300-710 Cisco Securing Networks with Cisco Firepower (300-710 SNCF) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-710 Securing Networks with Cisco Firepower (300-710 SNCF) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An engineer must investigate a connectivity issue by using Cisco Secure Firewall Management Center to access the Packet Capture feature on a Cisco Secure Firewall Threat Defense
device. The engineer must see a real packet going through the Secure Firewall Threat Defense device and the Snort detection actions. While reviewing the packet capture, the engineer
discovers that the Snort detection actions are missing. Which action must the engineer take to resolve the issue?
Which feature sets up multiple interfaces on a Cisco Secure Firewall Threat Defense to be on the same subnet?
Which two deployment types support high availability? (Choose two.)
An engineer is troubleshooting connectivity to the DNS servers from hosts behind a new Cisco FTD device. The hosts cannot send DNS queries to servers in the DMZ. Which action should the engineer take to troubleshoot this issue using the real DNS packets?
When a Cisco FTD device is configured in transparent firewall mode, on which two interface types can an IP address be configured? (Choose two.)
A hospital network needs to upgrade their Cisco FMC managed devices and needs to ensure that a disaster recovery process is in place. What must be done in order to minimize downtime on the network?
A network administrator is troubleshooting access to a website hosted behind a Cisco FTD device External clients cannot access the web server via HTTPS The IP address configured on the web server is 192 168 7.46 The administrator is running the command capture CAP interface outside match ip any 192.168.7.46 255.255.255.255 but cannot see any traffic in the capture Why is this occurring?
An administrator is configuring a new report template off. of a saved search within Cisco Secure Firewall Management Centre. The goal is to use the malware analysis report template, but use a different type saved search as the basis. The report is not working. What must be considered when configuring this report template?
An engineer must create an access control policy on a Cisco Secure Firewall Threat Defense device. The company has a contact center that utilizes VoIP heavily, and it is critical that this traffic is not …. by performance issues after deploying the access control policy Which access control Action rule must be configured to handle the VoIP traffic?
An engineer is deploying failover capabilities for a pair of Cisco Secure Firewall devices. The core switch keeps the MAC address of the previously active unit in the ARP table. Which action must the engineer take to minimize downtime and ensure that network users keep access to the internet after a Cisco Secure Firewall failover?
A company is in the process of deploying intrusion prevention with Cisco FTDs managed by a Cisco FMC. An engineer must configure policies to detect potential intrusions but not block the suspicious traffic. Which action accomplishes this task?
The administrator notices that there is malware present with an .exe extension and needs to verify if any of the systems on the network are running the executable file. What must be configured within Cisco AMP for Endpoints to show this data?
An engineer is configuring a custom application detector for HTTP traffic and wants to import a file that was provided by a third party. Which type of flies are advanced application detectors creates and uploaded as?
A network engineer must provide redundancy between two Cisco FTD devices. The redundancy configuration must include automatic configuration, translation, and connection updates. After the initial configuration of the two appliances, which two steps must be taken to proceed with the redundancy configuration? (Choose two.)
An engineer is setting up a remote access VPN on a Cisco FTD device and wants to define which traffic gets sent over the VPN tunnel. Which named object type in Cisco FMC must be used to accomplish this task?
An engineer is setting up a new Firepower deployment and is looking at the default FMC policies to start the implementation During the initial trial phase, the organization wants to test some common Snort rules while still allowing the majority of network traffic to pass Which default policy should be used?
An engineer is deploying a Cisco Secure Firewall Management Center appliance. The company must send data to Cisco Secure Network Analytics appliances. Which two actions must the engineer take? (Choose two.)
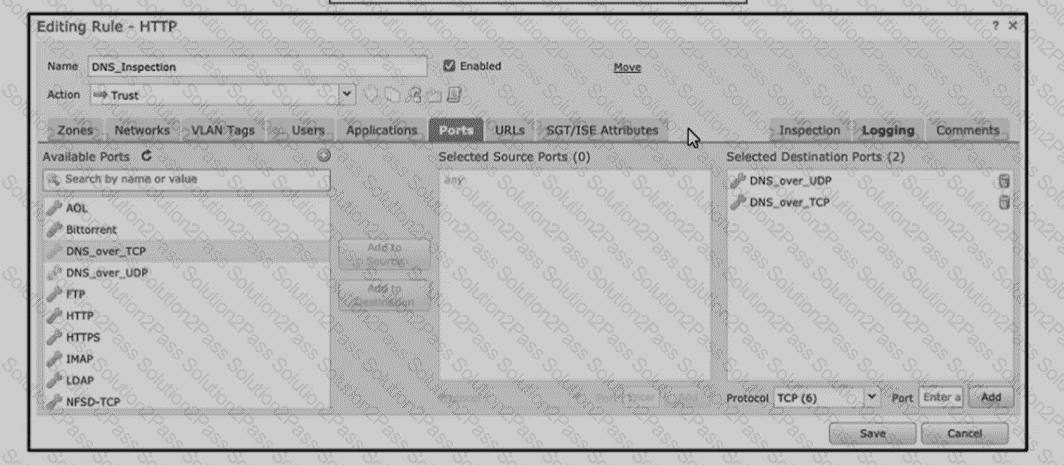
Refer to the exhibit An engineer is modifying an access control pokey to add a rule to inspect all DNS traffic that passes through the firewall After making the change and deploying thepokey they see that DNS traffic is not bang inspected by the Snort engine What is the problem?
An engineer must configure a correlation policy in Cisco Secure Firewall Management Center to detect when an IP address from an internal network communicates with a known malicious host. Connections made by the internal IP addresses must be tracked, and an external dynamic list must be used for the condition. Which type of event must the engineer configure on the correlation policy?
What is the result of specifying of QoS rule that has a rate limit that is greater than the maximum throughput of an interface?
