200-301 Cisco Certified Network Associate Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 200-301 Cisco Certified Network Associate certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
How is Al used to identify issues within network traffic?
How does automation leverage data models to reduce the operational complexity of a managed network?
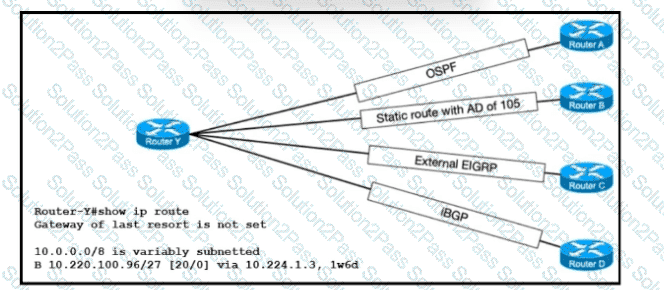
Refer to the exhibit. The route for 10.220.100.96/27 has been very unstable. The same route has four backups to routers A, B, C, and D via the respective methods. The routing protocol defaults for router Y have not been changed. When the current route for 10.220.100.96/27 becomes unavailable, which router will router Y use to route traffic to 10.220.100.96/27?
How does MAC learning function?
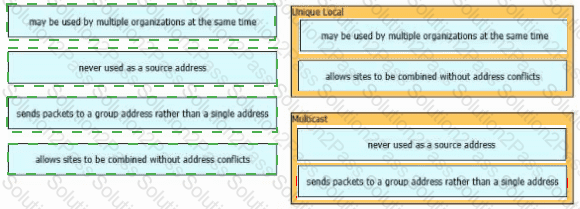
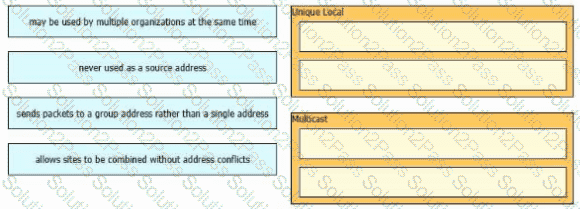
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Which type of protocol is VRRP?
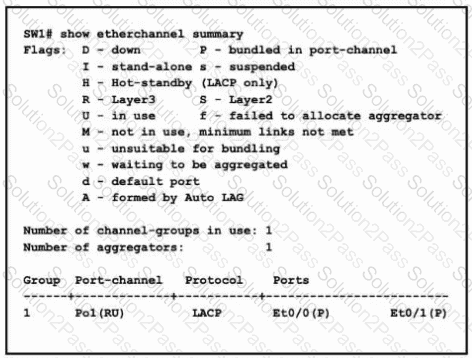
Refer to the exhibit. A network engineer is adding another physical interface as a new member to the existing Port-Channel1 bundle.
Which command set must be configured on the new interface to complete the process?
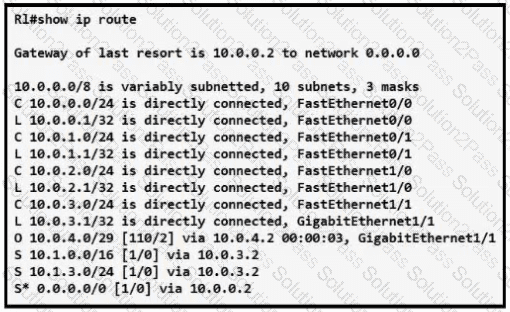
Refer to the exhibit.
How does router R1 forward packets destined to 10.0.4.10?
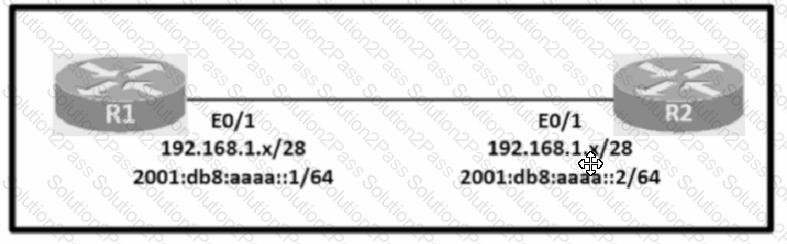
Configure IPv4 and IPv6 connectivity between two routers. For IPv4, use a /28 network from the 192.168.1.0/24 private range. For IPv6, use the first /64 subnet from the 2001:0db8:aaaa::/48 subnet.
1. Using Ethernet0/1 on routers R1 and R2, configure the next usable/28 from the 192.168.1.0/24 range. The network 192.168.1.0/28 is unavailable.
2. For the IPv4 /28 subnet, router R1 must be configured with the first usable host address.
3. For the IPv4 /28 subnet, router R2 must be configured with the last usable host address.
4. For the IPv6 /64 subnet, configure the routers with the IP addressing provided from the topology.
5. A ping must work between the routers on the IPv4 and IPv6 address ranges.
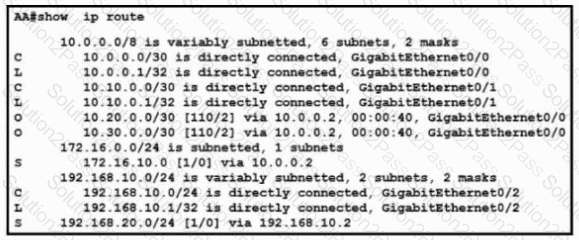
Refer to the exhibit. What is the administrative distance for the advertised prefix that includes the host IP address 10.30.0.1?
Which action prevents debug messages from being sent via syslog while allowing other messages when an abnormally high number of syslog messages are generated by a device with the debug process turned on?
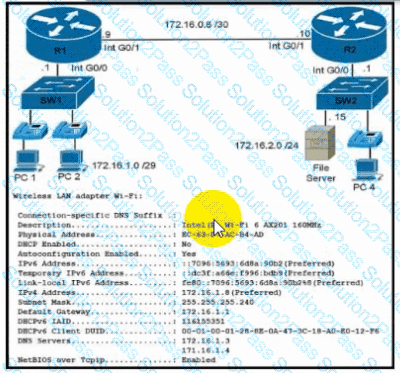
Refer to the exhibit. During initial configuration testing, the Windows workstation PC1 cannot connect with the 172.16.2.0/24 network.
Which set of actions corrects the configuration?

Refer to the exhibit. The routers R1-LAB and R2-LAB are configured with link-local addresses. What command must be applied to interface Gi0/0 on R1-LAB for an automated address self-assignment on the IPv6 network?
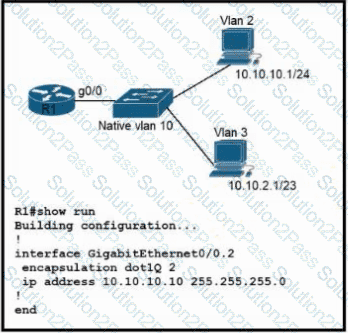
Refer to the exhibit. Configurations for the switch and PCs are complete.
Which configuration must be applied so that VLANs 2 and 3 communicate back and forth?
How does a network administrator securely manage an AP in lightweight mode?
Which interface is used to send traffic to the destination network?
10.90.207.87/26 [110/1912] via F0/7
10.90.207.87/26 [110/28968] via F0/6
10.90.207.87/26 [120/14] via F0/4
10.90.207.87/26 [120/11] via F0/5
Which fact must the engineer consider when implementing syslog on a new network?
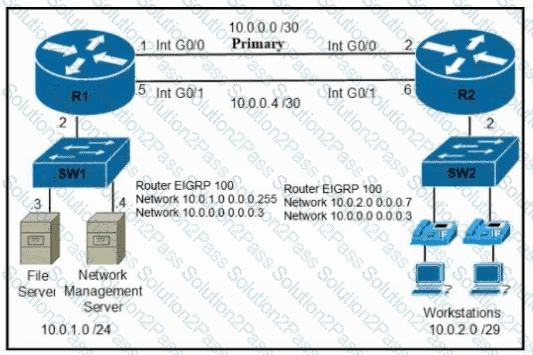
Refer to the exhibit. A secondary route is required on router R1 to pass traffic to the LAN network on R2 if the primary link fails. Which command must be entered to configure the router?
Refer to the exhibit.
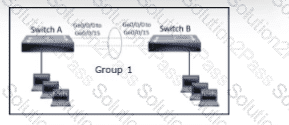
The LACP EtherChannel is configured, and the last change is to modify the interfaces on SwitchA to respond to packets received, but not to initiate negotiation. The interface range gigabitethernet0/0-15 command is entered. What must be configured next?
Refer to the exhibit.
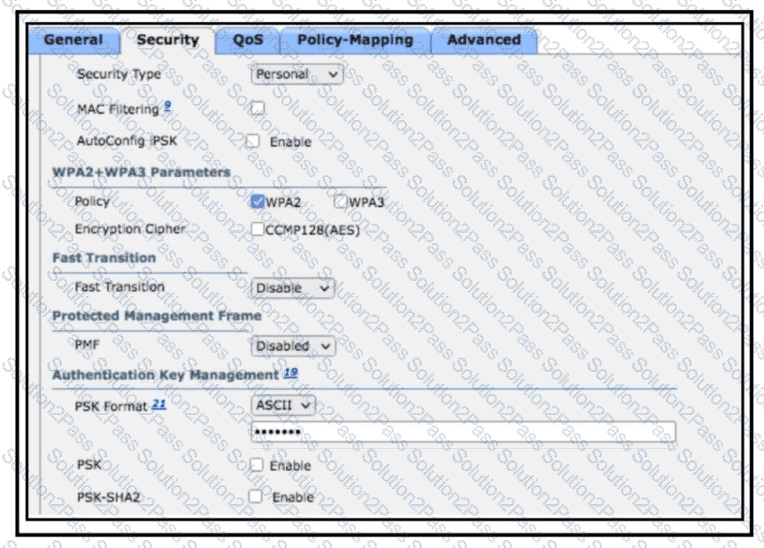
Users will be using a preconfigured secret key and SSID and must have a secured key hashing algorithm configured. The AAA server must not be used for the user authentication method. Which action completes the task?
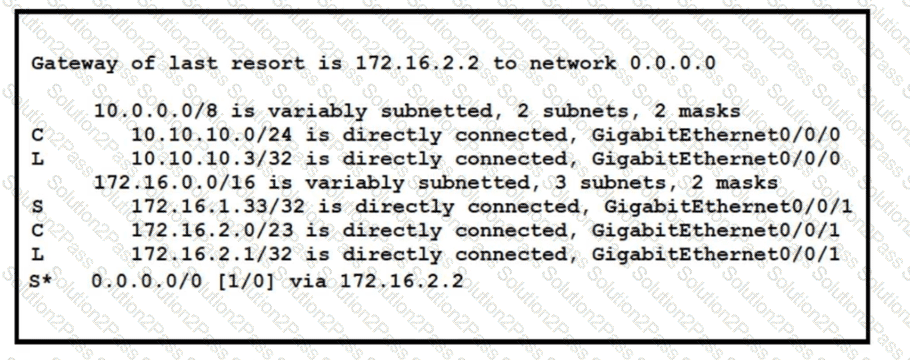
Refer to the exhibit. A packet sourced from 10.10.10.1 is destined for 172.16.3.254. What is the subnet mask of the destination route?
Why are API keys used to enforce rate limiting?
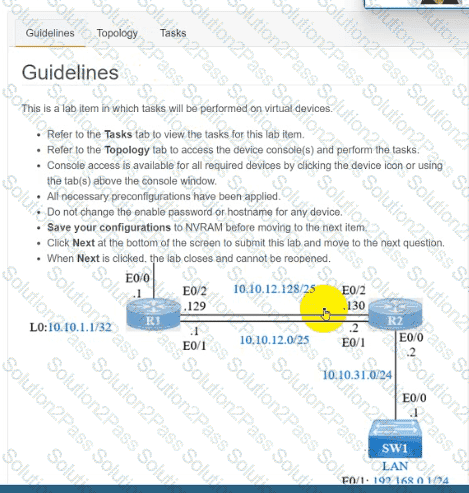
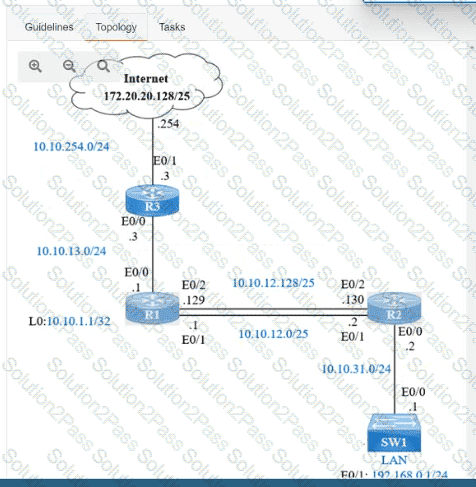
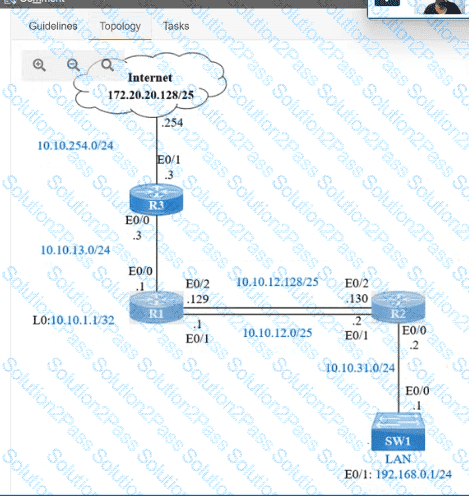
IP connectivity and OSPF are preconfigured on all devices where necessary. Do not make any changes to the IP addressing or OSPF. The company policy uses connected interfaces and next hops when configuring static routes except for load balancing or redundancy without floating static. Connectivity must be established between subnet 172.20.20.128/25 on the Internet and the LAN at 192.168.0.0/24 connected to SW1:
1. Configure reachability to the switch SW1 LAN subnet in router R2.
2. Configure default reachability to the Internet subnet in router R1.
3. Configure a single static route in router R2 to reach to the Internet subnet considering both redundant links between routers R1 and R2. A default route is NOT allowed in router R2.
4. Configure a static route in router R1 toward the switch SW1 LAN subnet where the primary link must be through Ethernet0/1. and the backup link must be through Ethernet0/2 using a floating route. Use the minimal administrative distance value when required.
How does automation affect network management processes?
What is an advantage of using SDN versus traditional networking when it comes to security?