CFR-410 CertNexus CyberSec First Responder (CFR) Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CertNexus CFR-410 CyberSec First Responder (CFR) Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A company website was hacked via the following SQL query:
email, passwd, login_id, full_name FROM members
WHERE email = “attacker@somewhere.com”; DROP TABLE members; –”
Which of the following did the hackers perform?
A security analyst has discovered that an application has failed to run. Which of the following is the tool MOST
likely used by the analyst for the initial discovery?
As part of an organization’s regular maintenance activities, a security engineer visits the Internet Storm Center advisory page to obtain the latest list of blacklisted host/network addresses. The security engineer does this to perform which of the following activities?
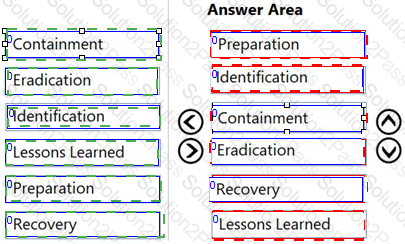
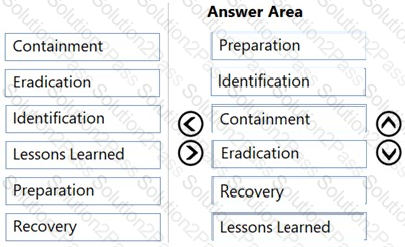
What is the correct order of the DFIR phases?
What is the primary purpose of the "information security incident triage and processing function" in the (CSIRT) Computer Security Incident Response Team Services Framework?
Which of the following, when exposed together, constitutes PII? (Choose two.)
A common formula used to calculate risk is:+ Threats + Vulnerabilities = Risk. Which of the following represents the missing factor in this formula?
A system administrator has been tasked with developing highly detailed instructions for patching managed assets using the corporate patch management solution. These instructions are an example of which of the following?
Which of the following does the command nmap –open 10.10.10.3 do?
A digital forensics investigation requires analysis of a compromised system's physical memory. Which of the following tools should the forensics analyst use to complete this task?
Which of the following regulations is most applicable to a public utility provider operating in the United States?
After successfully enumerating the target, the hacker determines that the victim is using a firewall. Which of the following techniques would allow the hacker to bypass the intrusion prevention system (IPS)?
Which of the following methods are used by attackers to find new ransomware victims? (Choose two.)
Which of the following digital forensic goals is being provided with hashing and time-stamping of the electronic evidence?