300-730 Cisco Implementing Secure Solutions with Virtual Private Networks (SVPN) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 300-730 Implementing Secure Solutions with Virtual Private Networks (SVPN) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A network engineer is setting up Cisco AnyConnect 4.9 on a Cisco ASA running ASA software 9.1. Cisco AnyConnect must connect to the Cisco ASA before the user logs on so that login scripts can work successfully. In addition, the VPN must connect without user intervention. Which two key steps accomplish this task? (Choose two.)
A TCP based application that should be accessible over the VPN tunnel is not working. Pings to the appropriate IP address are failing.

Based on the output, what is a fix for this issue?
Where must an engineer configure a preshared key for a site-to-site VPN tunnel configured on a Cisco ASA?
Users are getting untrusted server warnings when they connect to the URL https://asa.lab from their browsers. This URL resolves to 192.168.10.10, which is the IP address for a Cisco ASA configured for a clientless VPN. The VPN was recently set up and issued a certificate from an internal CA server. Users can connect to the VPN by ignoring the message, however, when users access other webservers that use certificates issued by the same internal CA server, they do not experience this issue. Which action resolves this issue?
Refer to the exhibit.
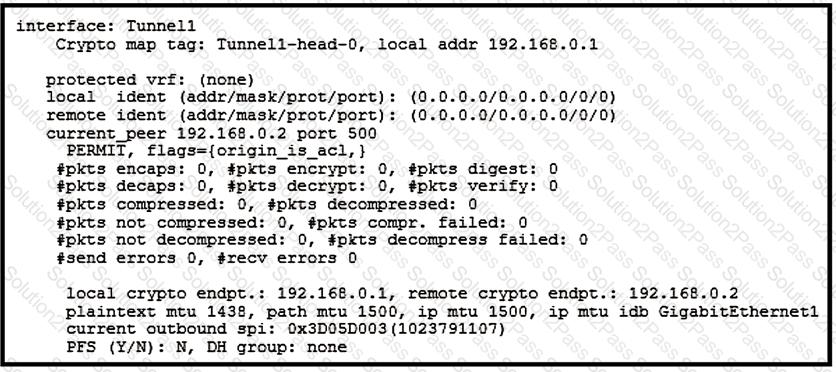
Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit? (Choose two.)
Refer to the exhibit.
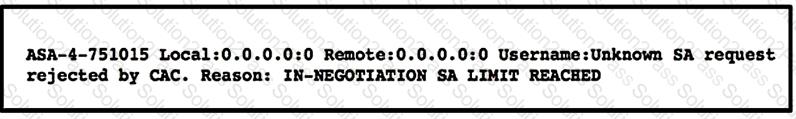
A customer cannot establish an IKEv2 site-to-site VPN tunnel between two Cisco ASA devices. Based on the syslog message, which action brings up the VPN tunnel?
Which two parameters help to map a VPN session to a tunnel group without using the tunnel-group list? (Choose two.)
Which two changes must be made in order to migrate from DMVPN Phase 2 to Phase 3 when EIGRP is configured? (Choose two.)
On a FlexVPN hub-and-spoke topology where spoke-to-spoke tunnels are not allowed, which command is needed for the hub to be able to terminate FlexVPN tunnels?
Which statement about GETVPN is true?
Refer to the exhibit.
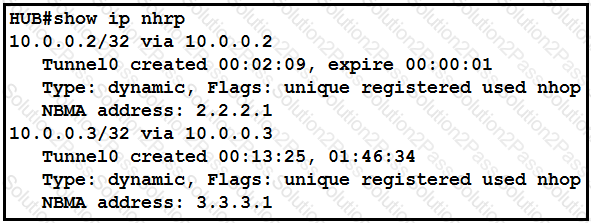
The DMVPN tunnel is dropping randomly and no tunnel protection is configured. Which spoke configuration mitigates tunnel drops?
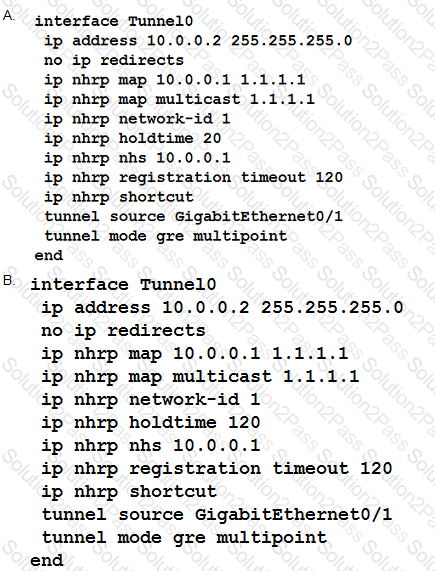
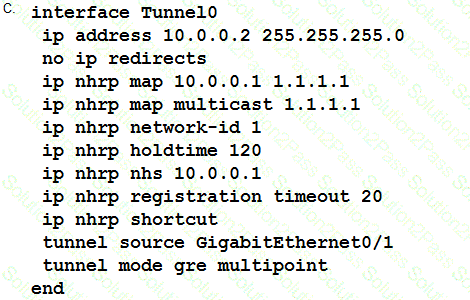
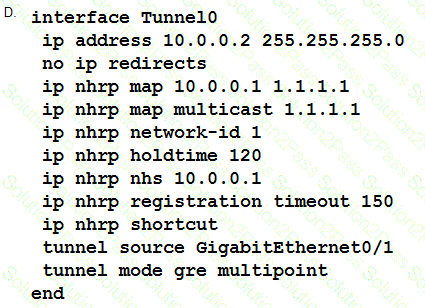
Which method dynamically installs the network routes for remote tunnel endpoints?
