300-715 Cisco Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-715 Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What must be configured on the WLC to configure Central Web Authentication using Cisco ISE and a WLC?
What must be configured on the Cisco ISE authentication policy for unknown MAC addresses/identities for successful authentication?
Which Cisco ISE deployment model provides redundancy by having every node in the deployment configured with the Administration. Policy Service, and Monitoring personas to protect from a complete node failure?
An engineer is configuring static SGT classification. Which configuration should be used when authentication is disabled and third-party switches are in use?
A network administrator is currently using Cisco ISE to authenticate devices and users via 802 1X There is now a need to also authorize devices and users using EAP-TLS. Which two additional components must be configured in Cisco ISE to accomplish this'? (Choose two.)
An engineer is assigned to enhance security across the campus network. The task is to enable MAB across all access switches in the network. Which command must be entered on the switch to enable MAB?
The security team identified a rogue endpoint with MAC address 00:46:91:02:28:4A attached to the network. Which action must security engineer take within Cisco ISE to effectively
restrict network access for this endpoint?
An engineer is configuring Cisco ISE for guest services They would like to have any unregistered guests redirected to the guest portal for authentication then have a CoA provide them with full access to the network that is segmented via firewalls Why is the given configuration failing to accomplish this goal?
The security engineer for a company has recently deployed Cisco ISE to perform centralized authentication of all network device logins using TACACS+ against the local AD domain. Some of the other network engineers are having a hard time remembering to enter their AD account password instead of the local admin password that they have used for years. The security engineer wants to change the password prompt to "Use Local AD Password:" as a way of providing a hint to the network engineers when logging in. Under which page in Cisco ISE would this change be made?
An administrator must provide network access to legacy Windows endpoints with a specific device type and operating system version using Cisco ISE profiler services. The ISE profiler services and access switches must be configured to identify endpoints using the dhcp-class-identifier and parameters-request-list attributes from the DHCP traffic. These configurations were performed:
enabled the DHCP probe in Cisco ISE
configured the Cisco ISE PSN interface to receive DHCP packets
configured the attributes in custom profiling conditions
configured a custom profiling policy
configured an authorization rule with permit access
Which action completes the configuration?
An engineer is starting to implement a wired 802.1X project throughout the campus. The task is for failed authentication to be logged to Cisco ISE and also have a minimal impact on the users. Which command must the engineer configure?
A security administrator is using Cisco ISE to create a BYOD onboarding solution for all employees who use personal devices on the corporate network. The administrator generates a Certificate Signing Request and signs the request using an external Certificate Authority server. Which certificate usage option must be selected when importing the certificate into ISE?
What happens when an internal user is configured with an external identity store for authentication, but an engineer uses the Cisco ISE admin portal to select an internal identity store as the identity source?
Which file extension is required when deploying Cisco ISE using a ZTP configuration file in Microsoft Hyper-V?
Which two VMware features are supported on a Cisco ISE virtual appliance? (Choose two.)
An administrator for a small network is configuring Cisco ISE to provide dynamic network access to users. Management needs Cisco ISE to not automatically trigger a CoA whenever a profile change is detected. Instead, the administrator needs to verify the new profile and manually trigger a CoA. What must be configuring in the profiler to accomplish this goal?
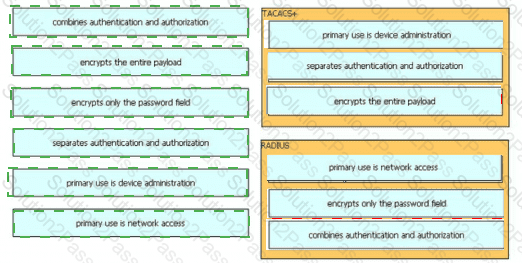
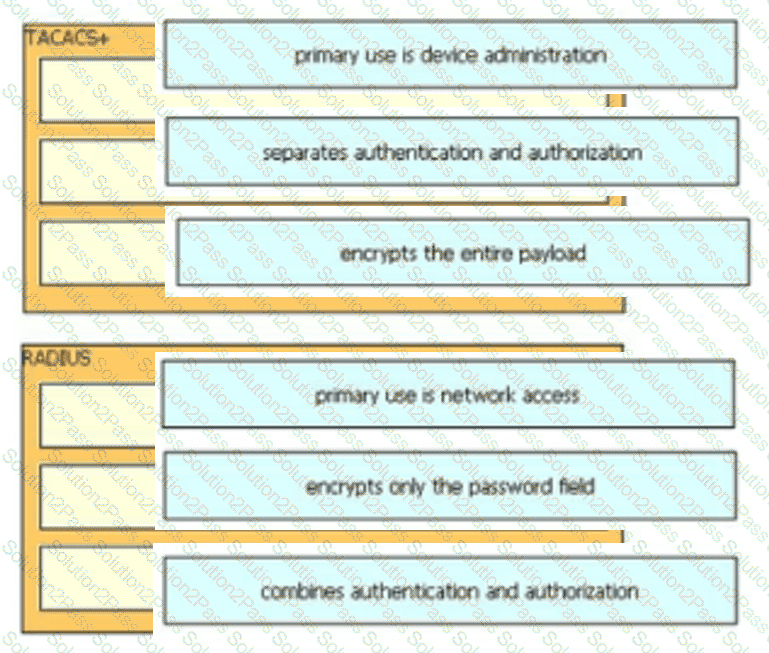
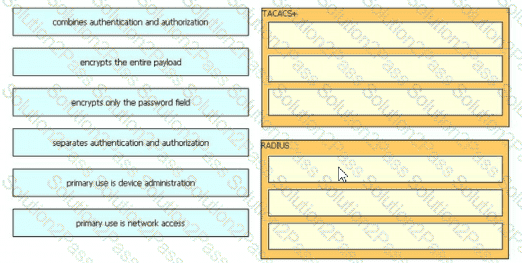
Drag and drop the description from the left onto the protocol on the right that is used to carry out system authentication, authentication, and accounting.
A network engineer has been tasked with enabling a switch to support standard web authentication for Cisco ISE. This must include the ability to provision for URL redirection on authentication Which two commands must be entered to meet this requirement? (Choose two)
An administrator is configuring a new profiling policy within Cisco ISE The organization has several endpoints that are the same device type and all have the same Block ID in their MAC address. The profiler does not currently have a profiling policy created to categorize these endpoints. therefore a custom profiling policy must be created Which condition must the administrator use in order to properly profile an ACME Al Connector endpoint for network access with MAC address
An administrator adds a new network device to the Cisco ISE configuration to authenticate endpoints to the network. The RADIUS test fails after the administrator configures all of the settings in Cisco ISE and adds the proper configurations to the switch. What is the issue"?