156-315.81 Checkpoint Check Point Certified Security Expert R81.20 ( 156-315.81.20 ) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Checkpoint 156-315.81 Check Point Certified Security Expert R81.20 ( 156-315.81.20 ) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Where you can see and search records of action done by R81 SmartConsole administrators?
Which command will allow you to see the interface status?
Which features are only supported with R81.20 Gateways but not R77.x?
What are the different command sources that allow you to communicate with the API server?
Which two of these Check Point Protocols are used by SmartEvent Processes?
Fill in the blank: The tool _____ generates a R81 Security Gateway configuration report.
Fill in the blank: The R81 utility fw monitor is used to troubleshoot ______________________.
What command verifies that the API server is responding?
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
How many images are included with Check Point TE appliance in Recommended Mode?
To fully enable Dynamic Dispatcher on a Security Gateway:
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
What is the correct command to observe the Sync traffic in a VRRP environment?
IF the first packet of an UDP session is rejected by a rule definition from within a security policy (not including the clean up rule), what message is sent back through the kernel?
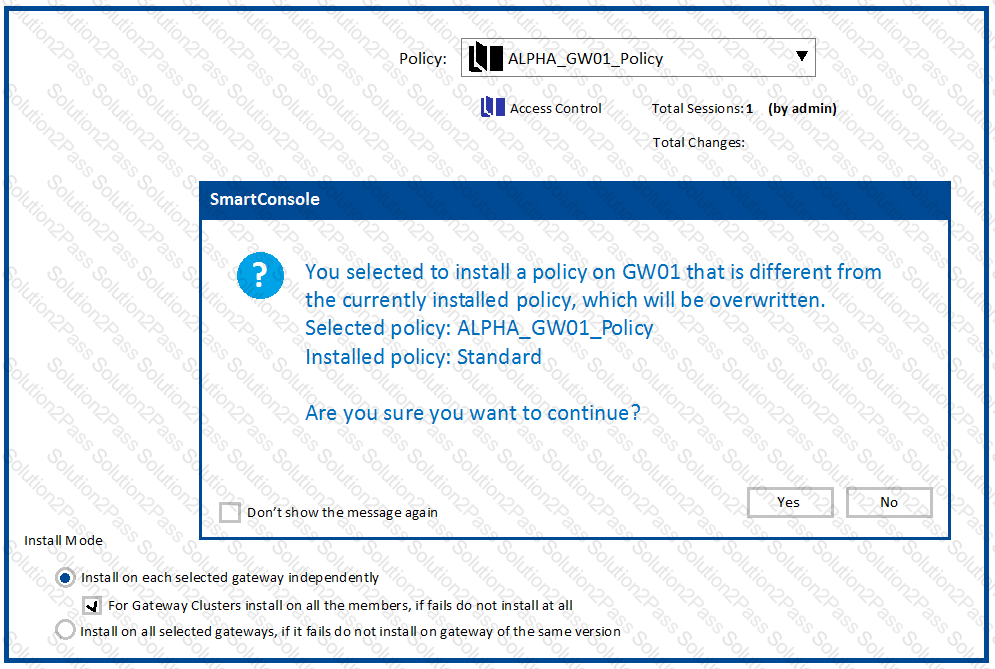
Why would an administrator see the message below?
What is "Accelerated Policy Installation"?
Secure Configuration Verification (SCV), makes sure that remote access client computers are configured in accordance with the enterprise Security Policy. Bob was asked by Alice to implement a specific SCV configuration but therefore Bob needs to edit and configure a specific Check Point file. Which location file and directory is true?
Which of the following is NOT a method used by Identity Awareness for acquiring identity?
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?
What is the command switch to specify the Gaia API context?
Name the authentication method that requires token authenticator.
Which command is used to add users to or from existing roles?
At what point is the Internal Certificate Authority (ICA) created?
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
What is the best sync method in the ClusterXL deployment?
How to can you make sure that the old logs will be available after updating the Management to version R81.20 using the Advanced Upgrade Method?
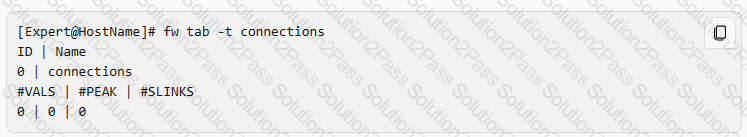
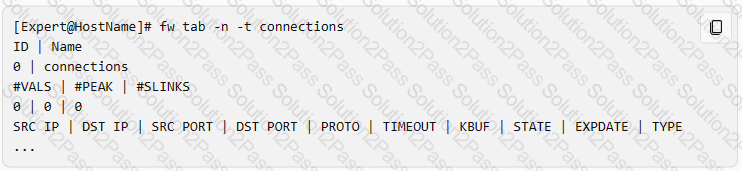
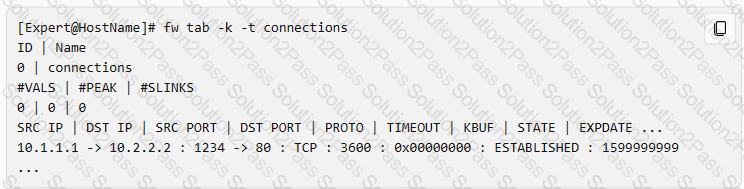
Which command shows only the table names of all kernel tables?
After upgrading the primary security management server from R80.40 to R81.10 Bob wants to use the central deployment in SmartConsole R81.10 for the first time. How many installations (e.g. Jumbo Hotfix, Hotfixes or Upgrade Packages) can run of such at the same time:
If the Active Security Management Server fails or if it becomes necessary to change the Active to Standby, the following steps must be taken to prevent data loss. Providing the Active Security Management Server is responsive, which if these steps should NOT be performed:
What are the Threat Prevention software components available on the Check Point Security Gateway?