300-540 Cisco Designing and Implementing Cisco Service Provider Cloud Network Infrastructure (SPCNI v1.0) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-540 Designing and Implementing Cisco Service Provider Cloud Network Infrastructure (SPCNI v1.0) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
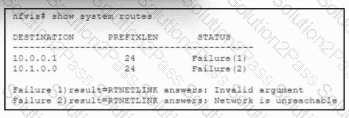
Refer to the exhibit. An engineer must deploy a standalone Cisco NFVIS. These configurations were performed already:
Deployed the virtual machine
Configured the hostname and IP address
Configured dual WAN support
When the engineer attempts to access the NFVIS portal, the API returns a 401 Unauthorized error. What is the cause of the issue?

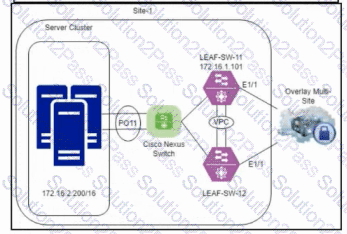
Refer to the exhibit. An engineer is troubleshooting an issue with switch LEAF-SW-11. The engineer observes that several main servers on the VXLAN BGP EVPN Multi-Site network experience 50–60% packet loss inbound and outbound, and all the DCI tracking interfaces are down. Which two actions must be taken to resolve the issue? (Choose two.)
How does log management assist in meeting the requirements of cloud security regulatory compliance?
What is a valid connection method between carrier-neutral facilities within the same metro area?
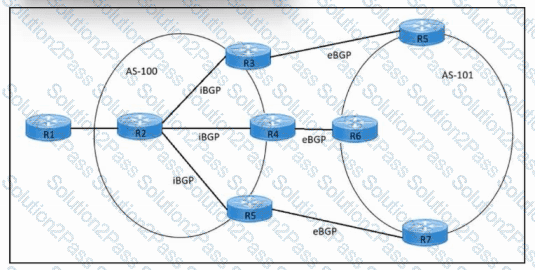
Refer to the exhibit. An engineer must configure iBGP multipath load sharing across three paths. Which two commands must be run on router R2? (Choose two.)
What is a valid connection method between carrier-neutral facilities that are more than 20 miles away from each other?
What should be used to protect against lateral movements during a Cisco NFVI security breach?
An engineer must implement a solution on a Cisco ASR 1000 Series router to protect against DDoS attacks. DDoS traffic must be dropped by transmitting Flowspec attributes to edge routers, instructing them to generate an ACL via class-maps and policy-maps. The engineer already configured BGP neighbors. Which action must be taken next?
Which two tools should be used to manage container orchestration? (Choose two.)
Which command must be run on a Cisco IOS device to configure six parallel iBGP and eBGP routes that can be installed into a routing table?
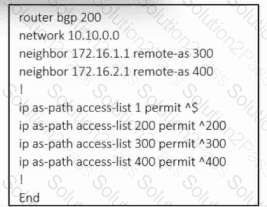
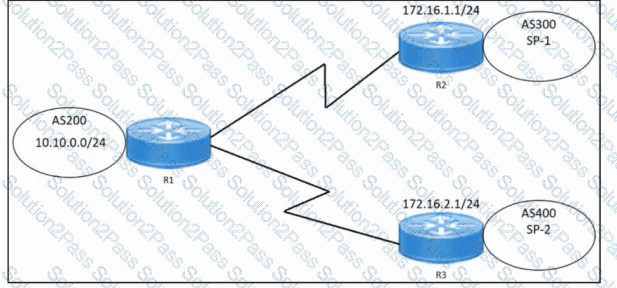
Refer to the exhibit. An engineer must configure multihoming between router R1 and service providers SP-1 and SP-2. Locally generated routes must be advertised to the service providers, and should prevent the risk that the local autonomous system becomes a transit AS for Internet traffic. Which two commands must be run on R1 to complete the configuration? (Choose two.)
What does Cisco Always-On Cloud DDoS use to protect against DDoS attacks?
Which two network segments are needed to support Cisco VIM? (Choose two.)
What is a benefit of using VXLANs in a cloud-scale environment?
An engineer must create a new VPC and deploy several Amazon EC2 instances in AWS. Only SSH connections originating from IP address 20.20.20.20 must be allowed to reach the EC2 instances. What must be configured?
Which format is used by Cisco Container Platform for configuration files?
Which command must be run on a Cisco IOS device to configure six parallel iBGP and eBGP routes that can be installed into a routing table?
A large company's legacy network is set up with equipment from multiple vendors. The company engaged a network architect to optimize the network for virtualization. The architect must ensure robust and efficient operation, considering the company's immediate needs but also anticipating future network complexities and scalability requirements. The chosen strategy must be capable of integrating seamlessly with existing systems, while providing a pathway for innovation and growth. The solution must facilitate end-to-end service automation throughout the entire lifecycle, and the implementation must ensure the validation, execution, and abstraction of network configurations and services. Which action must be taken to meet the requirements?
