200-301 Cisco Certified Network Associate Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 200-301 Cisco Certified Network Associate certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which IP address is used when an administrator must open a web-based management session with a lightweight AP?
What is the main purpose of SSH management access?
All physical cabling is in place. Router R4 and PCI are fully configured and
inaccessible. R4's WAN interfaces use .4 in the last octet for each subnet.
Configurations should ensure that connectivity is established end-to-end.
1 . Configure static routing to ensure RI prefers the path through R2 to
reach only PCI on R4's LAN
2. Configure static routing that ensures traffic sourced from RI will take
an alternate path through R3 to PCI in the event of an outage along
the primary path
3. Configure default routes on RI and R3 to the Internet using the least number of hops
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
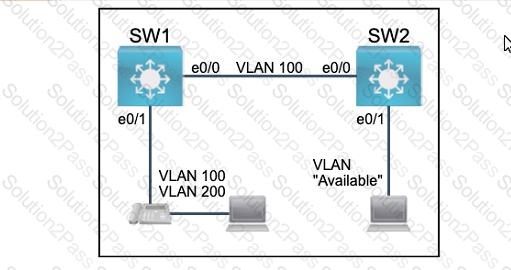
All physical cabling between the two switches is installed. Configure the network connectivity between the switches using the designated VLANs and interfaces.
1. Configure VLAN 100 named Compute and VLAN 200 named Telephony where required for each task.
2. Configure Ethernet0/1 on SW2 to use the existing VLAN named Available.
3. Configure the connection between the switches using access ports.
4. Configure Ethernet0/1 on SW1 using data and voice VLANs.
5. Configure Ethemet0/1 on SW2 so that the Cisco proprietary neighbor discovery protocol is turned off for the designated interface only.
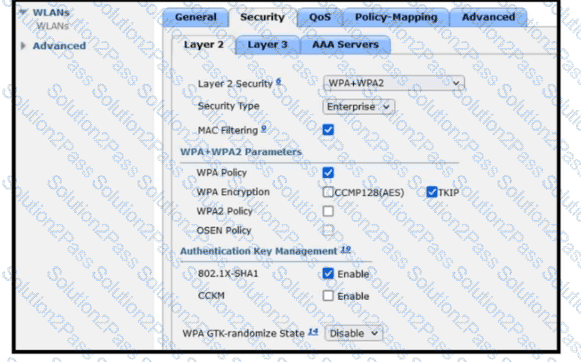
Refer to the exhibit. A guest WLAN must be created that prompts the client for a username and password on the local web page of the WLC. Which two actions must be performed on the Layer 2 tab before enabling the Authentication option on the Layer 3 tab? (Choose two.)
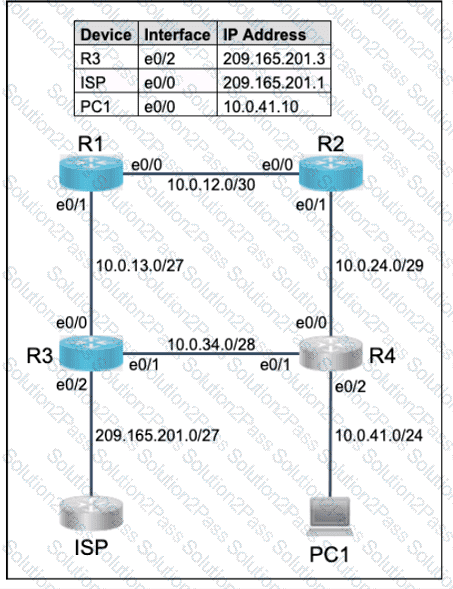
Connectivity between four routers has been established. IP connectivity must be configured in the order presented to complete the implementation. No dynamic routing protocols are included.
1. Configure static routing using host routes to establish connectivity from router R3 to the router R1 Loopback address using the source IP of 209.165.200.230.
2. Configure an IPv4 default route on router R2 destined for router R4.
3. Configure an IPv6 default router on router R2 destined for router R4.

Which interface is used to send traffic to the destination network?
O 10.18.75.113/27 [110/6906] via GO/6
O 10.18.75.113/27 [110/23018] via GO/3
R 10.18.75.113/27 [120/16] via GO/16
R 10.18.75.113/27 [120/14] via GO/23
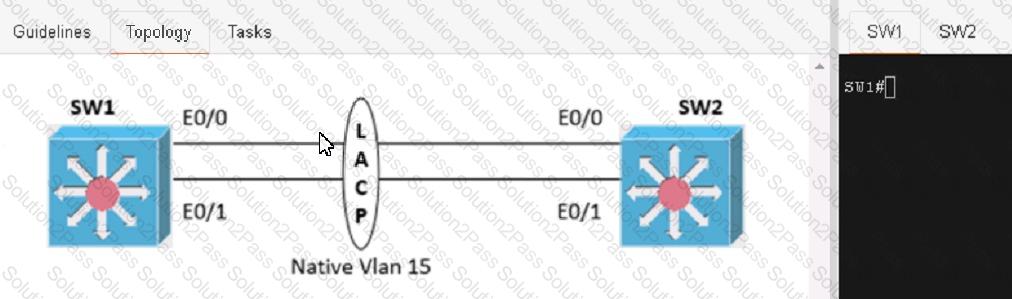
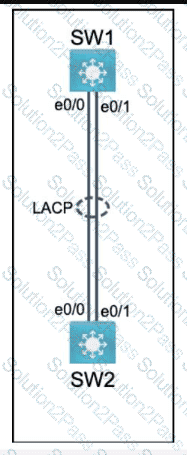
Physical connectivity is implemented between the two Layer 2 switches, and the network connectivity between them must be configured
1. Configure an LACP EtherChannel and number it as 1; configure it between switches SW1 and SVV2 using interfaces Ethernet0/0 and Ethernet0/1 on both sides. The LACP mode must match on both ends
2 Configure the EtherChannel as a trunk link.
3. Configure the trunk link with 802.1 q tags.
4. Configure the native VLAN of the EtherChannel as VLAN 15.
What is a function of a northbound API in an SDN environment?
Aswitch receives a frame with the destination MAC address 3C:5D: 7E:9F: 1A:2B.
Switch# show ethernet-frame-and-mac-address-table
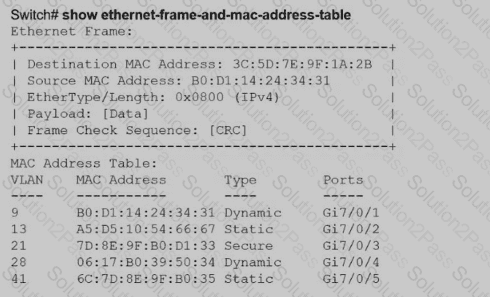
How does the switch handle the frame?
What differentiates the TCP and UDP protocols?
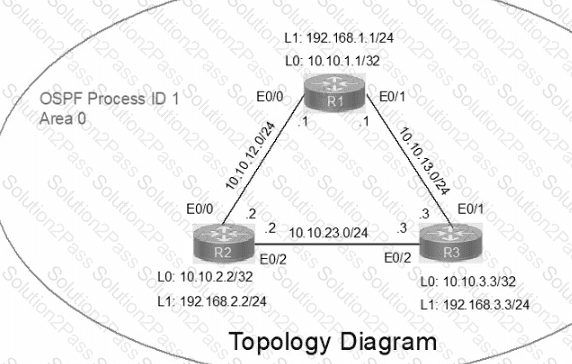
IP connectivity between the three routers is configured. OSPF adjacencies must be established.
1. Configure R1 and R2 Router IDs using the interface IP addresses from the link that is shared between them.
2. Configure the R2 links with a max value facing R1 and R3. R2 must become the DR. R1 and R3 links facing R2 must remain with the default OSPF configuration for DR election. Verify the configuration after clearing the OSPF process.
3. Using a host wildcard mask, configure all three routers to advertise their respective Loopback1 networks.
4. Configure the link between R1 and R3 to disable their ability to add other OSPF routers.
Refer to the exhibit.

What is occurring on this switch?
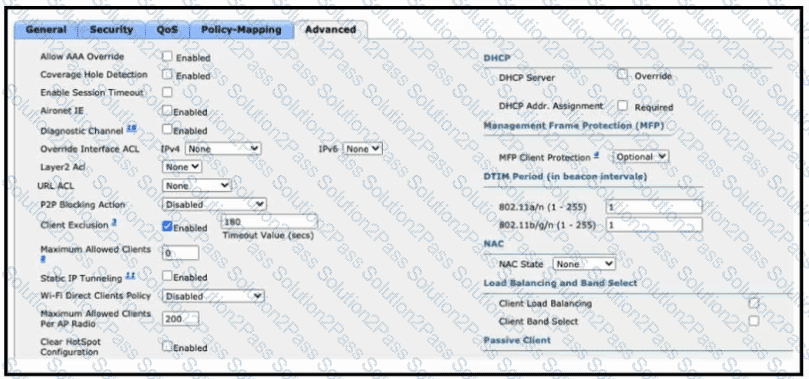
Refer to the exhibit. An administrator is configuring a new WLAN for a wireless network that has these requirements:
Dual-band clients that connect to the WLAN must be directed to the 5-GHz spectrum.
Wireless clients on this WLAN must be able to apply VLAN settings from RADIUS attributes.
Which two actions meet these requirements? (Choose two.)
Why would a network administrator choose to implement RFC 1918 address space?
What is the total number of users permitted to simultaneously browse the controller management pages when using the AireOS GUI?
Which AP mode wirelessly connects two separate network segments each set up within a different campus building?
Which security element uses a combination of one-time passwords, a login name, and a personal smartphone?
Which default condition must be considered when an encrypted mobility tunnel is used between two Cisco WLCs?
Physical connectivity is implemented between the two Layer 2 switches,
and the network connectivity between them must be configured.
I . Configure an LACP EtherChanneI and number it as 44; configure it
between switches SWI and SW2 using interfaces EthernetO/O and
Ethernet0/1 on both sides. The LACP mode must match on both ends.
2. Configure the EtherChanneI as a trunk link.
3. Configure the trunk link with 802. Iq tags.
4. Configure VLAN 'MONITORING' as the untagged VLAN of the
EtherChannel.
==================
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
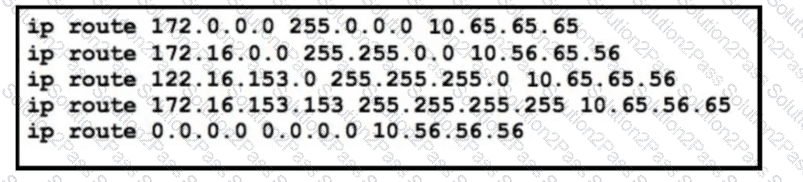
Refer to the exhibit. The static routes were implemented on the border router. What is the next hop IP address for a ping sent to 172.16.153.154 from the border router?
Which key function is provided by the data plane?
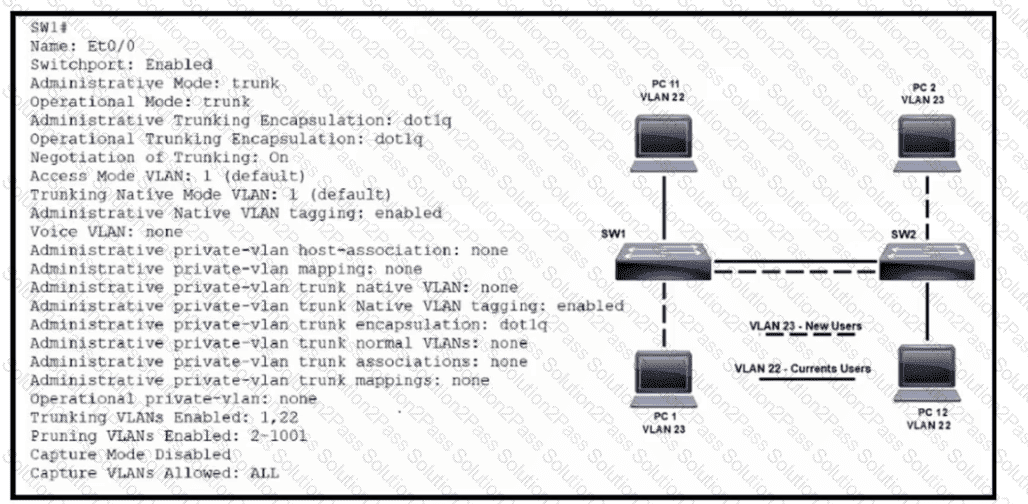
Refer to the exhibit. VLAN 23 is being implemented between SW1 and SW2. The command show interface ethernet0/0 switchport has been issued on SW1. Ethernet0/0 on SW1 is the uplink to SW2. Which command when entered on the uplink interface allows PC 1 and PC 2 to communicate without impact to the communication between PC 11 and PC 12?
What are two benefits of private IPv4 addressing? (Choose two.)
Which header must be included in a REST request from an application that requires JSON-formatted content?
All physical cabling is in place. A company plans to deploy 32 new sites.
The sites will utilize both IPv4 and IPv6 networks.
1 . Subnet 172.25.0.0/16 to meet the subnet requirements and maximize
the number of hosts
Using the second subnet
• Assign the first usable IP address to e0/0 on Sw1O1
• Assign the last usable IP address to e0/0 on Sw102
2. Subnet to meet the subnet requirements and maximize
the number of hosts
c Using the second subnet
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on e0/0 on Sw101
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on eO/O on swi02
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.

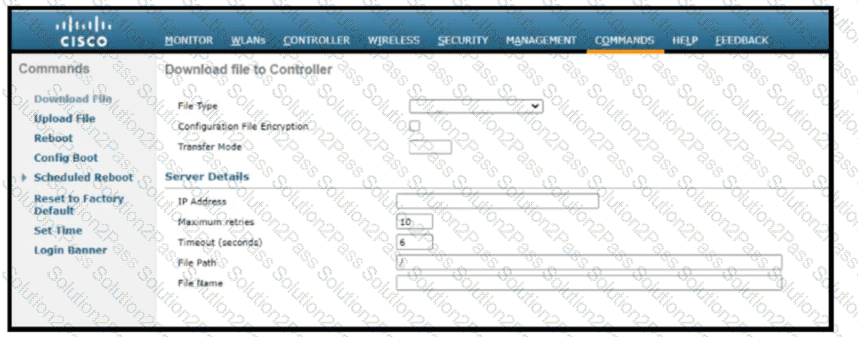
Refer to the exhibit. Which tasks must be performed on the Download File tab to install new software using TCP port 22?)
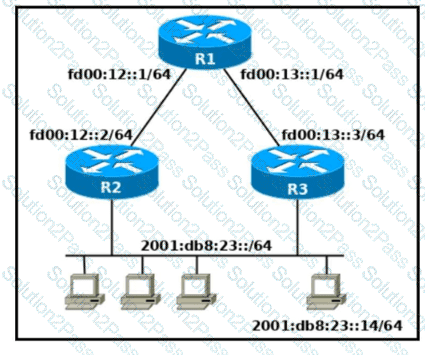
Refer to the exhibit. Which two commands, when configured on router R1. fulfill these requirements? (Choose two.) ' Packets toward the entire network 2001:db8:23: :/64 must be forwarded through router R2. ' Packets toward host 2001: db8:23::14 preferably must be forwarded through R3.
An organization developed new security policies and decided to print the policies and distribute them to all personnel so that employees review and apply the policies. Which element of a security program is the organization implementing?
What is the function of generative AI in network operations?
What are two behaviors of a point-to-point WAN topology? (Choose two.)
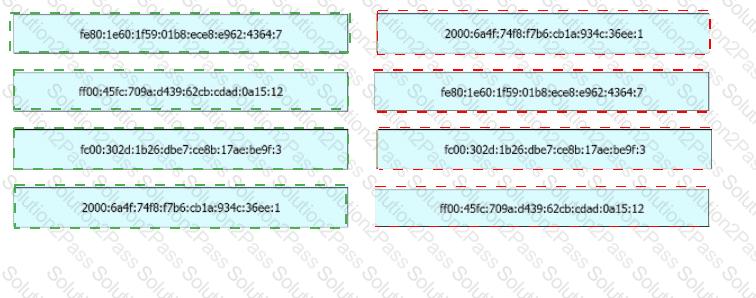
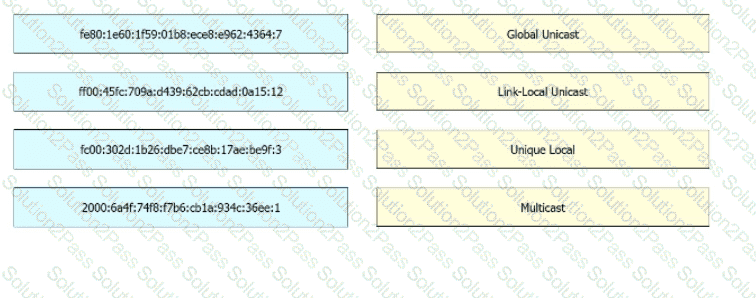
Drag and drop the IPv6 address from the left onto the type on the right.
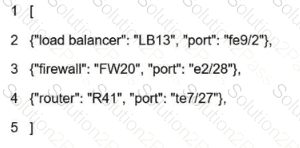
What is represented by the word "LB13" within this JSON schema?
Which two QoS tools provide congestion management? (Choose two.)
Which interface on the WLC is used exclusively as a DHCP relay?
Why does an administrator choose to implement a remote access IPsec VPN?
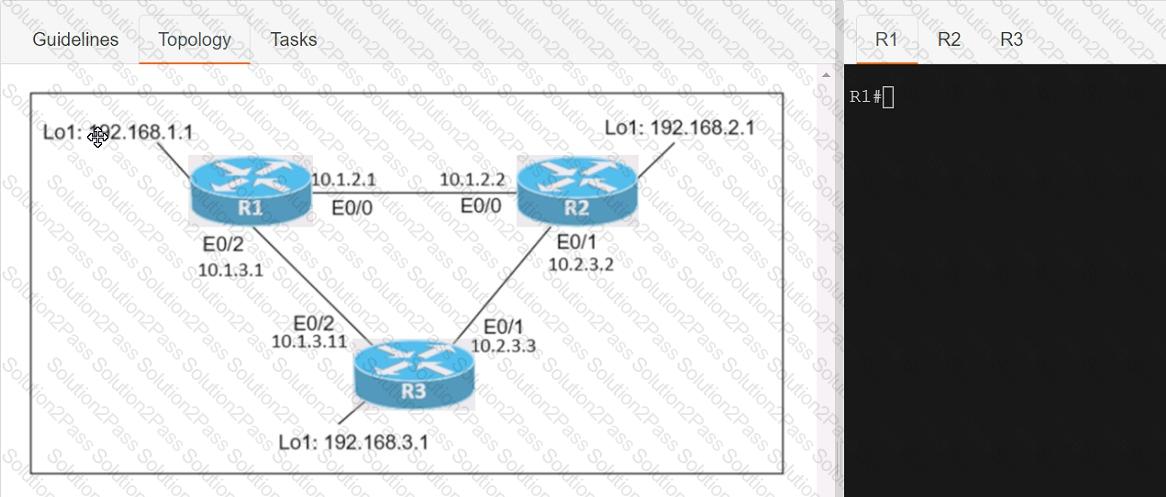
Connectivity between three routers has been established, and IP services must be configured jn the order presented to complete the implementation Tasks assigned include configuration of NAT, NTP, DHCP, and SSH services.
1. All traffic sent from R3 to the R1 Loopback address must be configured for NAT on R2. All source addresses must be translated from R3 to the IP address of Ethernet0/0 on R2, while using only a standard access list named NAT To verify, a ping must be successful to the R1 Loopback address sourced from R3. Do not use NVI NAT configuration.
2. Configure R1 as an NTP server and R2 as a client, not as a peer, using the IP address of the R1 Ethernet0/2 interface. Set the clock on the NTP server for midnight on January 1, 2019.
3. Configure R1 as a DHCP server for the network 10.1.3.0/24 in a pool named TEST. Using a single command, exclude addresses 1-10 from the range. Interface Ethernet0/2 on R3 must be issued the IP address of 10.1.3.11 via DHCP.
4. Configure SSH connectivity from R1 to R3, while excluding access via other remote connection protocols. Access for user root and password Cisco must be set on router R3 using RSA and 1024 bits. Verify connectivity using an SSH session from router R1 using a destination address of 10.1.3.11. Do NOT modify console access or line numbers to accomplish this task.
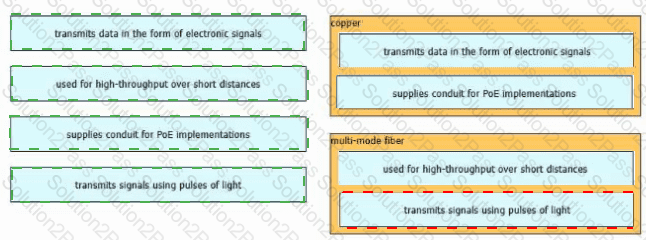
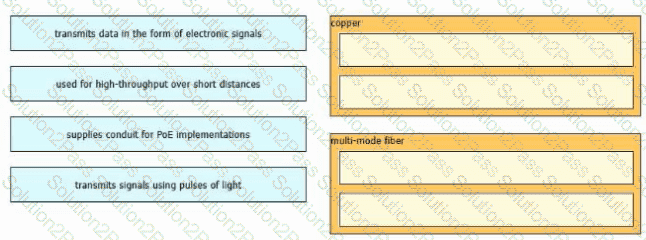
Drag and drop the characteristic from the left onto the cable type on the right.
Which technology allows for logical Layer 3 separation on physical network equipment?
A new DHCP server has been deployed in a corporate environment with lease time set to eight hours. Which CMD command on a Windows-based device allows the engineer to verify the DHCP lease expiration?