300-715 Cisco Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-715 Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which CLI command must be configured on the switchport to immediately run the MAB process if a non-802.1X capable endpoint connects to the port?
An engineer must use Cisco ISE to provide network access to endpoints that cannot support 802.1X. The endpoint MAC addresses must be allowlisted by configuring an endpoint identity group. These configurations were performed:
Configured an identity group named allowlist
Configured the endpoints to use the MAC address of incompatible 802.1X devices
Added the endpoints to the allowlist identity group
Configured an authentication policy for MAB users
What must be configured?
When creating a policy within Cisco ISE for network access control, the administrator wants to allow different access restrictions based upon the wireless SSID to which the device is connecting. Which policy condition must be used in order to accomplish this?
Which two ports do network devices typically use for CoA? (Choose two)
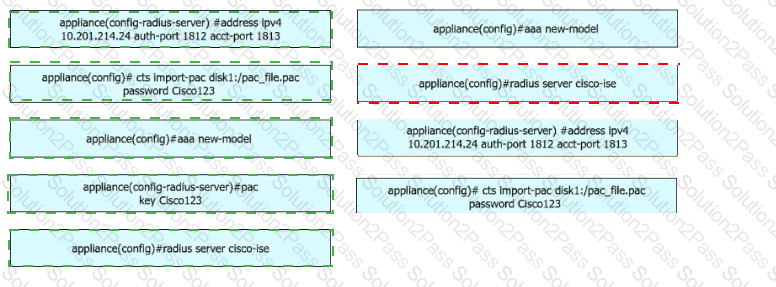
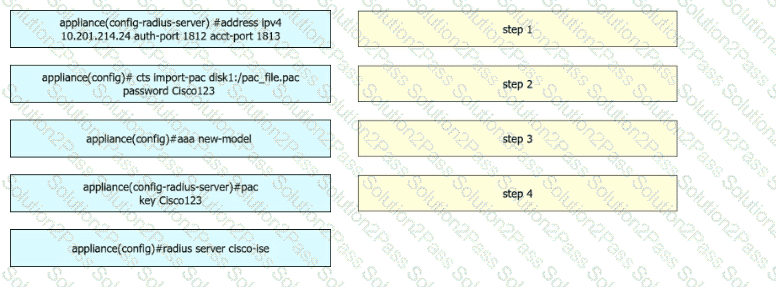
A security engineer configures a Cisco Catalyst switch to use Cisco TrustSec. The engineer must define the PAC key to authenticate the switch to Cisco IISE. Drag and drop the commands from the left into sequence on the right. Not all options are used.
Refer to the exhibit.
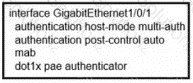
Which switch configuration change will allow only one voice and one data endpoint on each port?
A user reports that the RADIUS accounting packets are not being seen on the Cisco ISE server.
Which command is the user missing in the switch’s configuration?
In a standalone Cisco ISE deployment, which two personas are configured on a node? (Choose two )
A network administrator must configura endpoints using an 802 1X authentication method with EAP identity certificates that are provided by the Cisco ISE When the endpoint presents the identity certificate to Cisco ISE to validate the certificate, endpoints must be authorized to connect to the network Which EAP type must be configured by the network administrator to complete this task?
Using the SAK Active Directory Federation Services server. The configurations were performed:
• created a new SAML Identity provider profile in Cisco ISE
• exported the service provider Information
• configured all the required Active Directory Federation Services configurations
• Imported the Active Directory Federation Services metadata
• configured groups in the new SAML identity
• added attributes to the new SAML identity provider profile
• configured Advanced Settings in the new SAML identity provider profile
Which two actions must be taken to complete the configuration? (Choose two.)
A laptop was stolen and a network engineer added it to the block list endpoint identity group What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
A Cisco ISE engineer is creating a certificate authentication profile to be used with machine authentication for the network. The engineer wants to be able to compare the user-presented certificate with a certificate stored in Active Directory. What must be done to accomplish this?
What is a valid guest portal type?
Which permission is common to the Active Directory Join and Leave operations?
An administrator has added a new Cisco ISE PSN to their distributed deployment. Which two features must the administrator enable to accept authentication requests and profile the endpoints correctly, and add them to their respective endpoint identity groups? (Choose two )
NO: 37
In which two ways can users and endpoints be classified for TrustSec?
(Choose Two.)
An administrator must deploy the Cisco Secure Client posture agent to employee endpoints that access a wireless network by using URL redirection in Cisco ISE. The compliance module must be downloaded from Cisco and uploaded to the Cisco ISE client provisioning resource. What must be used to upload the compliance module?
An engineer is configuring ISE for network device administration and has devices that support both protocols. What are two benefits of choosing TACACS+ over RADUs for these devices? (Choose two.)
What occurs when a Cisco ISE distributed deployment has two nodes and the secondary node is deregistered?
What is the maximum number of PSN nodes supported in a medium-sized deployment?