EX407 RedHat Red Hat Certified Specialist in Ansible Automation exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your RedHat EX407 Red Hat Certified Specialist in Ansible Automation exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Install and configure ansible
User bob has been created on your control node. Give him the appropriate permissions on the control node. Install the necessary packages to run ansible on the control node.
Create a configuration file /home/bob/ansible/ansible.cfg to meet the following requirements:
• The roles path should include /home/bob/ansible/roles, as well as any other path that may be required for the course of the sample exam.
• The inventory file path is /home/bob/ansible/inventory.
• Ansible should be able to manage 10 hosts at a single time.
• Ansible should connect to all managed nodes using the bob user.
Create an inventory file for the following five nodes:
nodel.example.com
node2.example.com
node3.example.com
node4.example.com
node5.example.com
Configure these nodes to be in an inventory file where node1 is a member of group dev. nodc2 is a member of group test, nodc3 is a member of group proxy, nodc4 and node 5 are members of group prod. Also, prod is a member of group webservers.
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Create a role called apache in "/home/admin/ansible/roles" with the following
requirements:
--> The httpd package is installed, enabled on boot, and started.
--> The firewall is enabled and running with a rule to allow access to the web server.
--> template file index.html.j2 is used to create the file /var/www/html/index.html
with the output:
Welcome to HOSTNAME on IPADDRESS
--> Where HOSTNAME is the fqdn of the managed node and IPADDRESS is the IP-Address of
the managed node.
note: you have to create index.html.j2 file.
--> Create a playbook called httpd.yml that uses this role and the playbook runs on
hosts in the webservers host group.
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Create user accounts
------------------------
--> A list of users to be created can be found in the file called user_list.yml
which you should download from http://classroom.example.com/user_list.yml and
save to /home/admin/ansible/
--> Using the password vault created elsewhere in this exam, create a playbook called
create_user.yml
that creates user accounts as follows:
--> Users with a job description of developer should be:
--> created on managed nodes in the "dev" and "test" host groups assigned the
password from the "dev_pass"
variable and these user should be member of supplementary group "devops".
--> Users with a job description of manager should be:
--> created on managed nodes in the "prod" host group assigned the password from
the "mgr_pass" variable
and these user should be member of supplementary group "opsmgr"
--> Passwords should use the "SHA512" hash format. Your playbook should work using
the vault password file
created elsewhere in this exam.
while practising you to create these file hear. But in exam have to download as per
questation.
user_list.yml file consist:
---
user:
- name: user1
job: developer
- name: user2
job: manager
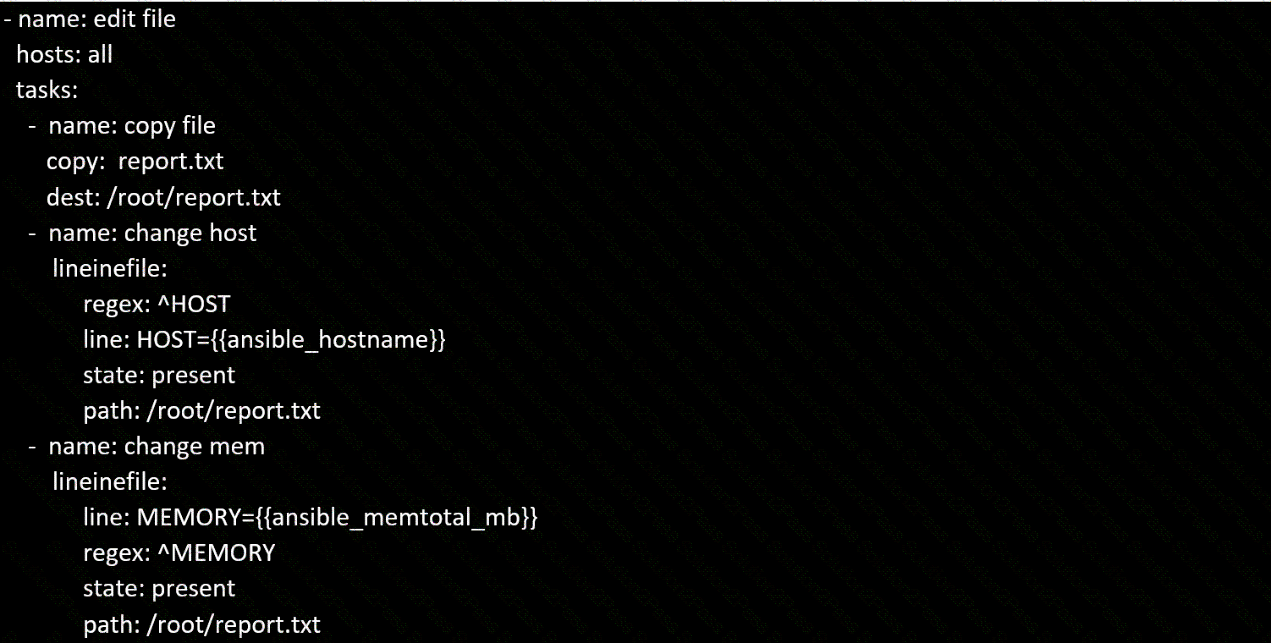
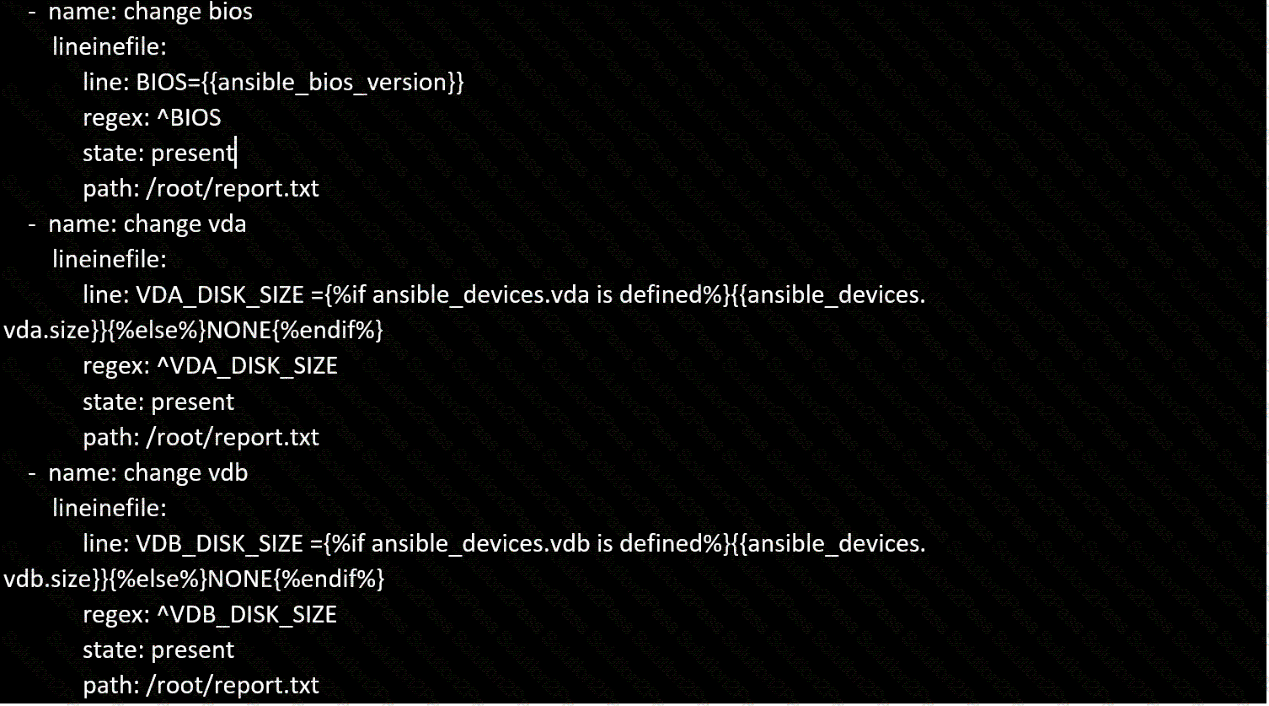
Create a file in /home/sandy/ansible/ called report.yml. Using this playbook, get a file called report.txt (make it look exactly as below). Copy this file over to all remote hosts at /root/report.txt. Then edit the lines in the file to provide the real information of the hosts. If a disk does not exist then write NONE.

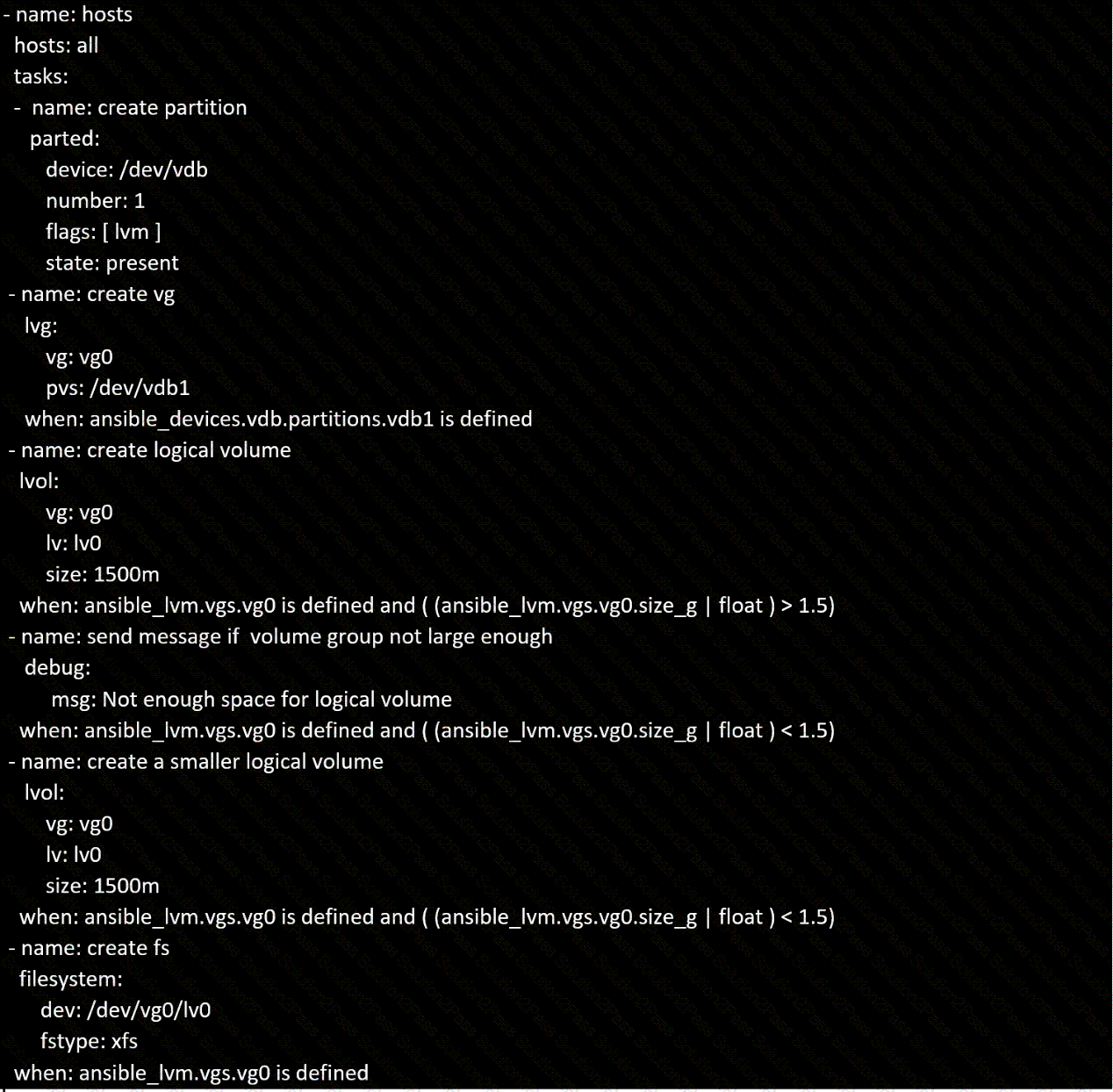
In /home/sandy/ansible/ create a playbook called logvol.yml. In the play create a logical volume called Iv0 and make it of size 1500MiB on volume group vgO If there is not enough space in the volume group print a message "Not enough space for logical volume" and then make a 800MiB Iv0 instead. If the volume group still doesn't exist, create a message "Volume group doesn't exist" Create an xfs filesystem on all Iv0 logical volumes. Don't mount the logical volume.
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Modify file content.
------------------------
Create a playbook called /home/admin/ansible/modify.yml as follows:
* The playbook runs on all inventory hosts
* The playbook replaces the contents of /etc/issue with a single line of text as
follows:
--> On hosts in the dev host group, the line reads: “Development”
--> On hosts in the test host group, the line reads: “Test”
--> On hosts in the prod host group, the line reads: “Production”
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Create and run an Ansible ad-hoc command.
--> As a system administrator, you will need to install software on the managed
nodes.
--> Create a shell script called yum-pack.sh that runs an Ansible ad-hoc command to
create yum-repository on each of the managed nodes as follows:
--> repository1
-----------
1. The name of the repository is EX407
2. The description is "Ex407 Description"
3. The base URL is http://content.example.com/rhel8.0/x86_64/dvd/BaseOS/
4. GPG signature checking is enabled
5. The GPG key URL is http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEYredhat-
release
6. The repository is enabled
--> repository2
-----------
1. The name of the repository is EXX407
2. The description is "Exx407 Description"
3. The base URL is http://content.example.com/rhel8.0/x86_64/dvd/AppStream/
4. GPG signature checking is enabled
5. The GPG key URL is http://content.example.com/rhel8.0/x86_64/dvd/ RPM-GPG-KEYredhat-
release
6. The repository is enabled
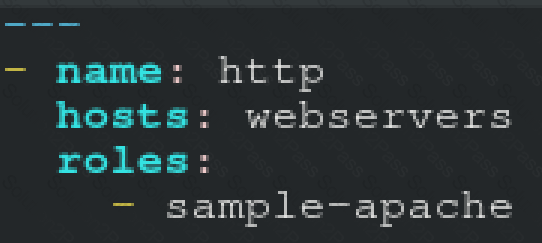
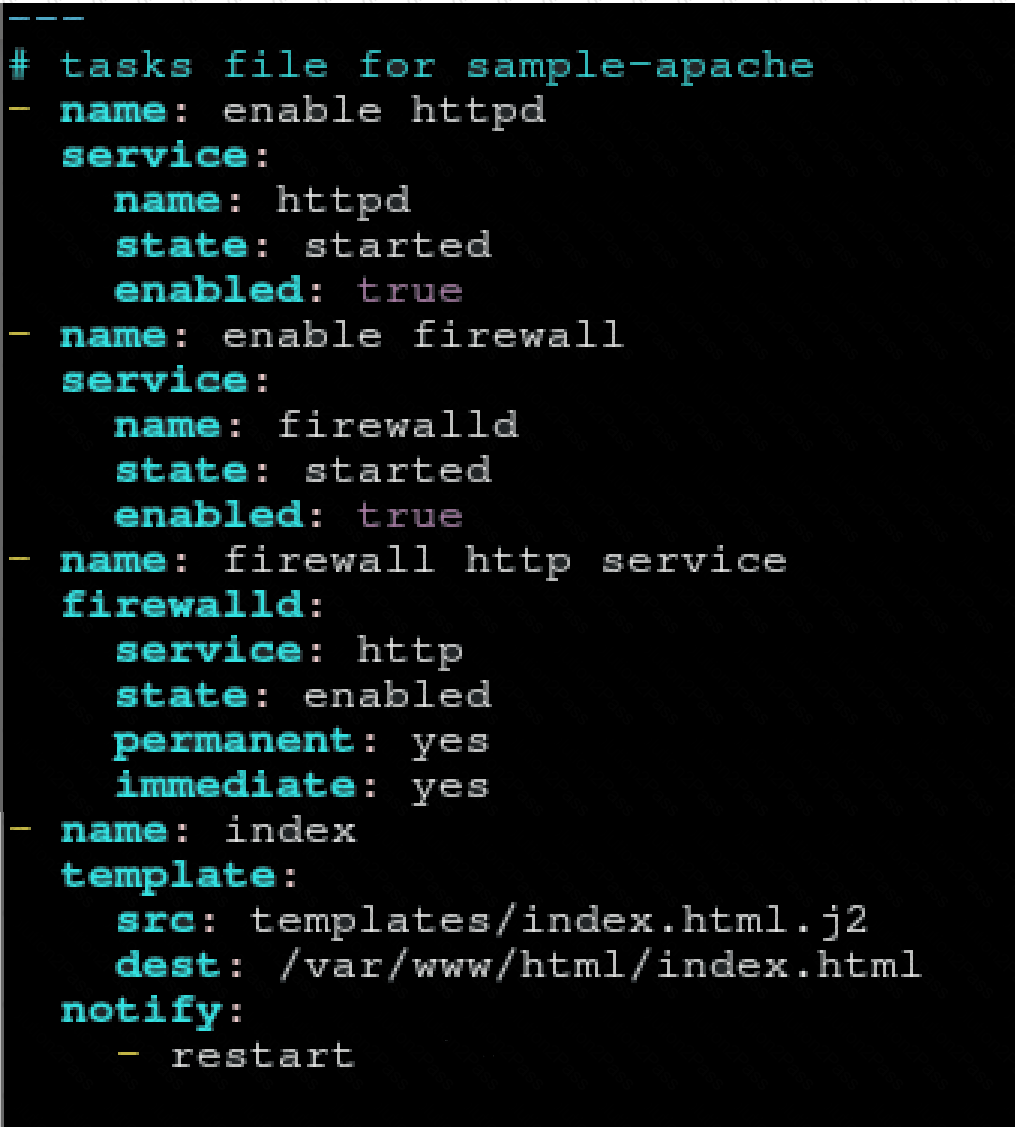
Create a role called sample-apache and store it in /home/bob/ansible/roles. The role should
satisfy the following requirements:
*In the role, install and enable httpd. Also enable the firewall to allow http. Also run the template
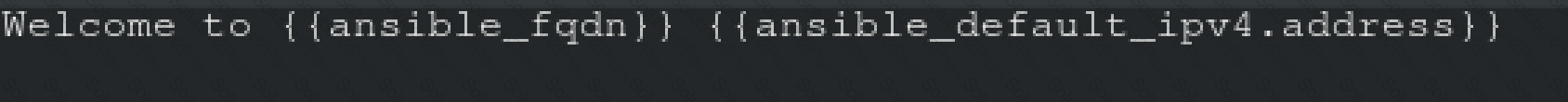
*index.html.j2 and make sure this runs Create a template index.html.j2 that displays "Welcome to the server HOSTNAME"
In a play called apache.yml in /home/bob/ansible/ run the sample-apache role.
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Create a playbook called balance.yml as follows:
* The playbook contains a play that runs on hosts in balancers host group and uses
the balancer role.
--> This role configures a service to loadbalance webserver requests between hosts
in the webservers host group.curl
--> When implemented, browsing to hosts in the balancers host group (for example
http://node5.example.com) should produce the following output:
Welcome to node3.example.com on 192.168.10.z
--> Reloading the browser should return output from the alternate web server:
Welcome to node4.example.com on 192.168.10.a
* The playbook contains a play that runs on hosts in webservers host group and uses
the phphello role.
--> When implemented, browsing to hosts in the webservers host group with the URL /
hello.php should produce the following output:
Hello PHP World from FQDN
--> where FQDN is the fully qualified domain name of the host. For example,
browsing to http://node3.example.com/hello.php, should produce the following output:
Hello PHP World from node3.example.com
* Similarly, browsing to http://node4.example.com/hello.php, should produce the
following output:
Hello PHP World from node4.example.com
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Rekey an existing Ansible vault as follows:
-----------------------------------------------
* Download Ansible vault from http:// classroom.example.com /secret.yml to /home/
admin/ansible/
* The current vault password is curabete
* The new vault password is newvare
* The vault remains in an encrypted state with the new password
Create a file called mysecret.yml on the control host using ansible vault in home/bob/ansible. Set the password to 'notasafepass' and inside the file create a variable called dev_pass with the value of devops. Save the file. Then go back in the file and change dev_pass value to devops123. Then change the vault password of mysecret.yml to verysafepass
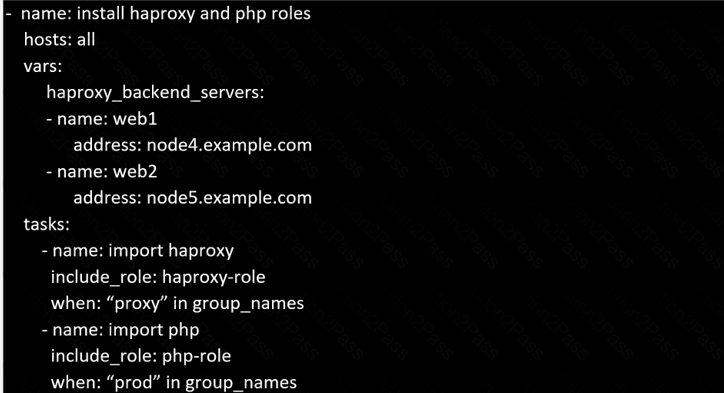
Create a file called requirements.yml in /home/sandy/ansible/roles a file called role.yml in /home/sandy/ansible/. The haproxy-role should be used on the proxy host. And when you curl http://node3.example.com it should display "Welcome to node4.example.com" and when you curl again "Welcome to node5.example.com" The php-role should be used on the prod host.