partners to their data centers.
The solution must meet these requirements:
The mobile users must have internet filtering, data center connectivity, and remote site connectivity to the branch locations.
The branch locations must have internet filtering and data center connectivity.
The B2B partner connections must only have access to specific data center internally developed applications running on non-standard ports.
The security team must have access to manage the mobile user and access to branch locations.
The network team must have access to manage only the partner access.
How should Prisma Access be implemented to meet the customer requirements?
An intern is tasked with changing the Anti-Spyware Profile used for security rules defined in the GlobalProtect folder. All security rules are using the Default Prisma Profile. The intern reports that the options are greyed out and cannot be modified when selecting the Default Prisma Profile.
Based on the image below, which action will allow the intern to make the required modifications?
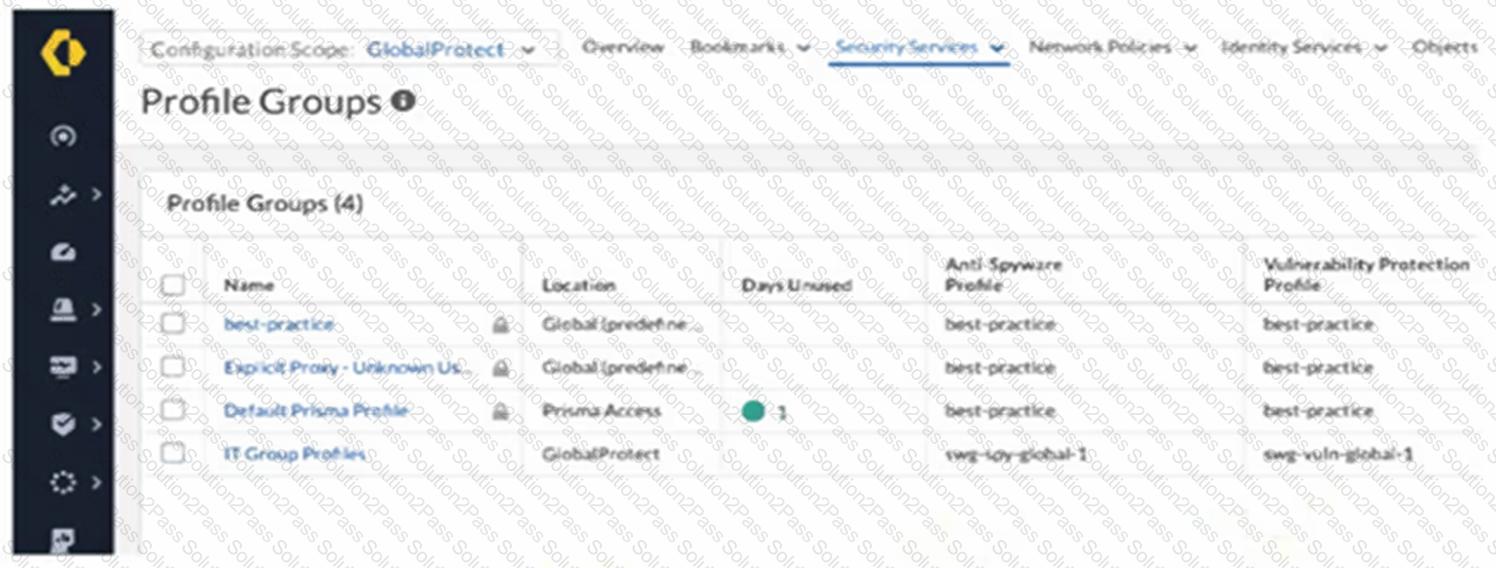
A company has a Prisma Access deployment for mobile users in North America and Europe. Service connections are deployed to the data centers on these continents, and the data centers are connected by private links.
With default routing mode, which action will verify that traffic being delivered to mobile users traverses the service connection in the appropriate regions?
An engineer has configured a new Remote Networks connection using BGP for route advertisements. The IPSec tunnel has been established, but the BGP peer is not up.
Which two elements must the engineer validate to solve the issue? (Choose two.)
Which two statements apply when a customer has a large branch office with employees who all arrive and log in within a five-minute time period? (Choose two.)
Based on the image below, which two statements describe the reason and action required to resolve the errors? (Choose two.)
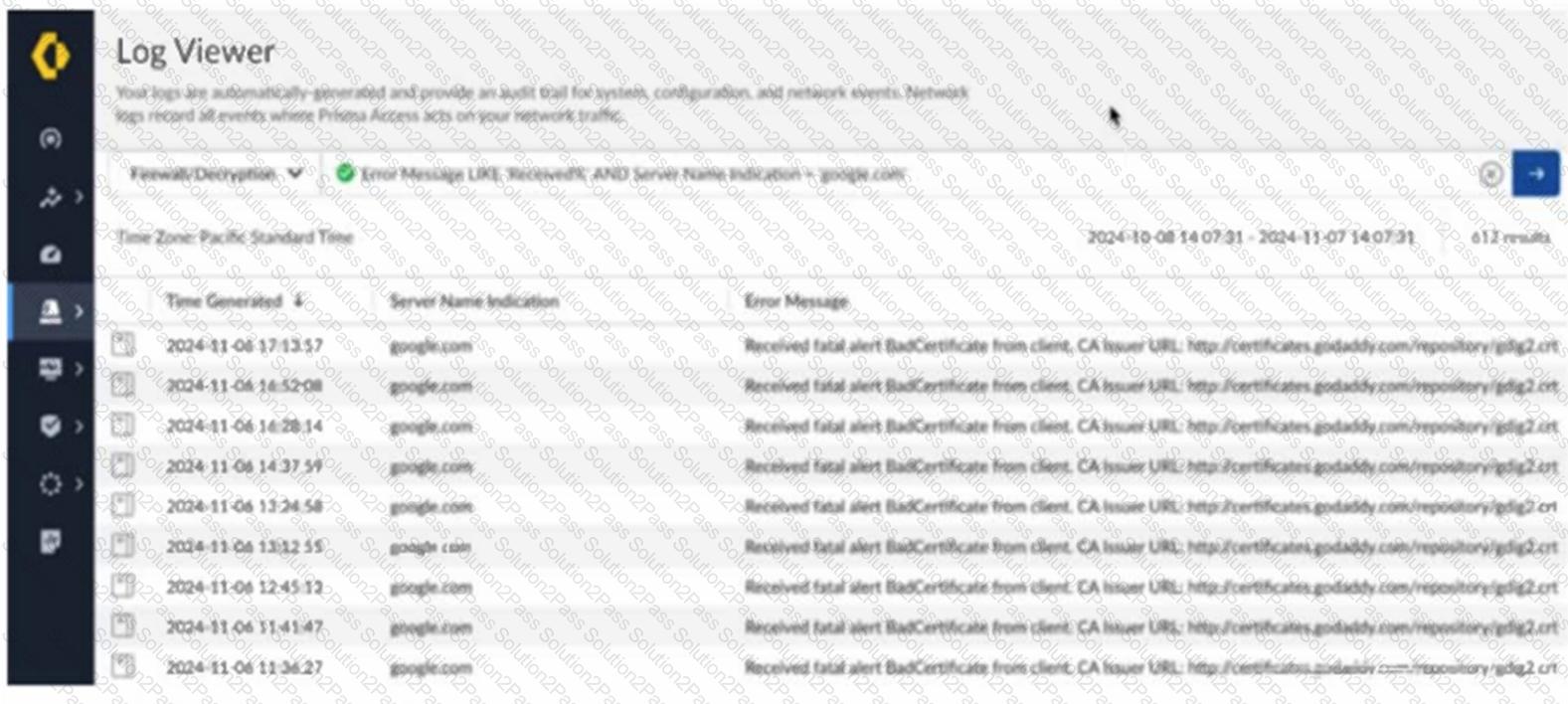
What must be configured to accurately report an application's availability when onboarding a discovered application for ZTNA Connector?
Which overlay protocol must a customer premises equipment (CPE) device support when terminating a Partner Interconnect-based Colo-Connect in Prisma Access?
How can a network security team be granted full administrative access to a tenant's configuration while restricting access to other tenants by using role-based access control (RBAC) for Panorama Managed Prisma Access in a multitenant environment?
