300-910 Cisco Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-910 Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which method is a safe way to provide a username/password combination to an application running as a service in a Docker container?
Which two statements about Infrastructure as Code are true? (Choose two.)
A development team is using Cl/CD during application development During the latest releases runtime vulnerabilities have been indicated to address these vulnerabilities. a complete redesign oí the affected applications were required To overcome this issue black box testing has been proposed. What must be used to automate this testing within a Cl/CD pipeline.
A DevOps engineering wants to build an application implementation based on the CI/CD pipeline model. Which service should be used to provide hosted continuous service for open and private projects?
Refer to the exhibit.
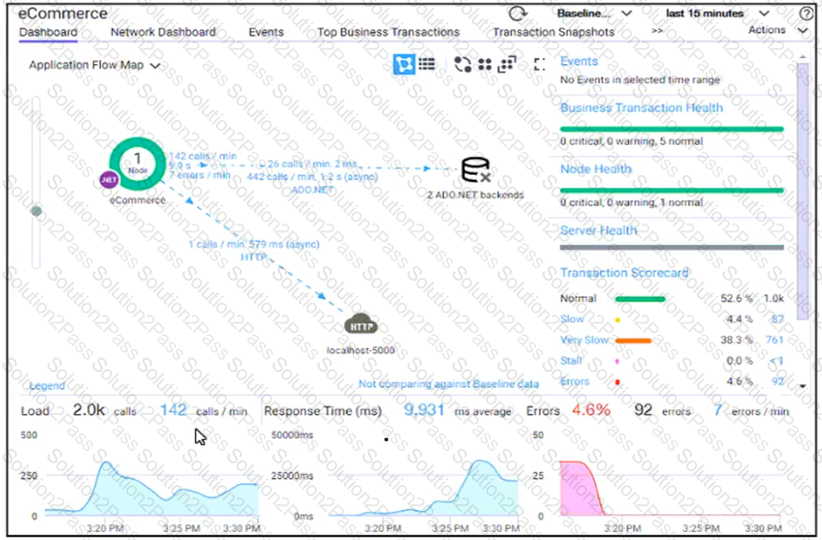
An application for data storing and processing has been created. The application is time-sensitive and manages confidential data AppDynamics identifies error transactions within a distributed application.
Which action will help resolve the errors?
What is a benefit of Infrastructure as Code for the cloud?
Refer to the exhibit.
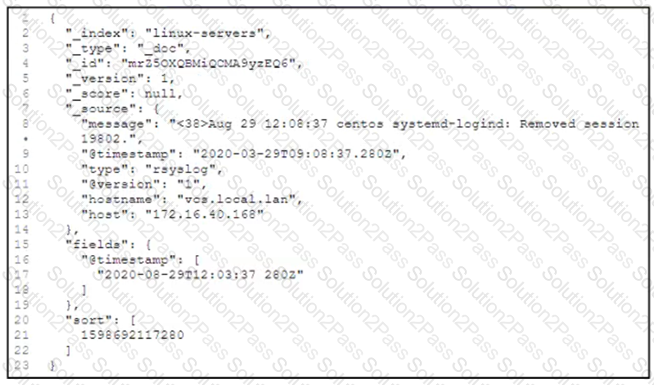
The JSON object represents a single entry on a centralized log server, but log data cannot be processed because of the format.
What causes the issue?
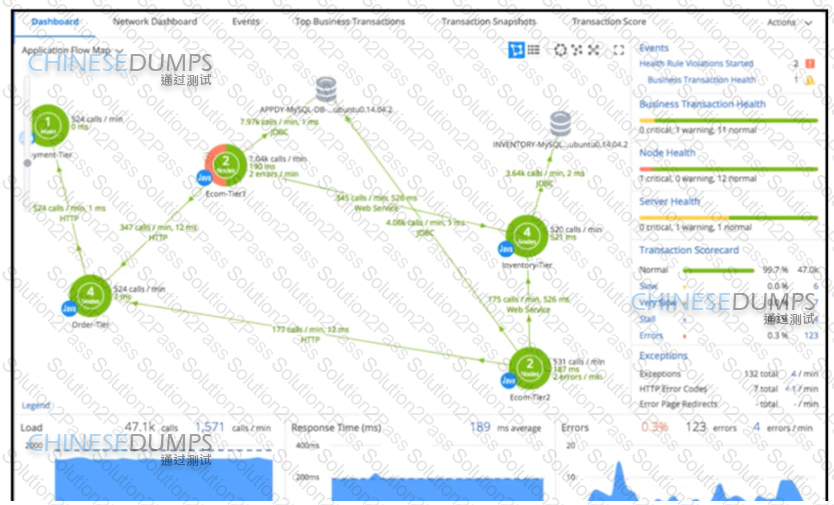
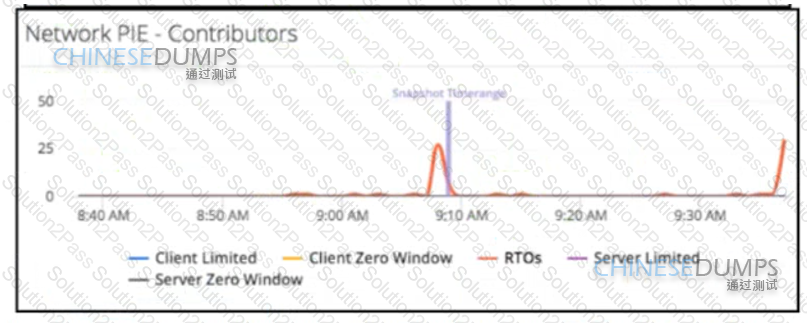
Refer to the exhibit A DevOps engineer is responsible for monitoring a mission-critical app During normal operations, when opening the application dashboard, it has been noticed that Ecom-Tier1 suddenly turns partially red Which action must be taken to address the Ecom-Tier1 turning red?
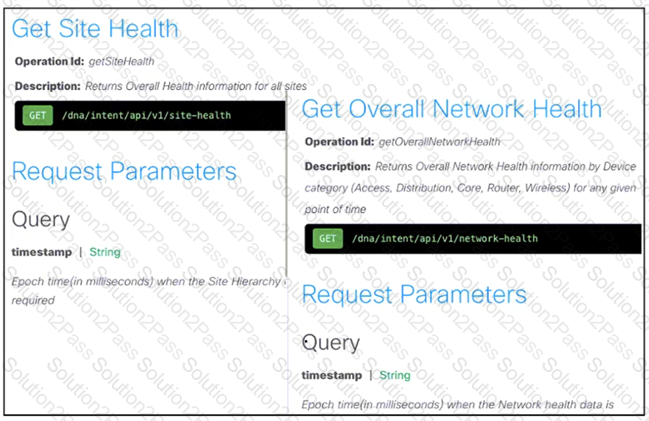
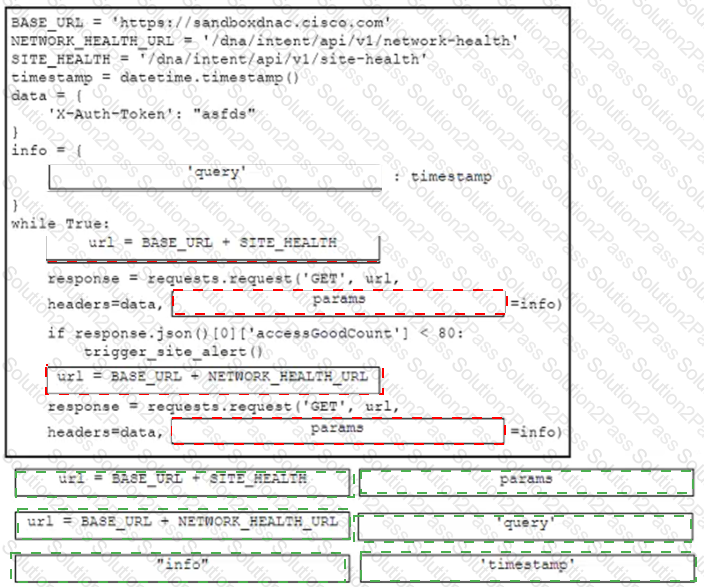
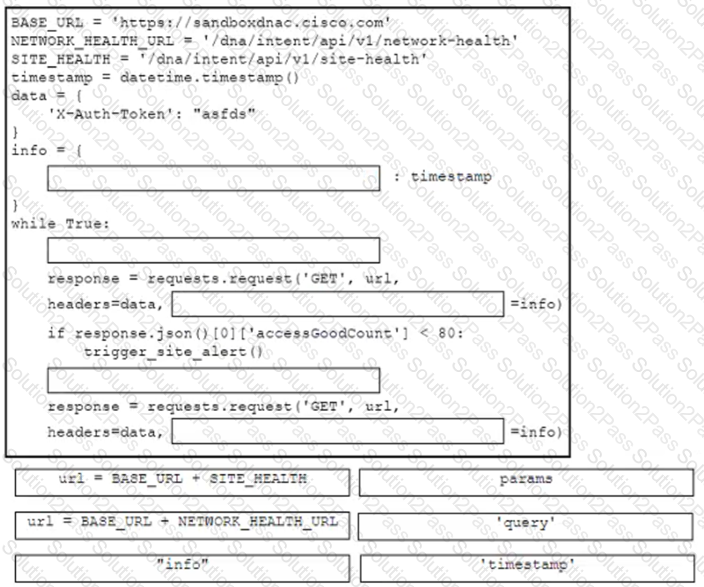
Refer to the exhibit. A developer is creating a health check monitoring script that queries information from the Cisco DNA Center platform. The script must trigger an alert if a site health statistic named accessGoodCount drops below 80 and if a network statistic named latestHealthScore is 95 or less.
Drag and drop the code snippets from the bottom onto the blanks in the code to monitor the site and network health on a Cisco DNA Center platform instance. Options may be used more than once. Not all options are used.
Which two actions help limit the attack surface of your Docker container? (Choose two.)
AppDynamics is being used to monitor your distributed Python application. Each individual container of the application is instrumented with an AppD agent. Which two configuration variables uniquely determine the module being monitored? (Choose two.)
Refer to the exhibit.
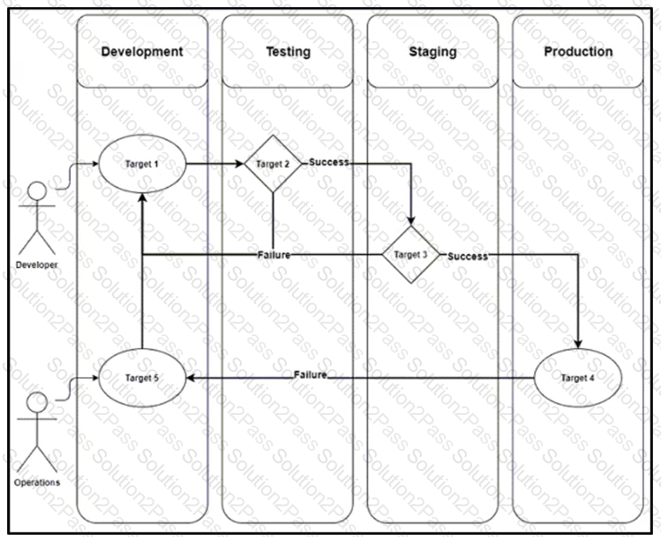
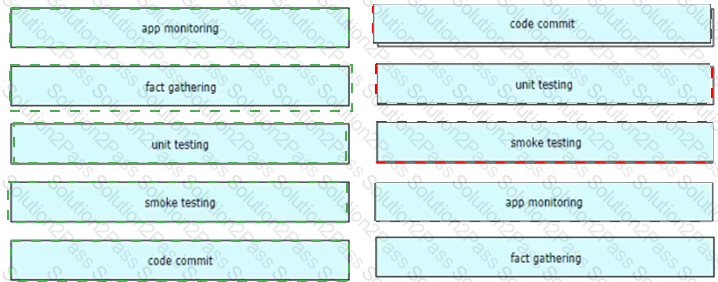
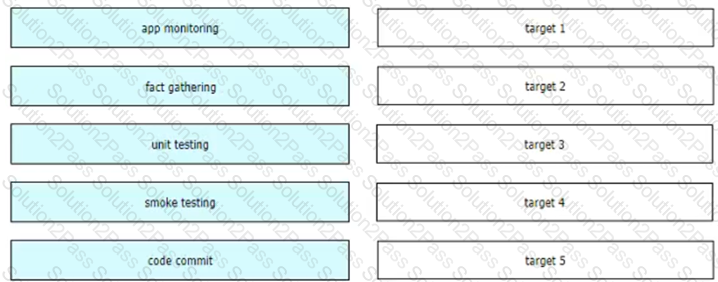
A development team is designing an application that will include multiple components and services. To streamline the process, CO/CD must be implemented.
Drag and drop the CI/CD pipeline stages from the left onto the targets on the right.
A developer wants to deploy a highly available web server cluster and decides to put a load balancer in front of multiple clustered nodes that run the same web service. The goal is for the load balancer to take in users and distribute the load across the whole cluster.
What kind of high-availability configuration is the developer running?
Which Dockerfile yields the most predictable builds?
A)
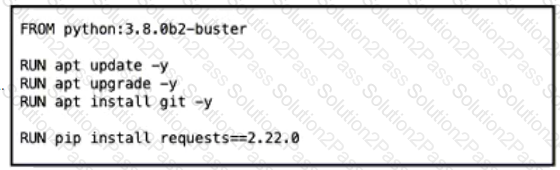
B)

C)
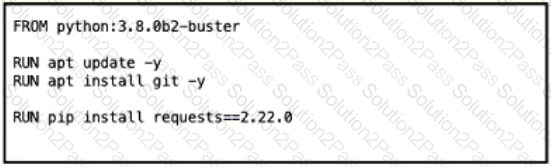
D)
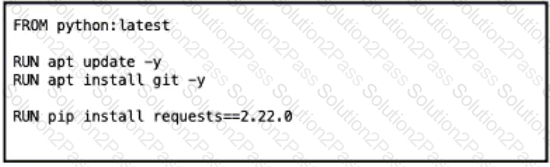
A DevOps engineer must build a Docker image to containerize an application. Then the image must be pushed to a repository on Docker Hub in a CI/CD pipeline using GitHub Actions.
Which approach securely encrypts the Docker Hub access token as an environment variable within the CI/CD pipeline?
What is an advantage of using configuration management tools to automate infrastructure services?
Microservices architecture pattern has been applied and the system has been architected as a set of services. Each service is deployed as a set of instances for throughput and availability. In which two ways are these services packaged and deployed? (Choose two.)
A developer is nearing the end of a software development cycle and is ready to deploy the software. The customer wants to continue using a secure software development lifecycle methodology and must plan for postproduction components. Which two areas should be the developer address? (Choose two.)
A company has experienced serious growth and the hosted applications are getting more and more hits. Based on the increased work load, applications have started to show signs of reduced performance, which is affecting the user experience.
Which two server metrics should be tracked to ensure that the customer experience remains within acceptable limits? (Choose two.)