156-215.81 Checkpoint Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Checkpoint 156-215.81 Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Full synchronization between cluster members is handled by Firewall Kernel. Which port is used for this?
What is the difference between SSL VPN and IPSec VPN?
Fill in the blank: Once a certificate is revoked from the Security GateWay by the Security Management Server, the certificate information is _______.
Name one limitation of using Security Zones in the network?
When changes are made to a Rule base, it is important to _______________ to enforce changes.
R80 is supported by which of the following operating systems:
When connected to the Check Point R80 Management Server using the SmartConsole the first administrator to connect has a lock on:
You can see the following graphic:
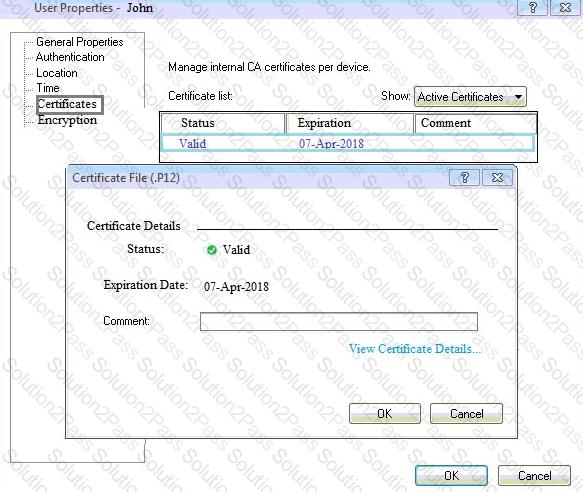
What is presented on it?
What is the default shell of Gaia CLI?
Identity Awareness lets an administrator easily configure network access and auditing based on three items Choose the correct statement.
Which statement is NOT TRUE about Delta synchronization?
What is the default shell for the command line interface?
To quickly review when Threat Prevention signatures were last updated, which Threat Tool would an administrator use?
Which of the following is NOT a role of the SmartCenter:
Choose what BEST describes a Session
Gaia includes Check Point Upgrade Service Engine (CPUSE), which can directly receive updates for what components?
Which of the following situations would not require a new license to be generated and installed?
Which type of Endpoint Identity Agent includes packet tagging and computer authentication?
What is the purpose of Captive Portal?
In which scenario will an administrator need to manually define Proxy ARP?
