299-01 Riverbed Certified Solutions Professional - Network Performance Management Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Riverbed 299-01 Riverbed Certified Solutions Professional - Network Performance Management certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following configuration changes can be used to reduce the number of alerts generated overall for a Service?
On Cascade Profiler, in terms of retention of completed reports and reporting sources (one minute flow and rollup files), which of the following is true? (Select 4)
What do you need to configure on the Profiler to detect utilization for an interface?
A SPAN port or Port Mirror differs from RSPAN technology in which way:
Which of the following metrics can Cascade Profiler create dependency (Connection Graphs) for? (Select 3)
Cascade Profiler's Switch Integration feature uses SNMP and adds the capability for Cascade to report on which of the followinG. (Select 2)
When working with capture job traces on a Cascade Shark appliance from Cascade Pilot:
If a VLAN SPAN (VLAN101) is configured and monitored by Cascade Shark, which of the following is true? (Select 2)
In this scenario, you have created a host group called My_Computers on Cascade Profiler. In that group you have included the subnet 192.168.1.0/25.
You have 10 devices in that group 192.168.1.1-10. The rest of the addresses are unused. While running reports on this segment of the network you notice that when a report is run using the entire subnet you see traffic destined for 192.168.1.120. When you run the same report specifying the host group the traffic does not appear. Why is this happening?
How do Cascade Performance Analytics assist with Performance Monitoring?
Within Cascade Pilot a Watch can: (Select 3)
Which version of SNMP traps can the Cascade Profiler and Cascade Express send?
Trace clips in Cascade Pilot allow you to:
A system administrator needs to update their Cascade Profiler host group settings to remove references to a decommissioned office on the 10.63.32.0/24 subnet.
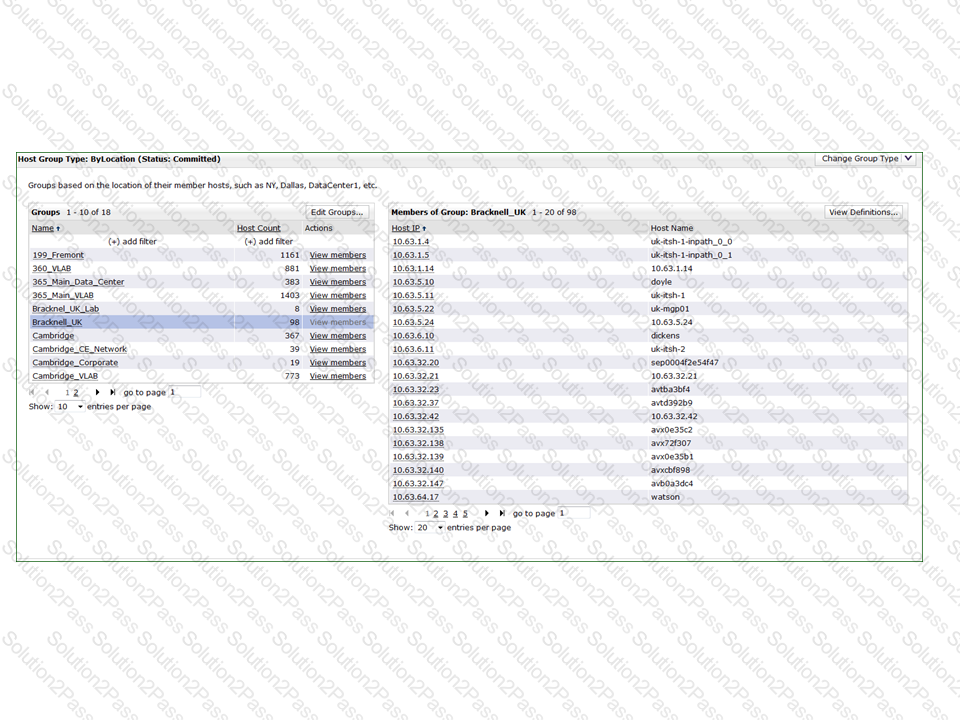
What is the best way to do this?
On the Cascade Shark appliance, packet de-duplication should be enabled when:
Which TCP port is used for Cascade Profiler web based management interfaces?
What is a benefit that Cascade Profiler might provide to Security Operations? (Select 3)
Which parameters can be used to set up an Application Performance analytic on Cascade Profiler?
Some common protocols which may be observed on a network with visibility tools are listed below. Match the protocol name with the most common port used.
1. HTTP a) TCP/25
2. HTTPS b) TCP/445
3. HTTPS through a proxy c) TCP/443
4. SMTP d) TCP/80
5. CIFS e) TCP/8080
In the Cascade Profiler GUI, where can you mark a TCP port as a Server Port?
