QSSA2018 Qlik Sense System Administrator Certification Exam - June 2018 Release Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Qlik QSSA2018 Qlik Sense System Administrator Certification Exam - June 2018 Release certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A system administrator installs Qlik Sense Enle.pr.se and is tasting the product with a small team of 10 users.
The system administrator completes the following steps in the proxy configuration
* Opens all necessary ports
* Checks in MMC that there is a personal certificate on the server
* Creates a DNS entry (or an easier URL
* Tries to connect with various Internal browsers on different machines including mobile devices
* Adds the page to trusted sites in the Internet configurations
* Installs OpenSSL in the environment
Which steps should the system administrator take lo resolve this issue?
A user reports (hat the Create new app button does NOT consistently appear when logging into the hub The system administrator tries to verify the problem and finds the following
* The user has the correct security rule setup
* The problem can be reproduced in different machines and different browsers
* No error message is related to the user activities in the Qlik Sense logs
* The user can see the Create new app button when directly accessing the central node URL
* The user can NOT see the Create new app button when directly accessing the rim node URL
What is the likely cause of this issue?
A system administrator needs to troubleshoot an issue reported with Qlik Sense. The administrator confirms the following.
* NO hardware issues exist
* NO other process are affecting Qlik Sense
* NO other systems report any issues
* The network team reports optimal performance
The system administrator decides to check the task execution details and token allocations Which two tools should the system administrator use? (Select two )
A system administrator is creating a user directory connector (UDC) for an Active Directory using SSL Which path should the administrator use to configure the UDC?
Which option should the system administrator recommend?
A system administrator creates a new content library to give the developers access to images. The system administrator tests the new library in the Qlik Management Console (QMC) by adding an image into a text image object in an app ion the hub. The developers are unable to see the new content library, but can see the default library.
What should the administrator do to make sure the developer have access to the content library?
Refer to the exhibit.
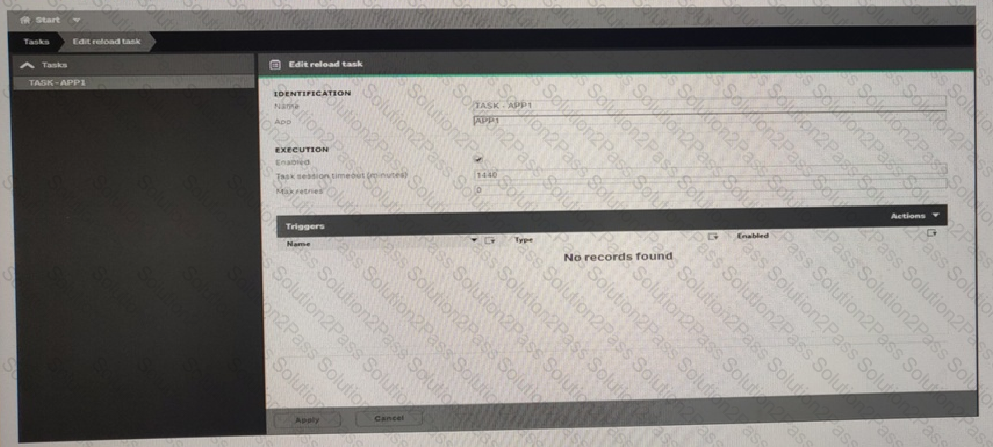
What is the result when the administrator selects the Start button for TASK-APP1 in the Task screen?
A Qlik Sense deployment is planned for 200 users initially. Within a year, the number of users will grow to 2000, with over 100 apps. Most of these users will be the organization’s firewall. There are plans to eventually allows access to some apps to users outside the firewall.
Which two deployment modes will ensure secure access to Qlik Sense apps to users outside the firewall.
Which two deployment models will ensure secure access to Qlik Sense apps by authorized users outside the firewall? (Select two.)
A system administrator needs to set up a solution for mobile device users to access the Qlik Sense hub. The solution must meet several requirements.
* Support IOS devices
* Can be used in remote locations where users do NOT have laptop or desktop computers
* Ability to access Qlik Sense outside the office network without a compatible tunnel solution
* Ability to access Qlik Sense using a secure gateway
What should the system administrator do to meet these requirements?
A company recently experienced a merger and needs to integrate new users into the Qlik Sense environment.
A system administrator must make sure that the system sizing and the tokens match the requirements for all employees in the future.
The system administrator learns the following information.
* 450 active Qlik Sense users before the merger
* 300 new Qlik Sense users
* 500 current token licenses
* Reloads must have the same performance as before the merger
* The number or apps will approximately double
Management request an estimate from the system administrator about server resources and additional license.
Which set of tools should the system administrator use to meet these requirements?
A system Administrator needs to complete the configuration of a Qlik Sense Enterprise environment. The customer solution that needs to access Qlik Sense resources is a JavaScript app which must be authenticated through single sign-on. The customer provides a public key to the system administrator Qlik Sense is expecting an RSA signature with SHA256.
A user needs to update a published app in the Finance stream. After the changes have been made, the needs to be moved to the Accounting stream. The user only has access to a laptop running windows 7(32-bit). The owner of all published apps is the sa_repository user.
Which steps should a system administrator take to efficiently complete this task?
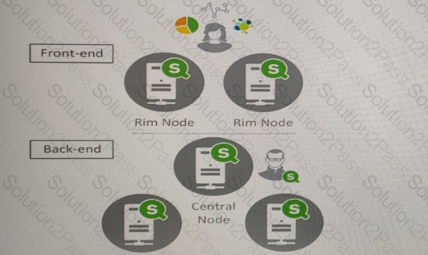
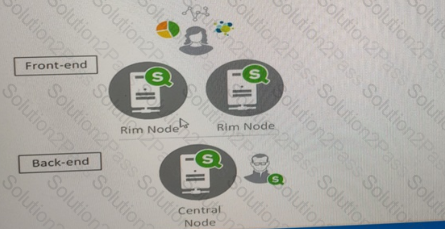
A system administrator must design a Qlik Sense server architecture that meets the following requirements
* Approximately 1000 users will be using apps
* Apps are reloaded outside of office hours
* The total size of data in all apps will be approximately 600 million rows
* Apps must be available 24/7
Which architecture meets these requirements in the most cost efficient way?
A)
B)
C)

D)
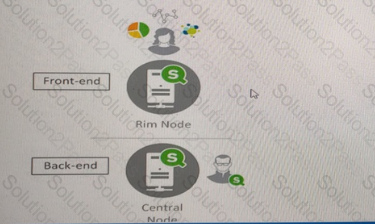
Refer to the exhibit.
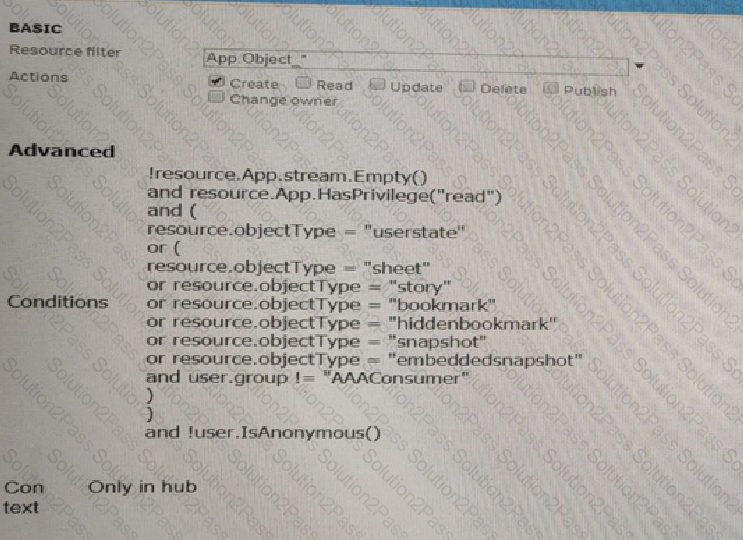
A system administrator creates the security rule shown No other custom security rules exist
What effect will the security rule have when applied to a user?
Refer to the exhibit.
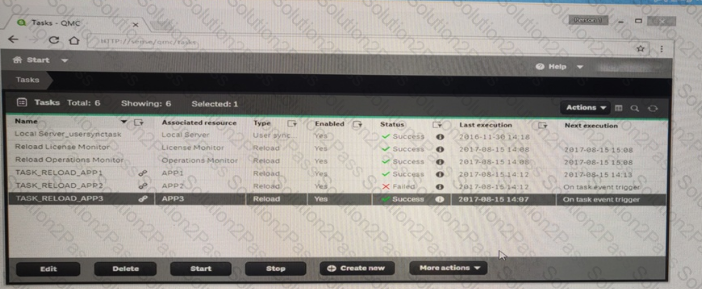
A contentAdmin user discover TASK_RELOAD_APP2 fails.The user double cliks the Failed task to open the Edit reload task screen. There are NO isse found in the Edit reload task screen. The user opens the Operations Monitor app, and the finds an error message in the Details sheet.
Message from reloadprovider: Reload Failed in Engine. Check Engine or script logs
The Engine log did NOT provide any reason for the failure?
Which is the most efficient methods to the cause of this issue?
