Essentials WatchGuard Fireware Essentials Exam Free Practice Exam Questions (2025 Updated)
Prepare effectively for your WatchGuard Essentials Fireware Essentials Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
When you configure the Global Application Control action, it is automatically applied to all policies.
An email newsletter about sales from an external company is sometimes blocked by spamBlocker. What option could you choose to make sure the newsletter is delivered to your users? (Select one.)
How can you include log messages from more than one Firebox in a single report generated by Dimension? (Select two.)
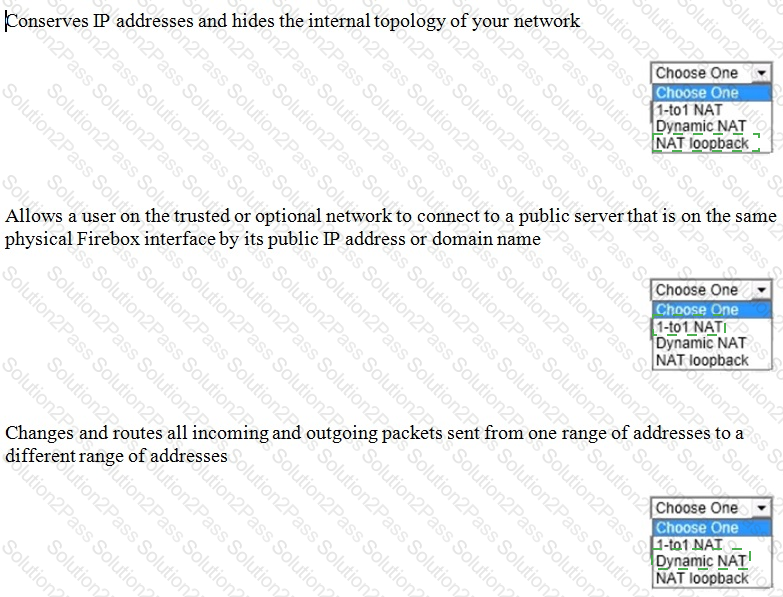
Match each type of NAT with the correct description:
When your users connect to the Authentication Portal page to authenticate, they see a security warning message in their browses, which they must accept before they can authenticate. How can you make sure they do not see this security warning message in their browsers? (Select one.)
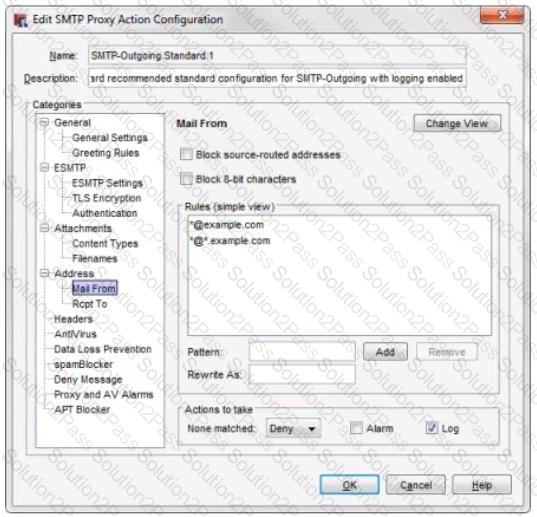
From the SMTP proxy action settings in this image, which of these options is configured for outgoing SMTP traffic? (Select one.)
You have a privately addressed email server behind your Firebox. If you want to make sure that all traffic from this server to the Internet appears to come from the public IP address 203.0.113.25, regardless of policies, which from of NAT would you use? (Select one.)
Which policies can use the Intrusion Prevention Service to block network attacks? (Select one?)
If you use an external authentication server for mobile VPN, which option must you complete before remote users can authenticate? (Select one.)
Which diagnostic tasks can you run from the Traffic Monitor tab of Firebox System Manager? (Select four.)
Which of these threats can the Firebox prevent with the default packet handling settings? (Select four.)
Which of these actions adds a host to the temporary or permanent blocked sites list? (Select three.)
Which takes precedence: WebBlocker category match or a WebBlocker exception?
How can you prevent connections to the Fireware Web UI from computers on optional interface Eth2? (Select one.)
To enable remote devices to send log messages to Dimension through the gateway Firebox, what must you verify is included in your gateway Firebox configuration? (Select one.)
What settings must you device configuration file include for Gateway AntiVirus to protect users on your network? (Select two.)
Your company denies downloads of executable files from all websites. What can you do to allow users on the network to download executable files from the company’s remote website? (Select one.)
Which of these options must you configure in an HTTPS-proxy policy to detect credit card numbers in HTTP traffic that is encrypted with SSL? (Select two.)