300-710 Cisco Securing Networks with Cisco Firepower (300-710 SNCF) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-710 Securing Networks with Cisco Firepower (300-710 SNCF) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An engineer must perform a packet capture on a Cisco Secure Firewall Threat Defense device to confirm the MAC address of the host using IP address 192.168.100.100 while troubleshooting an ARP issue. What is the correct tcpdump command syntax to ensure that the MAC address appears in the packet capture output?
On the advanced tab under inline set properties, which allows interfaces to emulate a passive interface?
A network administrator is migrating from a Cisco ASA to a Cisco FTD.
EIGRP is configured on the Cisco ASA but it is not available in the Cisco FMC.
Which action must the administrator take to enable this feature on the Cisco FTD?
Refer to the exhibit.

An engineer generates troubleshooting files in Cisco Secure Firewall Management Center (FMC). A successfully completed task Is removed before the files are downloaded. Which two actions must be taken to determine the filename and obtain the generated troubleshooting files without regenerating them? (Choose two.)
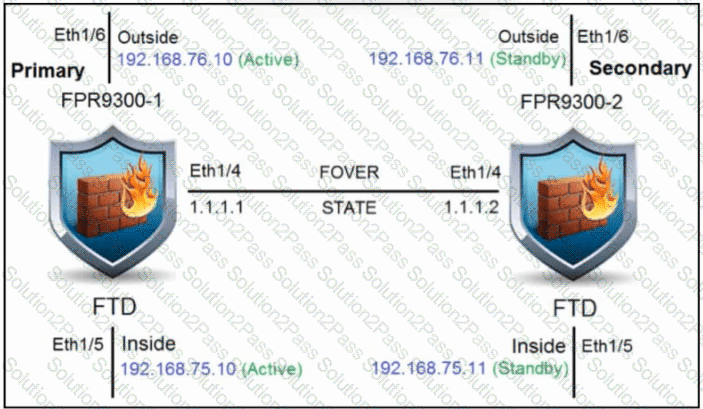
Refer to the exhibit. An engineer is configuring a high-availability solution that has the hardware devices and software versions:
two Cisco Secure Firewall 9300 Security Appliances with FXOS SW 2.0(1.23)
software Cisco Secure Firewall Threat Defense 6.0.1.1 (build 1023) on both appliances
one Cisco Secure Firewall Management Center with SW 6.0.1.1 (build 1023)
Which condition must be met to complete the high-availability configuration?
An organization is migrating their Cisco ASA devices running in multicontext mode to Cisco FTD devices. Which action must be taken to ensure that each context on the Cisco ASA is logically separated in the Cisco FTD devices?
An administrator configures a Cisco Secure Firewall Threat Defense device in transparent mode. To configure the BVI (Bridge Virtual Interface), the administrator must:
Add a bridge-group interface
Configure a bridge-group ID
Configure the bridge-group interface description
Add bridge-group member interfaces
How must the engineer perform these actions?
An engineer is investigating connectivity problems on Cisco Firepower that is using service group tags. Specific devices are not being tagged correctly, which is preventing clients from using the proper policies when going through the firewall How is this issue resolved?
An organization is implementing Cisco FTD using transparent mode in the network. Which rule in the default Access Control Policy ensures that this deployment does not create a loop in the network?
While integrating Cisco Umbrella with Cisco Threat Response, a network security engineer wants to automatically push blocking of domains from the Cisco Threat Response interface to Cisco Umbrella. Which API meets this requirement?
With a recent summer time change, system logs are showing activity that occurred to be an hour behind real time Which action should be taken to resolve this issue?
Within an organization's high availability environment where both firewalls are passing traffic, traffic must be segmented based on which department it is destined for. Each department is situated on a different LAN. What must be configured to meet these requirements?
The event dashboard within the Cisco FMC has been inundated with low priority intrusion drop events, which are overshadowing high priority events. An engineer has been tasked with reviewing the policies and reducing the low priority events. Which action should be configured to accomplish this task?
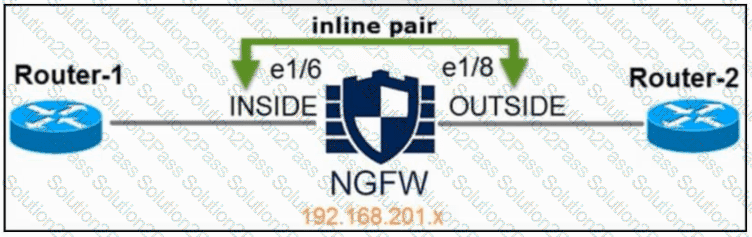
Refer to the exhibit. An engineer is configuring an instance of Cisco Secure Firewall Threat Defense with interfaces in IPS Inline Pair mode. What must be configured on interface e1/6 to accomplish the requirement?
Users report that Cisco Duo 2FA fails when they attempt to connect to the VPN on a Cisco Secure Firewall Threat Defense (FTD) device IT staff have VPN profiles that do not require multifactor authentication and they can connect to the VPN without any issues When viewing the VPN troubleshooting log in Cisco Secure Firewall Management Centre (FMC), the network administrator sees an error in the Cisco Duo AAA server has been marked as tailed. What is the root cause of the Issue?
A security engineer is configuring an Access Control Policy for multiple branch locations. These locations share a common rule set and utilize a network object called INSIDE_NET which contains the locally significant internal network subnets at each location. Which technique will retain the policy consistency at each location but allow only the locally significant network subnet within the applicable rules?
A security engineer is adding three Cisco FTD devices to a Cisco FMC. Two of the devices have successfully registered to the Cisco FMC. The device that is unable to register is located behind a router that translates all outbound traffic to the router's WAN IP address. Which two steps are required for this device to register to the Cisco FMC? (Choose two.)
An engineer must configure an inline set on a Cisco Secure IPS by using the Cisco Secure Firewall Management Center. The inline set must make a copy of each packet before analyzing the packet and block any connections that do not complete the three-way handshake. These configurations have been performed already:
Select and enable the interfaces that will be added to the inline set.
Configure the speed and duplex.
Configure the inline set and add the interfaces to the inline set.
Which action completes the task?
A network engineer detects a connectivity issue between Cisco Secure Firewall Management Center and Cisco Secure Firewall Threat Defense. Initial troubleshooting indicates that heartbeats and events are not being received. The engineer re-establishes the secure channels between both peers. Which two commands must the engineer run to resolve the issue? (Choose two.)
A Cisco FTD has two physical interfaces assigned to a BVI. Each interface is connected to a different VLAN on the same switch. Which firewall mode is the Cisco FTD set up to support?
