156-315.81 Checkpoint Check Point Certified Security Expert R81.20 ( 156-315.81.20 ) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Checkpoint 156-315.81 Check Point Certified Security Expert R81.20 ( 156-315.81.20 ) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
True or False: In a Distributed Environment, a Central License can be installed via CLI on a Security Gateway.
An established connection is going to www.google.com. The Application Control Blade Is inspecting the traffic. If SecureXL and CoreXL are both enabled, which path is handling the traffic?
You plan to automate creating new objects using new R81 Management API. You decide to use GAIA CLI for this task.
What is the first step to run management API commands on GAIA’s shell?
What should the admin do in case the Primary Management Server is temporary down?
The back-end database for Check Point R81 Management uses:
DLP and Geo Policy are examples of what type of Policy?
What is the recommended way to have a redundant Sync connection between the cluster nodes?
In the R81 SmartConsole, on which tab are Permissions and Administrators defined?
Alice works for a big security outsourcing provider company and as she receives a lot of change requests per day she wants to use for scripting daily (asks the API services from Check Point fof the Management API. Firstly she needs to be aware if the API services are running for the management. Which of the following Check Point Command is true:
The “MAC magic” value must be modified under the following condition:
Check Point ClusterXL Active/Active deployment is used when:
Which Check Point daemon invokes and monitors critical processes and attempts to restart them if they fail?
By default, which port does the WebUI listen on?
Choose the correct syntax to add a new host named “emailserver1” with IP address 10.50.23.90 using GAiA Management CLI?
You have enabled “Full Log” as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
In R81.20 a new feature dynamic log distribution was added. What is this for?
Configure the Security Gateway to distribute logs between multiple active Log Servers to support a better rate of Logs and Log Servers redundancy
In case of a Management High Availability the management server stores the logs dynamically on the member with the most available disk space in /var/log
Synchronize the log between the primary and secondary management server in case of a Management High Availability
What is the minimum number of CPU cores required to enable CoreXL?
The Check Point installation history feature in provides the following:
Packet acceleration (SecureXL) identities connections by several attributes. Which of the attributes is NOT used for identifying connection?
What are types of Check Point APIs available currently as part of R81.20 code?
Using fw monitor you see the following inspection point notion E and i what does that mean?
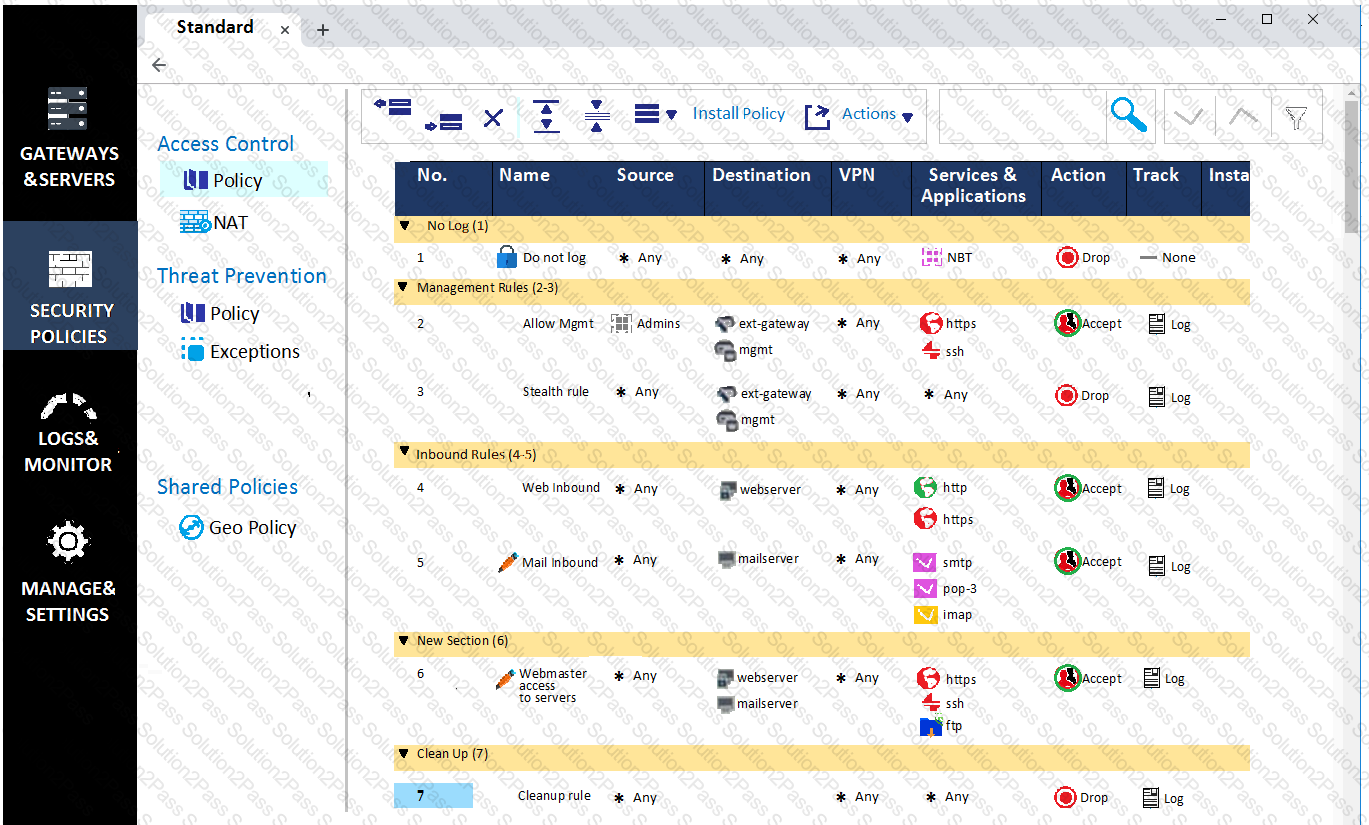
What can we infer about the recent changes made to the Rule Base?
What is the purpose of the command "ps aux | grep twd"?
After verifying that API Server is not running, how can you start the API Server?
Installations and upgrades with CPUSE require that the CPUSE agent is up-to-date. Usually the latest build is downloaded automatically. How can you verify the CPUSE agent build?
The “Hit count” feature allows tracking the number of connections that each rule matches. Will the Hit count feature work independently from logging and Track the hits if the Track option is set to “None”?
What is the correct order of the default “fw monitor” inspection points?
When using the Mail Transfer Agent, where are the debug logs stored?
Check Point Support in many cases asks you for a configuration summary of your Check Point system. This is also called:
CPM process stores objects, policies, users, administrators, licenses and management data in a database. The database is:
