300-430 Cisco Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-430 Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An engineer is configuring wireless guests using Cisco CWA. When a device connects, it must be redirected to the WebAuth, but this was failing. What must be configured for the device to be redirected correctly?
Which AP model of the Cisco Aironet Active Sensor is used with Cisco DNA Center?
A network engineer is configuring a Cisco AireOS WLC environment for central web authentication using Cisco ISE.
The controllers are configured using auto-anchor for the guest network.
Which three components must be implemented for the foreign WLC?(Choose three.)
In a Cisco WLAN deployment, it is required that all Aps from branch1 remain operational even if the control plane CAPWAP tunnel is down because of a WAN failure to headquarters. Which operational mode must be configured on the APs?
Refer to the exhibit.
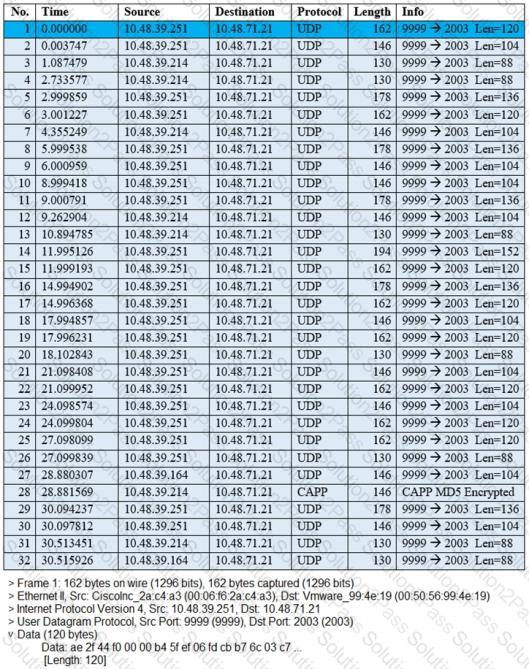
The image shows a packet capture that was taken at the CLI of the Cisco CMX server. It shows UDP traffic from the WLC coming into the server. What does the capture prove?
A user is trying to connect to a wireless network that is configured for WPA2-Enterprise security using a corporate laptop. The CA certificate for the authentication server has been installed on the Trusted Root Certification Authorities store on the laptop. The user has been prompted to enter the credentials multiple times, but the authentication has not succeeded. What is causing the issue?
An engineer needs to provision certificates on a Cisco Catalyst 9800 Series Wireless Controller. The customer uses a third-party CA server. Which protocol must be used between the controller and CA server to request and install certificates?
A Cisco WLC has been added to the network and Cisco ISE as a network device, but authentication is failing. Which configuration within the network device configuration should be verified?
A network engineer observes a spike in controller CPU overhead and overall network utilization after multicast is enabled on a controller with 500 APs. Which feature corrects the issue?
Refer to the exhibit.
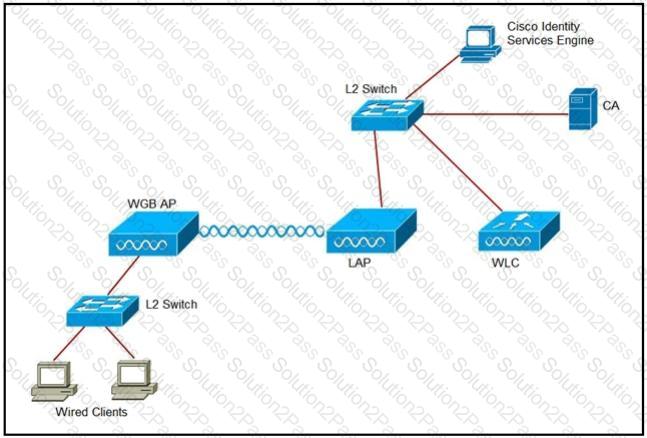
An engineer must connect a fork lift via a WGB to a wireless network and must authenticate the WGB certificate against the RADIUS server. Which three steps are required for this configuration? (Choose three.)
An engineer must achieve the highest level of location accuracy possible for a new mobile application. Which technology must be implemented for this use case?
What is an important consideration when implementing a dual SSID design for BYOD?
An engineer set up a VoWLAN with QoS on the WLC and a class map on the switch, but the markings are not being preserved correctly in the end-to- end traffic flow. Which two configurations on the wired network ensure end-to-end QoS? (Choose two.)
Where is a Cisco OEAP enabled on a Cisco Catalyst 9800 Series Wireless Controller?
What is the maximum time range that can be viewed on the Cisco DNA Center issues and alarms page?
After looking in the logs, an engineer notices that RRM keeps changing the channels for non-IEEE 802.11 interferers. After surveying the area, it has been decided that RRM should not change the channel. Which feature must be enabled to ignore non-802.11 interference?
Which component must be integrated with Cisco DNA Center to display the location of a client that is experiencing connectivity issues?
Refer to the exhibit.
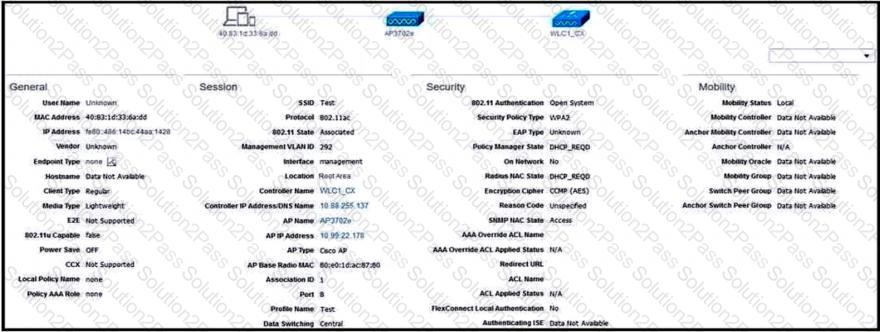
What is the reason that the wireless client cannot get the RUN state?
An engineer just added a new MSE to Cisco Prime Infrastructure and wants to synchronize the MSE with the Cisco 5520 WLC, located behind a firewall in a DMZ. It is noticed that NMSP messages are failing between the two devices. Which traffic must be allowed on the firewall to ensure that the MSE and WLC are able to communicate using NMSP?
An engineer must configure Cisco OEAPs for three executives. As soon as the NAT address is configured on the management interface, it is noticed that the WLC is not responding for APs that are trying to associate to the internal IP management address. Which command should be used to reconcile this?
