300-430 Cisco Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-430 Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit.
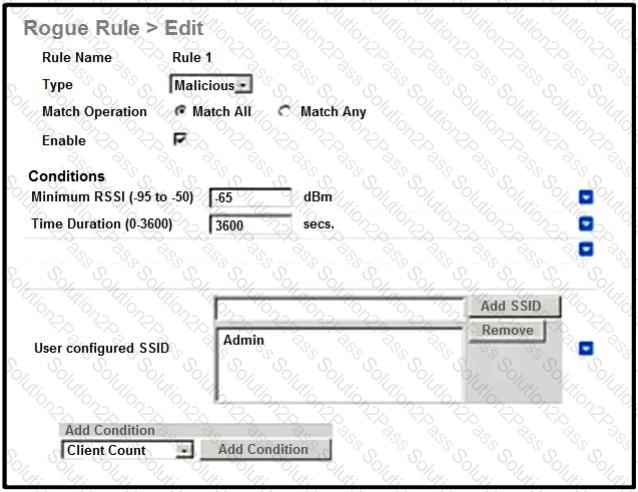
An engineer tries to manage the rogues on the Cisco WLC. Based on the configuration, which AP is marked as malicious by the controller?
An engineer added more APs to newly renovated areas in building. The engineer is now receiving Out-of-Sync alarms on Cisco Prime Infrastructure. Which two actions resolve this issue? (Choose two.)
An engineer has configured the wireless controller to authenticate clients on the employee SSID against Microsoft Active Directory using PEAP authentication.
Which protocol does the controller use to communicate with the authentication server?
Which EAP method can an AP use to authenticate to the wired network?
An engineer is implementing a FlexConnect group for access points at a remote location using local switching but central DHCP. Which client feature becomes available only if this configuration is changed?
Which statement about the VideoStream/Multicast Direct feature is true?
An engineer is following the proper upgrade path to upgrade a Cisco AireOS WLC from version 7.3 to 8.9. Which two ACLs for Cisco CWA must be configured when upgrading from the specified codes? (Choose two.)
The Cisco Hyperlocation detection threshold is currently set to -50 dBm. After reviewing the wireless user location, discrepancies have been noticed. To improve the Cisco Hyperlocation accuracy, an engineer attempts to change the detection threshold to -100 dBm. However, the Cisco Catalyst 9800 Series Wireless Controller does not allow this change to be applied. What actions should be taken to resolve this issue?
A network administrator just completed the basic implementation of Cisco CMX and tries to implement location tracking. The administrator is having trouble establishing connectivity between one of the WLCs through NMSP. What must be configured to establish this connectivity? (Choose two.)
Which two statements about the requirements for a Cisco Hyperlocation deployment are true? (Choose two.)
When configuring a Cisco WLC, which CLI command adds a VLAN with VLAN ID of 30 to a FlexConnect group named BranchA-FCG?
A wireless administrator receives this information to complete a CMX deployment in high availability by using version 10.6 to gather analytics.
IP address of the primary server
IP address of the secondary server
failover mode to be configured as automatic
root password of the secondary server
email ID for NOC notifications
Enabling high availability fails when these parameters are used. Which action resolves the issue?
An engineer is configuring an autonomous AP to allow 802.1X authentication for users. The policy on the RADIUS server only allows for EAP-TLS authentication. Which authentication method must the engineer select under the Client Authentication Settings for the SSID on the AP?
What are two considerations when deploying a Cisco Hyperlocation? (Choose two.)
An engineer must control administrative access to the WLC using their Active Directory without being concerned about RBAC after the admin user is authenticated. Which two features does the engineer configure to accomplish this task? (Choose two.)
When implementing self-registration for guest/BYOD devices, what happens when an employee tries to connect four devices to the network at the same time?
Refer to the exhibit.
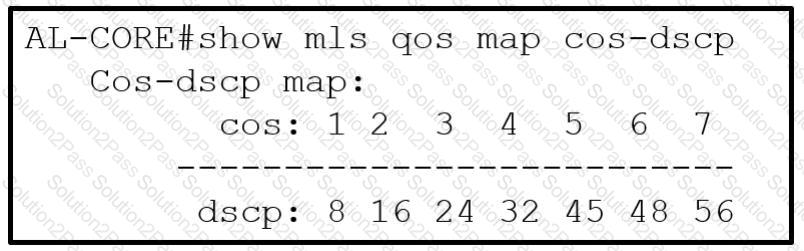
Which COS to DSCP map must be modified to ensure that voice traffic is tagged correctly as it traverses the network?
An engineer must provide a graphical report with summary grouped data of the total number of wireless clients on the network. Which Cisco Prime Infrastructure report provides the required data?
A customer is concerned that their wireless network is detecting spurious threats from channels that are not being used by their wireless infrastructure. Which two technologies must they deploy? (Choose two.)
An engineer wants to upgrade the APs in a Cisco FlexConnect group. To accomplish this upgrade, the FlexConnect AP Upgrade setting will be used. One AP of each model with the lowest MAC address in the group must receive the upgrade directly from the controller. Which action accomplishes this direct upgrade?
