CBSP Blockchain BTA Certified Blockchain Security Professional Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Blockchain CBSP BTA Certified Blockchain Security Professional certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following attacks were enabled by design decisions made by the blockchain's developers? Select all that apply
The code of smart contracts that are "self-destructed" is no longer visible to the blockchain network
The List hack demonstrated that biockchains using short addresses are exploitable
Which of the following are necessary properties for a cryptographic hash function to be secure? Select all that apply
Multisignatures are designed to allow a set of users to make a valid transaction only if a set minimum number of them consent
Which of the following blockchains is designed to allow multiple blockchains to run on the same network?
Which of the following is NOT an essential part of Confidential Transactions?
Which of the following blockchains does NOT use broadcast communications?
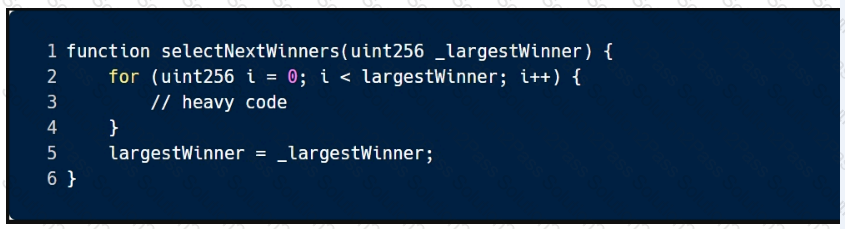
This sample code is vulnerable to which of the following attacks?
In which blockchain consensus algorithm does a user pay (give up coin forever) to participate in consensus?
Determining if a transaction is part of the distributed ledger is less computationally intensive in DAG-based solutions than in blockchain
All smart contracts are audited for correctness and checked for malicious code before being uploaded to the blockchain.
Compromising blockchain accounts is beneficial to which of the following types ot attacks?
Using public keys tor identity management helps blockchain technology achieve which of the following?
Which smart contract auditing strategy involves graphing how the code executes and looks for anomalies?
The goal of most network-based blockchain attacks is to enable what type of attack?
Which of the following are shared benefits of private and permissioned blockchain architectures? Select all that apply.
A major advantage of a stale channel is that it provides a permanent means of transferring value between two parties.
Transaction validation on DAG-based DLTs is designed in a way that allows legitimate transactions to be considered untrusted due to random chance.
A controversial update to blockchain functionality could increase the vulnerability of the blockchain to attack
