PEGACPSSA23V1 Pegasystems Certified Pega Senior System Architect 23 Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Pegasystems PEGACPSSA23V1 Certified Pega Senior System Architect 23 Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
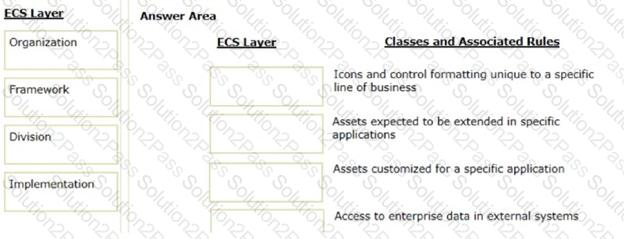
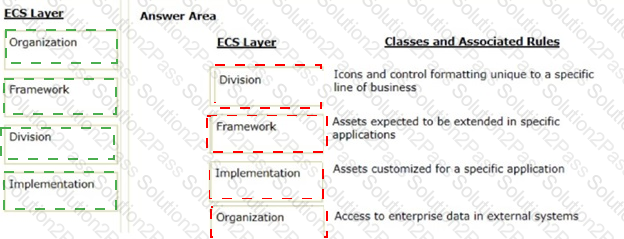
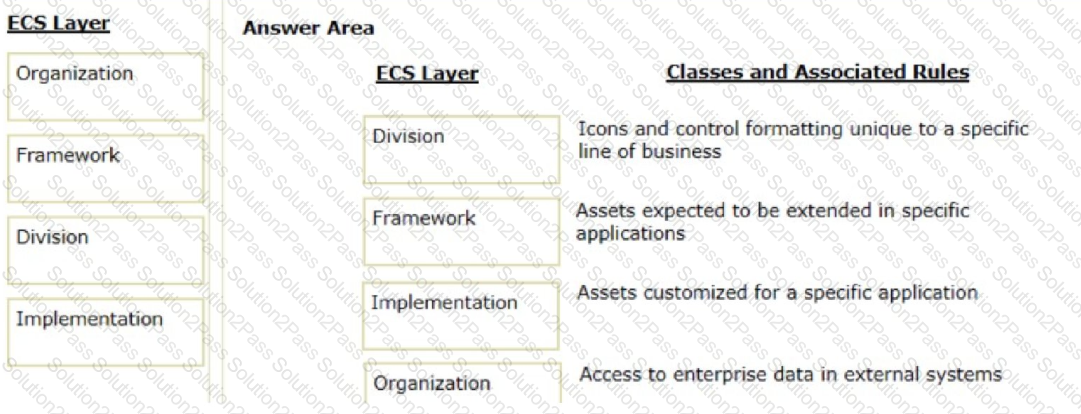
Organize the classes and associated rules in the appropriate Enterprise Class Structure (ECS) layer.
A Pega Platform™ application has just been integrated with an external data source.
Which of the following tests do you perform to ensure that the integration passes data as expected?
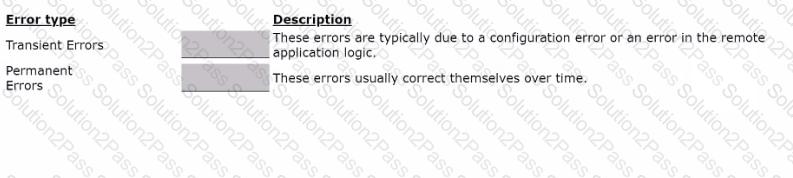
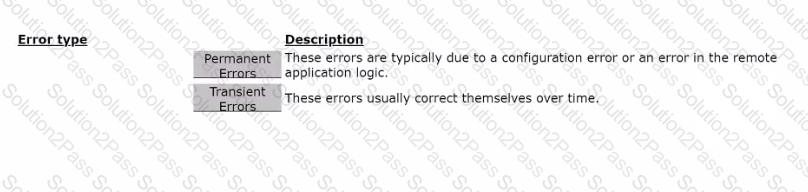
Drag the error type on the left to its description on the right.
You want to create a new minor version of an application ruleset to add a new feature to your application. The new feature will be made available to users in a phased rollout.
How do you update the application to add the new ruleset version?
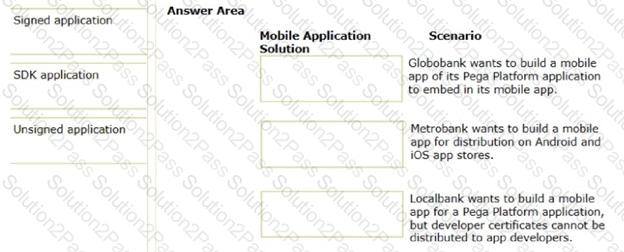
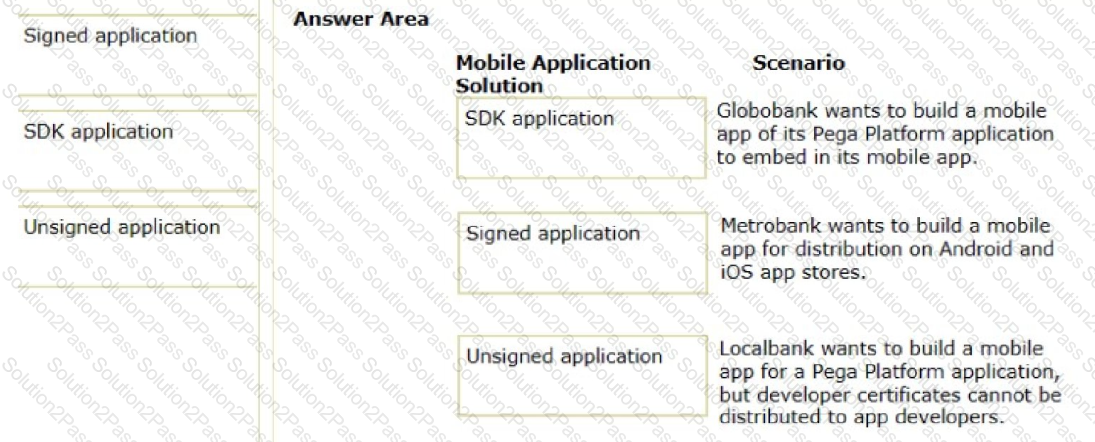
In the Answer Area, drag each mobile application solution on the left to the correct scenario.
An assignment service-level agreement (SLA) is configured with the following details:
♦ Initial urgency: 20
♦ Assignment ready: Timed delay of 1 hour
♦ Goal: 5 hours and increase urgency by 10
♦ Deadline: 8 hours and increase urgency by 20
♦ Passed deadline: 2 hours, increase urgency by 20, and limit events to 5
Assuming no other urgency adjustments, what is the assignment urgency 16 hours after the case reaches the assignment.
Which two situations are likely to negatively impact application performance? (Choose Two)
What is the difference between using the Call and Branch methods in an activity step to invoke other activities?
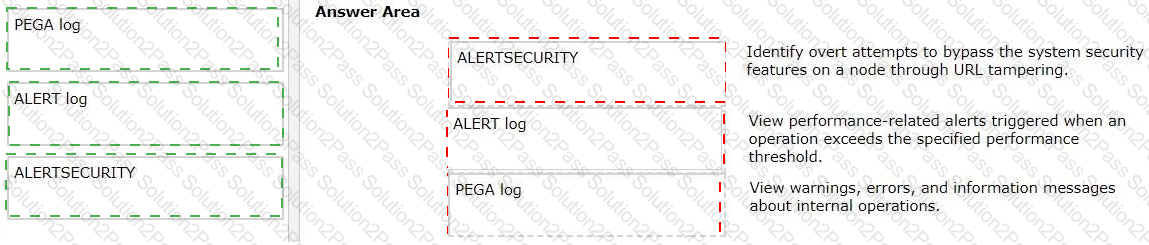
Drag the name of the Pega Platform log file appender from the left to the matching use case on the right.

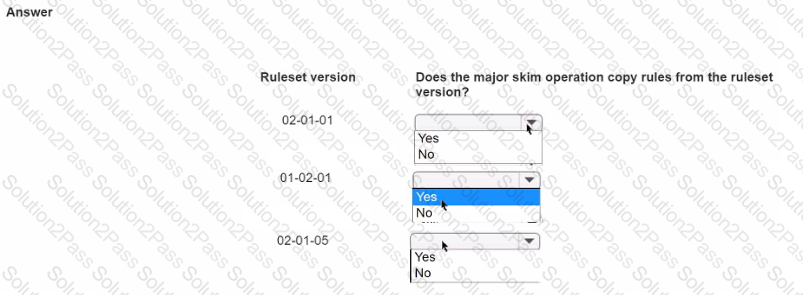
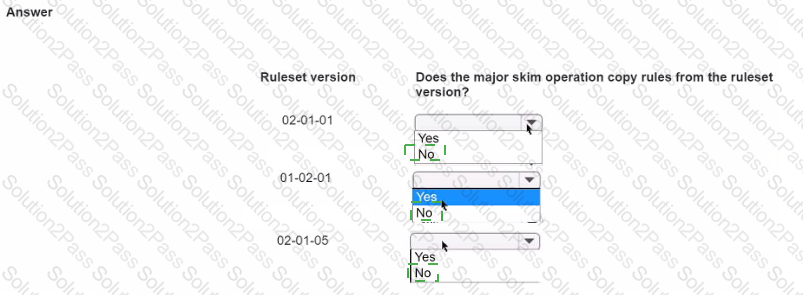
You perform a major skim on the ruleset ABC:02-02-01 to ABC:03-01-01.
In the Answer area, select the ruleset versions that the skim operation uses to copy rules into ABC:03-01-01.
A budgeting application uses a job scheduler to automatically email customers once a week with a breakdown of their weekly expenses. Due to the international usage of the application, stakeholders require peak performance at all hours.
Which solution addresses this performance concern?
Which two configurations can you use to include access groups into your Product rule? (Choose two.)
A medium-size toymaker wants to fulfill orders received during the peak season in December and process the orders in batches multiple times a day.
How do you implement this use case?
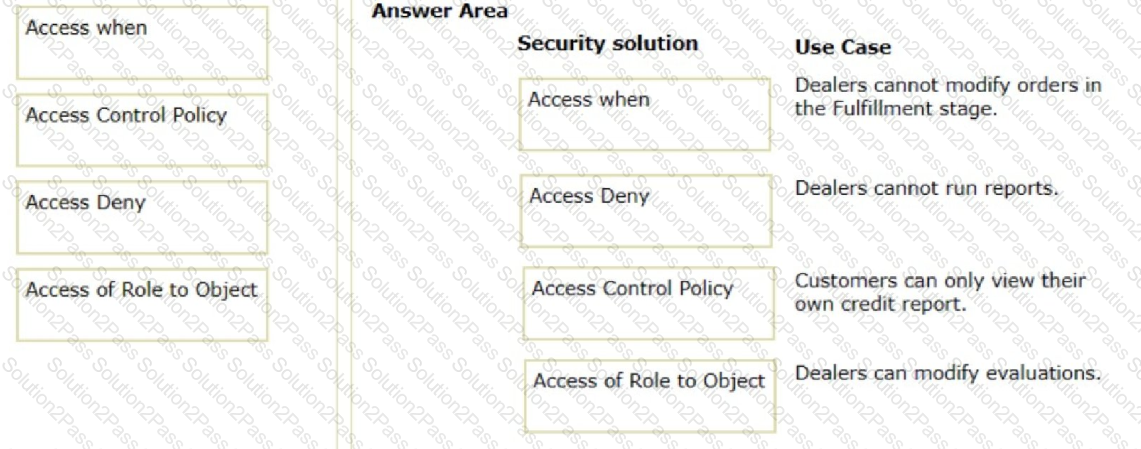
Drag each security solution on the left to its appropriate use case.

In an online shopping application, you enable class-level encryption for the entire case type and optimize First Name, Last Name, Social Security number (SSN), Total Cart, and Account Number properties for reporting.
To secure sensitive data, how do you enable property-level encryption for SSN and Account Number?
A hospital uses a case type to manage the treatment of patients visiting the Emergency Room (ER). Cases are created when the patient checks in at the registration desk, and are resolved when the patient is released from the hospital. Stakeholders identify the following security requirements for the case type.
♦ Patients access cases on a read-only basis.
♦ Patients can only access their own cases.
♦ Doctors and nurses can modify cases throughout the case life cycle.
♦ Only doctors are allowed to write prescriptions.
Which configuration allows doctors and nurses to modify cases while complying with all identified security requirements?
Select the three Pega best practices for developing activities. (Choose Three)
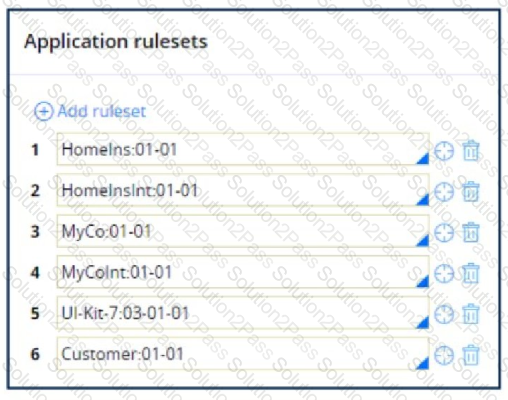
In the following example, the Homelns, Homelnslnt, and Customer rulesets are configured for application validation. MyCo and MyCoInt are configured for ruleset validation. MyCo lists MyCoInt and Customer as its prerequisites, and the prerequisite for MyCoInt is Pega-ProcessCommander.
Which of the following statements is correct?
What is the function of class mapping for reports?
A fitness organization wants to ensure that data is entered correctly into an online form when users apply for, or update, their membership information.
Which scenario requires an edit validate rule?
 Graphical user interface, application
Description automatically generated
Graphical user interface, application
Description automatically generated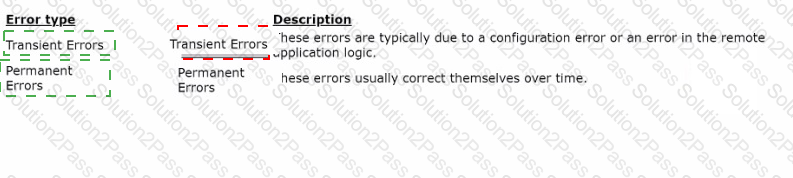
 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg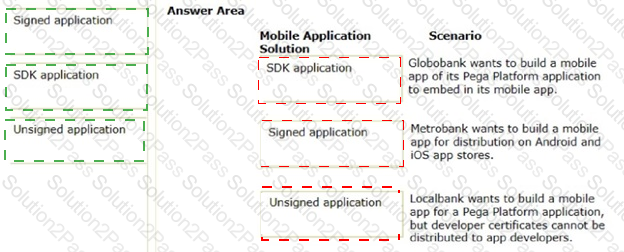

 Graphical user interface
Description automatically generated
Graphical user interface
Description automatically generated