200-301 Cisco Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-301 Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Why would a network administrator choose to implement RFC 1918 address space?
Refer to the exhibit.
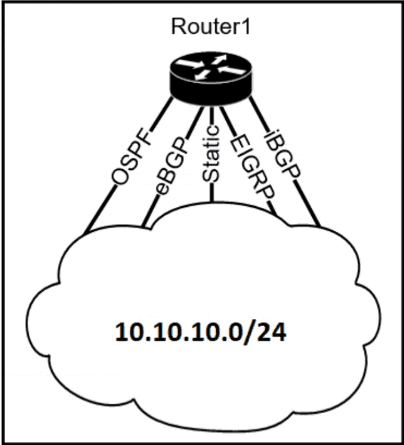
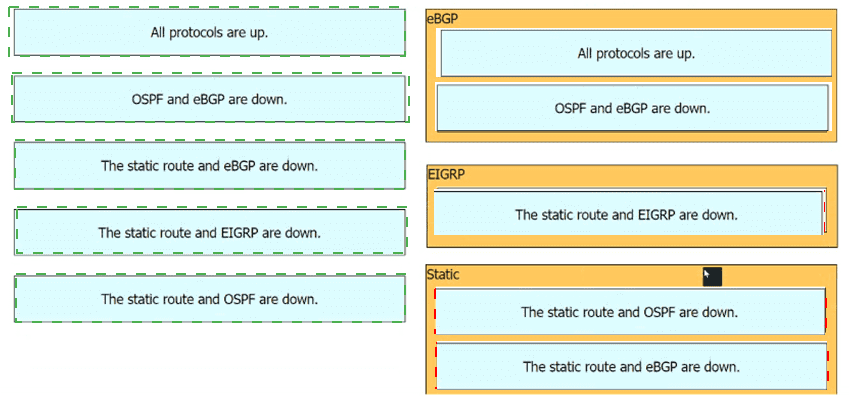
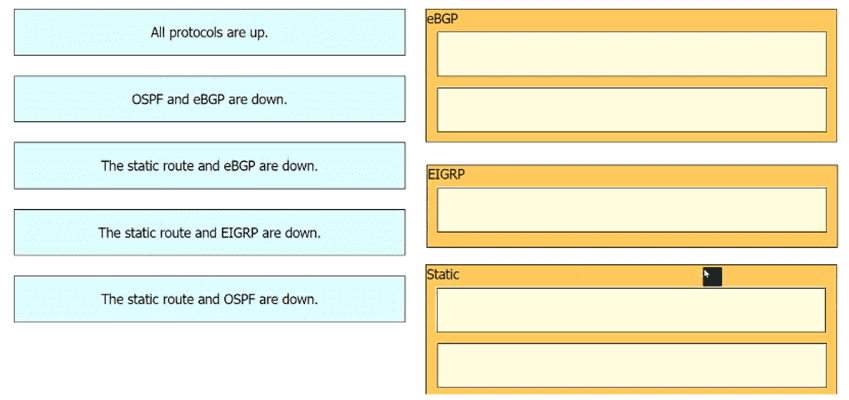
The Router1 routing table has multiple methods to reach 10.10.10.0/24 as shown. The default Administrative Distance is used. Drag and drop the network conditions from the left onto the routing methods that Router1 uses on the right.
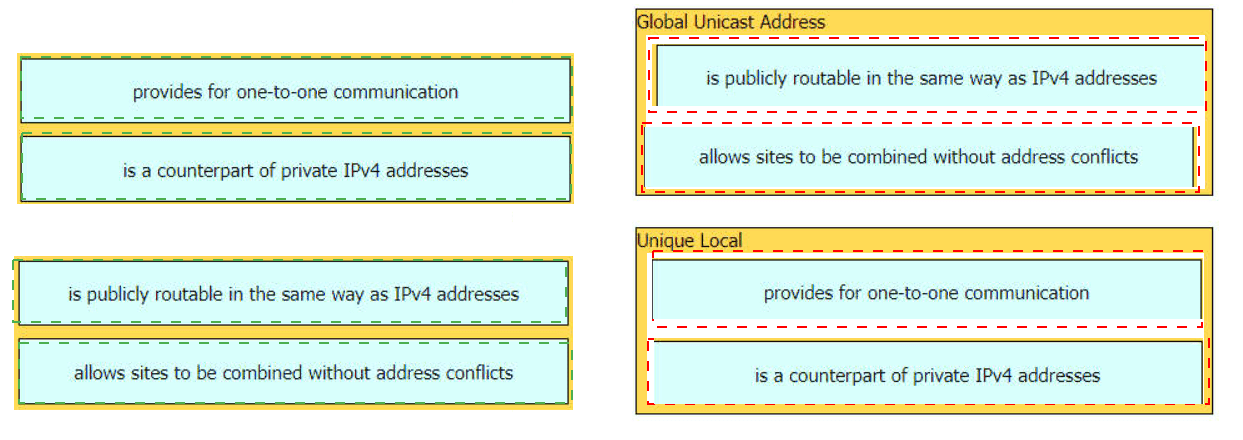
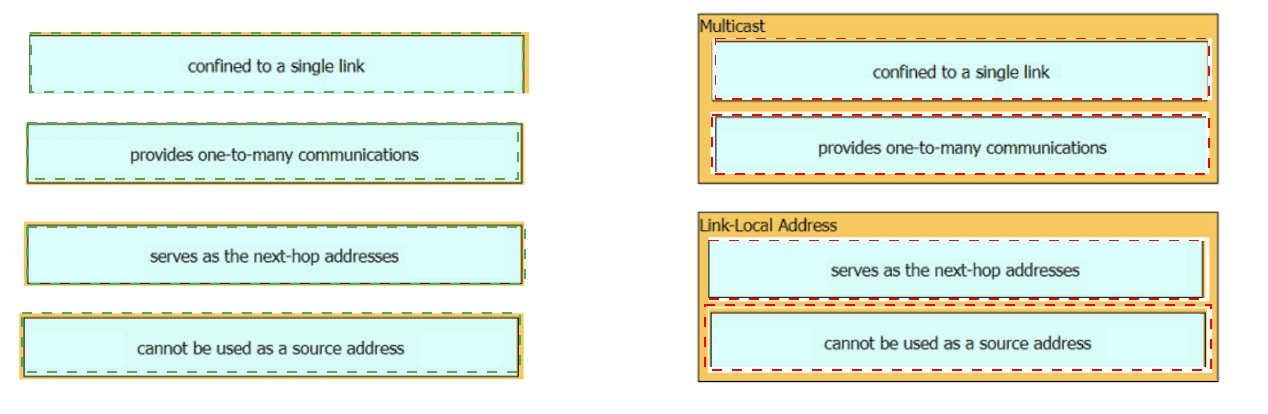
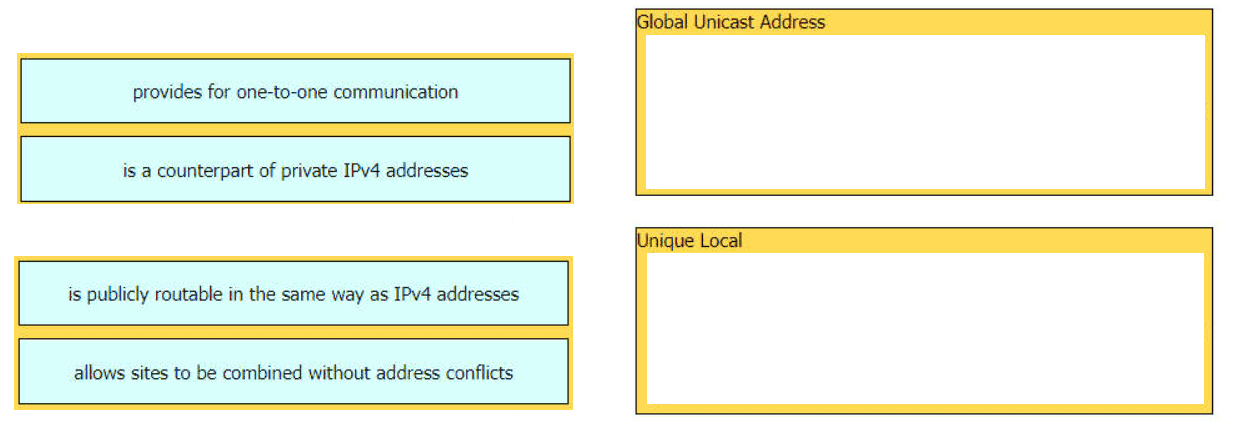
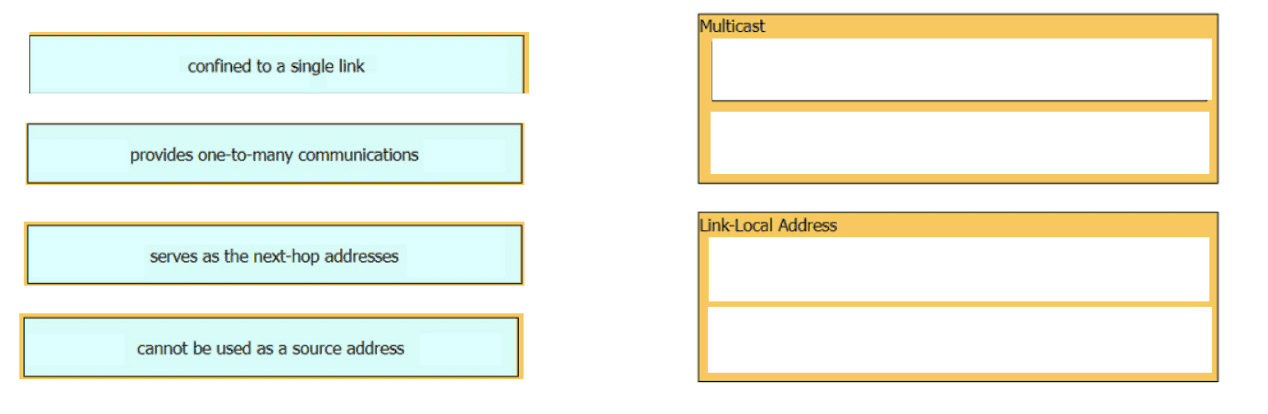
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
A router has two static routes to the same destination network under the same OSPF process. How does the router forward packets to the destination if the next-hop devices are different?
Why would VRRP be implemented when configuring a new subnet in a multivendor environment?
What is a zero-day exploit?
Refer to the exhibit.
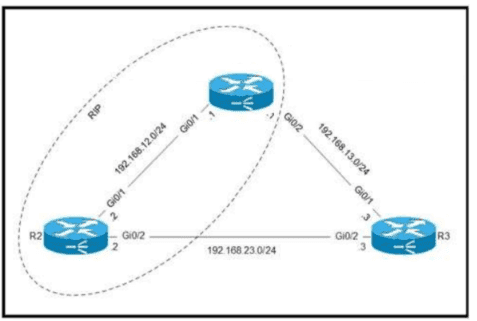
Routers R1 and R2 are configured with RIP as the dynamic routing protocol. A network engineer must configure R1 with a floating static route to serve as a backup route to network 192.168.23.0. Which command must the engineer configure on R1?
Refer to the exhibit.
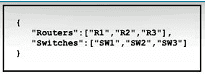
What is represented by "R1" and "SW1" within the JSON output?
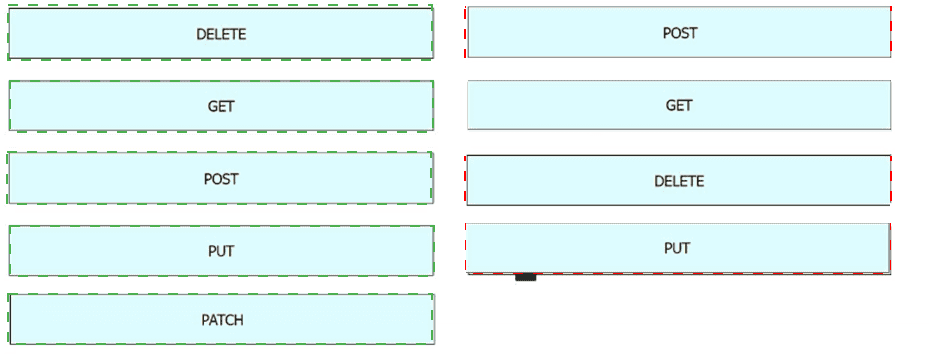
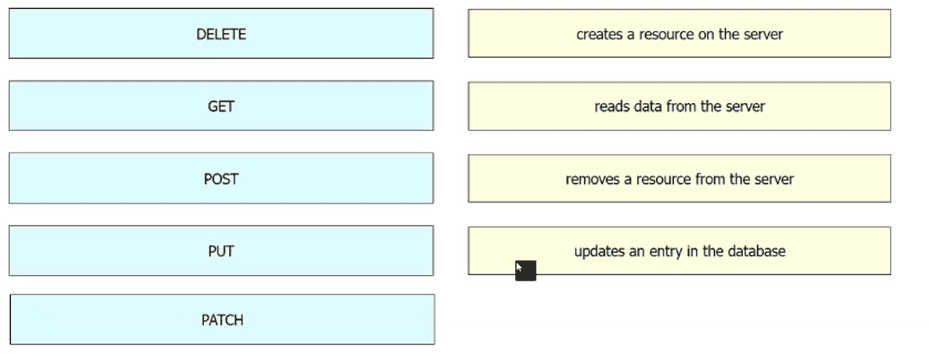
Drag and drop the REST API call method for HTTP from the left onto the action they perform on the right.
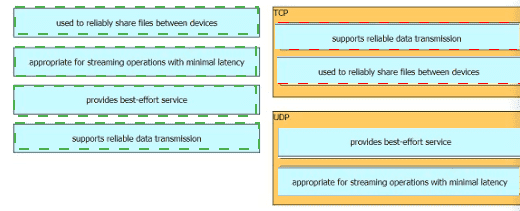
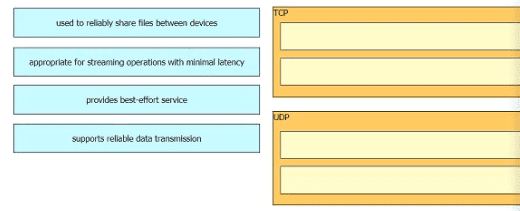
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
An engineer is configuring a switch port that is connected to a VoIP handset. Which command must the engineer configure to enable port security with a manually assigned MAC address of abod-bod on voice VLAN 4?
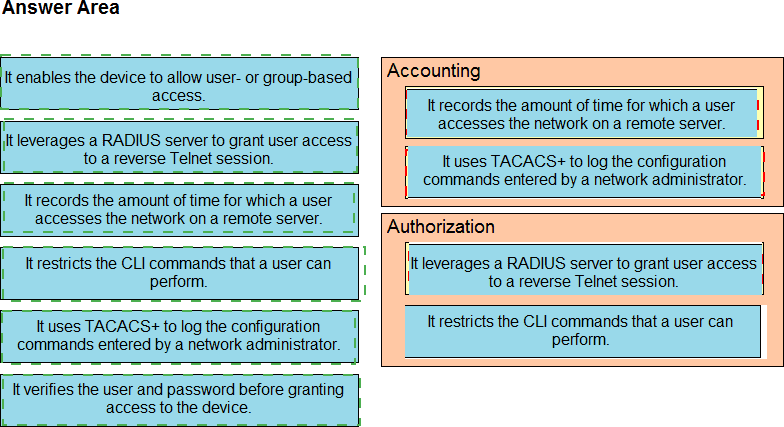
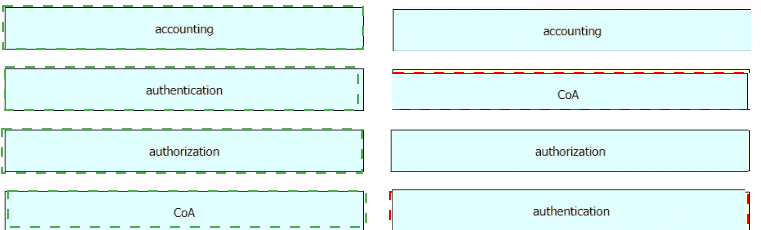
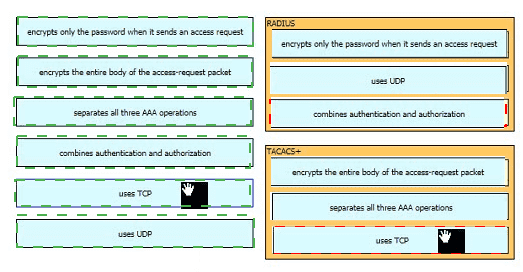
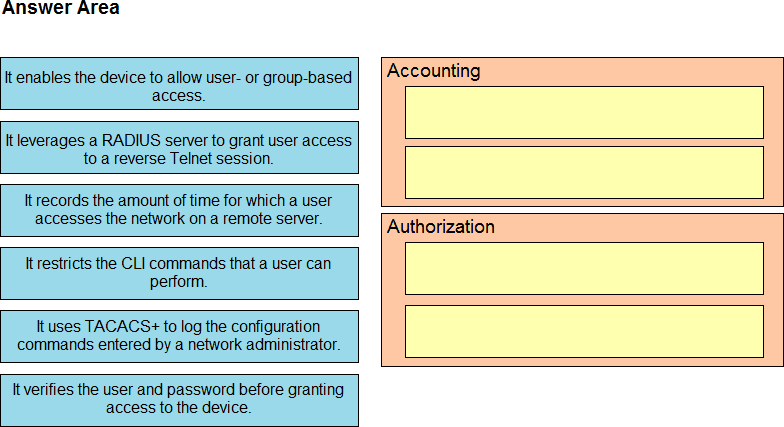
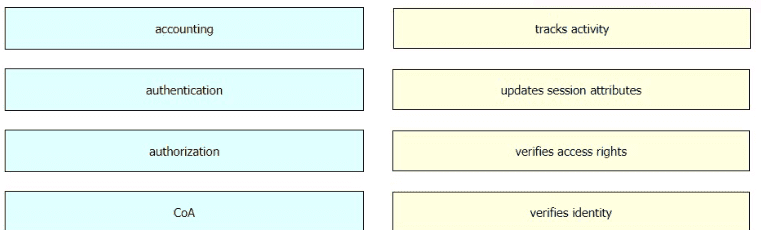
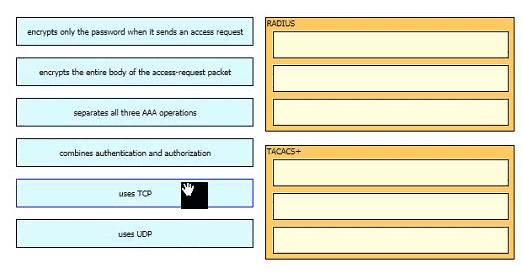
Drag and drop the AAA features from the left onto the corresponding AAA security services on the right. Not all options are used.
Refer to the exhibit.
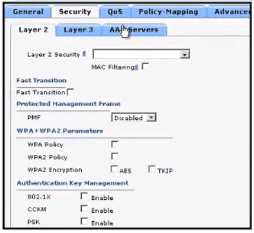
What are the two steps an engineer must take to provide the highest encryption and authentication using domain credentials from LDAP?
Refer to the exhibit.
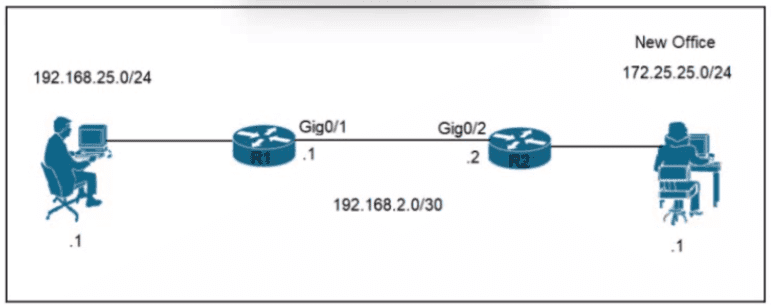
A network engineer is updating the configuration on router R1 to connect a new branch office to the company network R2 has been configured correctly. Which command must the engineer configure so that devices at the new site communicate with the main office?
What is a feature of WPA?
Which benefit does Cisco ONA Center provide over traditional campus management?
What is the difference between SNMP traps and SNMP polling?
Which protocol is used in Software Defined Access (SDA) to provide a tunnel between two edge nodes in different fabrics?
A manager asks a network engineer to recommend a cloud service model so that employees do not spend time installing, managing, and updating software that is only used occasionally. Which cloud service model does the engineer recommend?
A)
B)
C)
D)
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
What is an Ansible inventory?
Refer to the exhibit.
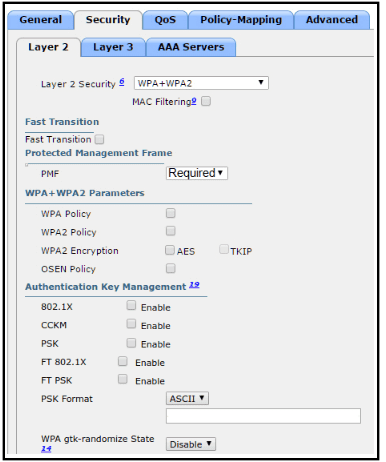
The network engineer is configuring a new WLAN and is told to use a static password for authentication instead of the RADIUS servers. Which additional set of tasks must the engineer perform to complete the configuration?
Refer to the exhibit.
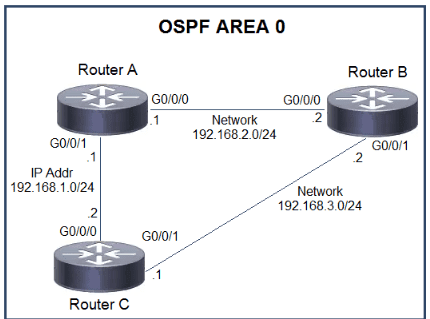
Which action must be taken to ensure that router A is elected as the DR for OSPF area 0?
Refer to the exhibit.
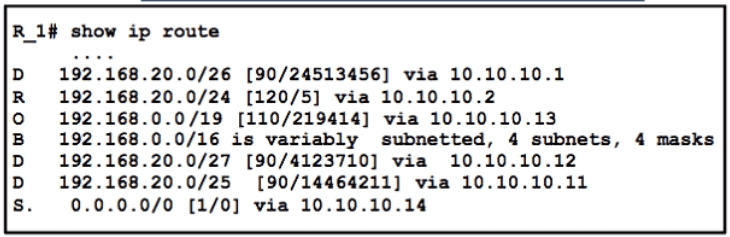
Packets are flowing from 192.168 10.1 to the destination at IP address 192.168.20 75. Which next hop will the router select for the packet?
Which Cisco proprietary protocol ensures traffic recovers immediately, transparently, and automatically when edge devices or access circuits fail?
Which event has occurred if a router sends a notice level message to a syslog server?
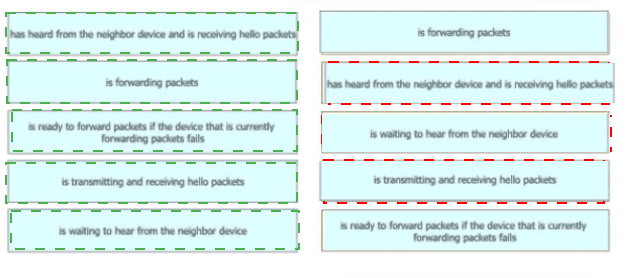
Drag and drop the device behaviors from the left onto the matching HSRP slate on the right.
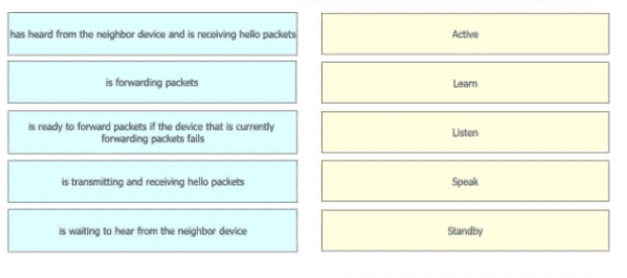
Refer to the exhibit.
The administrator must configure a floating sialic default route that points to 2001:db8:1234:2::1 and replaces the current default route only if it fails. Which command must the engineer configure on the CPE?
Refer to Itie exhibit
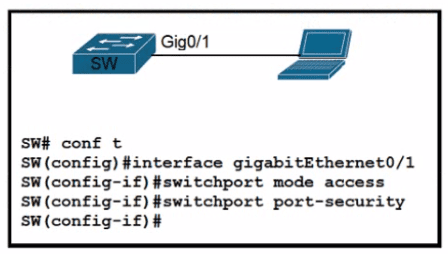
A network engineer started to configure port security on a new switch. These requirements must be met:
* MAC addresses must be learned dynamically
* Log messages must be generated without disabling the interface when unwanted traffic is seen
Which two commands must be configured to complete this task"? (Choose two)
Refer to the exhibit An IPv6 address must be obtained automatically on the LAN interface on R1 Which command must be implemented to accomplish the task?
Which REST method updates an object in the Cisco DNA Center Intent API?
Drag and drop the AAA lerms from the left onto the descriptions on the right.
Refer to the exhibit.
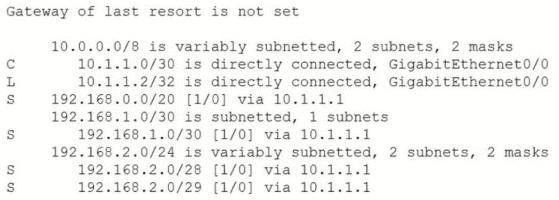
An engineer is checking the routing table in the main router to identify the path to a server on the network. Which route does the router use to reach the server at 192.168.2.2?
Refer to the exhibit.
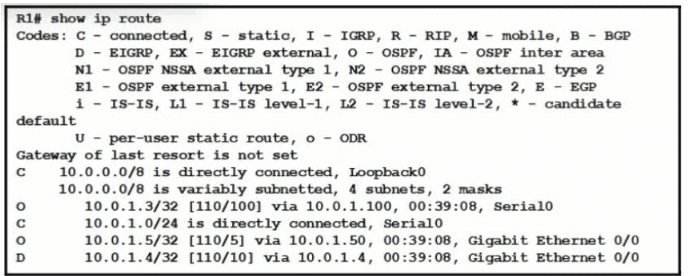
What does route 10.0.1.3/32 represent in the routing table?
Drag and drop the functions of AAA supporting protocols from the left onto the protocols on the right.
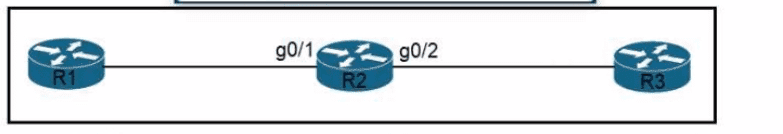
Refer to the exhibit Routers R1 R2 and R3 use a protocol to identify their neighbors' IP addresses hardware platforms, and software versions. A network engineer must configure R2 to avoid sharing any neighbor information with R3, and maintain its relationship with R1. What action meets this requirement?
Which device separates networks by security domains?
What is the purpose of using First Hop Redundancy Protocol on a specific subnet?
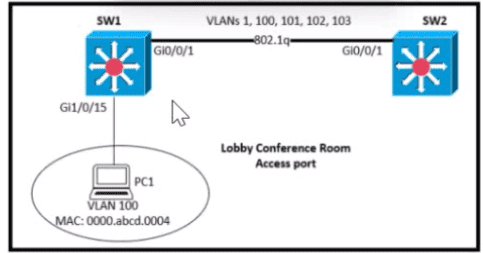
SW1 supports connectivity for a lobby conference room and must be secured. The engineer must limit the connectivity from PCI lo ma SW1 and SW2 network. The MAC addresses allowed must be Limited to two. Which configuration secures the conference room connectivity?
A)

B)

C)

D)

Which two IPv6 addresses are used to provide connectivity between two routers on a shared link? (Choose two)
Two switches have been implemented and all interfaces are at the default configuration level. A trunk link must be implemented between two switches with these requirements:
• using an industry-standard trunking protocol
• permitting VLANs 1 -10 and denying other VLANs
How must the interconnecting ports be configured?
A)

B)

C)

D)

A HCP pool has been created with the name CONTROL. The pool uses the next to last usable IP address as the default gateway for the DHCP clients. The server is located at 172.16 32.15. What is the step in the process for clients on the 192.168.52.0/24 subnet to reach the DHCP server?
When should an engineer implement a collapsed-core architecture?
Refer to the exhibit.
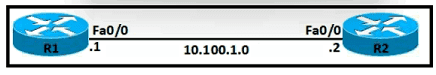
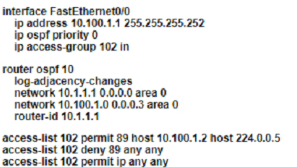
An OSPF neighbor relationship must be configured using these guidelines:
• R1 is only permitted to establish a neighbor with R2
• R1 will never participate in DR elections
• R1 will use a router-id of 101.1.1.
Which configuration must be used?
A)
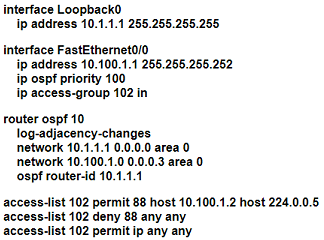
B)
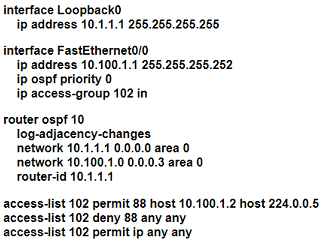
C)
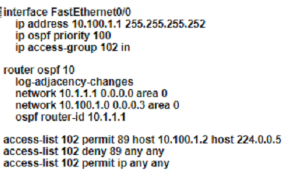
D)
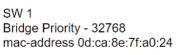
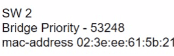
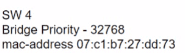
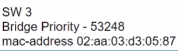
What is the role of the root port in a switched network?
Which command implies the use of SNMPv3?
Refer to the exhibit.
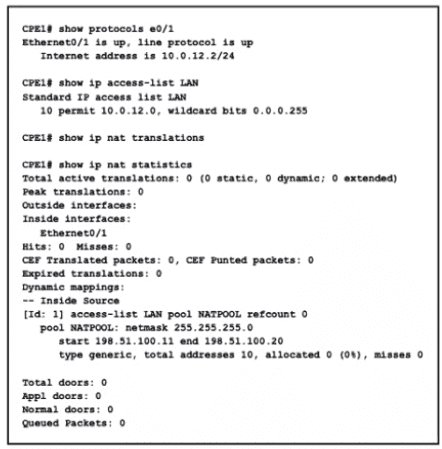
What is the next step to complete the implementation for the partial NAT configuration shown?
Which is a fact related to FTP?
Refer to the exhibit.
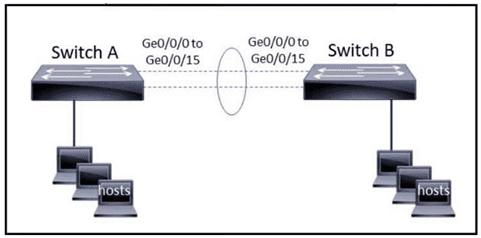
The EtherChannel is configured with a speed of 1000 and duplex as full on both ends of channel group 1. What is the next step to configure the channel on switch A to respond to but not initiate LACP communication?
Refer to the exhibit.
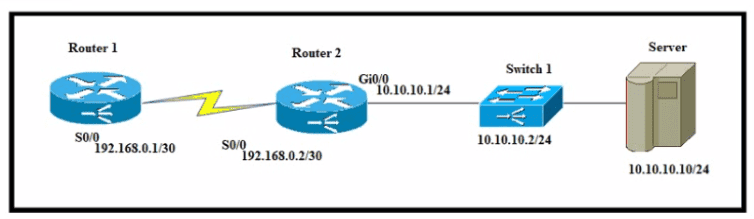
A network engineer must configure router R1 with a host route to the server. Which command must the engineer configure?
What are two purposes of HSRP? (Choose two.)
What are two examples of multifactor authentication? (Choose two.)
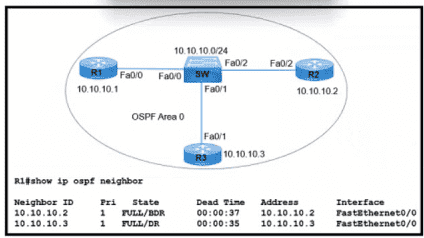
Refer to the exhibit. R1 has taken the DROTHER role in the OSPF DR/BDR election process. Which configuration must an engineer implement so that R1 is elected as the DR?
Which syslog severity level is considered the most severe and results in the system being considered unusable?
What is used to identify spurious DHCP servers?
Which alternative to password authentication Is Implemented to allow enterprise devices to log in to the corporate network?
Refer to the exhibit.

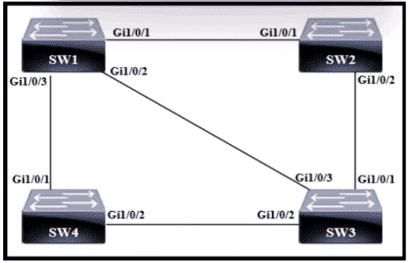
Which action must be taken so that neighbofing devices rapidly discover switch Cat9300?
Refer to the exhibit.
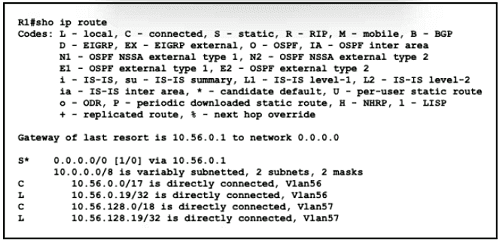
When router R1 is sending traffic to IP address 10.56.192 1, which interface or next hop address does it use to route the packet?
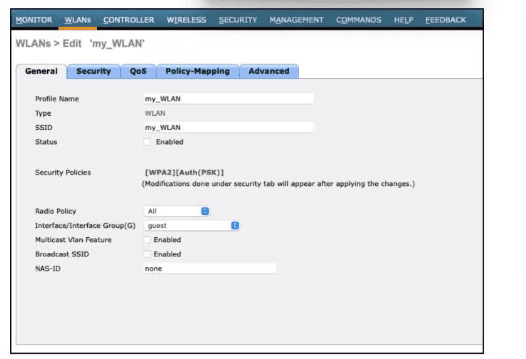
Refer to the exhibit. The My_WLAN wireless LAN was configured with WPA2 Layer 2 PSK security. Which additional configuration must the administrator perform to allow users to connect to this WKAN on a different subnet called Data?