CNSP The SecOps Group Certified Network Security Practitioner (CNSP) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your The SecOps Group CNSP Certified Network Security Practitioner (CNSP) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which command will perform a DNS zone transfer of the domain "victim.com" from the nameserver at 10.0.0.1?
What is the response from an open UDP port which is behind a firewall (port is open on the firewall)?
Which of the following is an example of a SUID program?
What types of attacks are phishing, spear phishing, vishing, scareware, and watering hole?
What is the response from an open UDP port which is not behind a firewall?
Where are the password hashes stored in a Microsoft Windows 64-bit system?
Which of the following files has the SUID permission set?
-rwxr-sr-x 1 root root 4096 Jan 1 00:00 myfile
-rwsr-xr-x 1 root root 4896 Jan 1 08:00 myprogram
-rw-r--r-s 1 root root 4096 Jan 1 00:00 anotherfile
What user account is required to create a Golden Ticket in Active Directory?
In the context of a Unix-based system, where does a daemon process execute in the memory?
Which of the aforementioned SSL/TLS protocols are considered to be unsafe?
Where is the system registry file stored in a Microsoft Windows Operating System?
Which of the following attacks are associated with an ICMP protocol?
Where are the password hashes stored in the Linux file system?
Which of the following techniques can be used to bypass network segmentation during infrastructure penetration testing?
Which of the following files has the SGID permission set?
-rwxr-sr-x 1 root root 4096 Jan 1 08:00 myfile
-rwsr-xr-x 1 root root 4096 Jan 1 00:08 myprogram
-rw-r--r-s 1 root root 4896 Jan 1 00:00 anotherfile
Which one of the following is a phishing email?
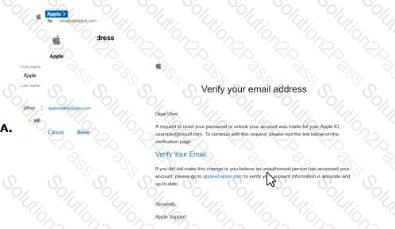
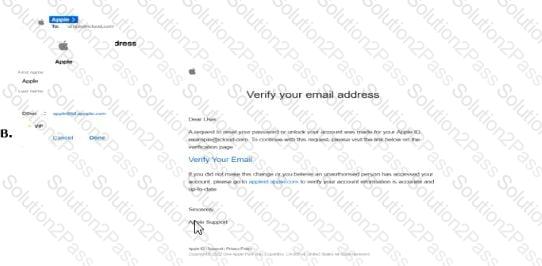
What is the response from a closed UDP port which is not behind a firewall?
The Management Information Base (MIB) is a collection of object groups that is managed by which service?
