350-901 Cisco Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 350-901 Developing Applications using Cisco Core Platforms and APIs (DEVCOR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit.


An engineer writes a script to retrieve data from a REST API and must build support for cases where the response that contains data from the server may take a longer time than normal Which code must be added to the snippet where the code is missing to catch such a timeout?
Refer to the exhibit.
A network administrator copies SSL certificates to a Cisco NX-OS switch. An Ansible playbook is created to enable NX-API, which will use the new certificate. In the group_vars/vars.yml file, which code snippet must be used to define the properly formatted variables?
A)
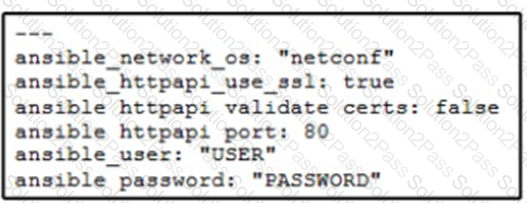
B)
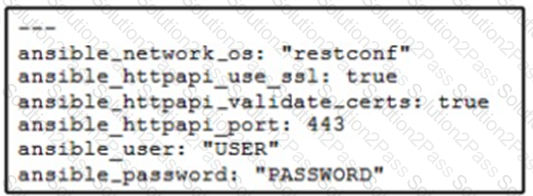
C)
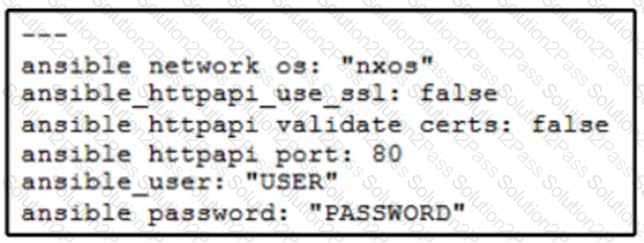
D)
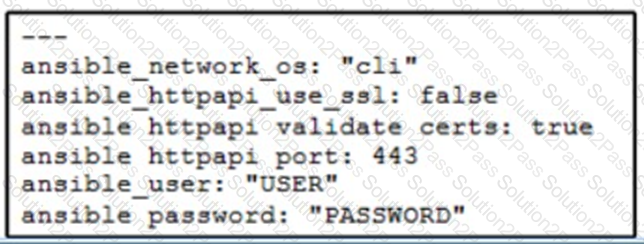
Refer to the exhibit.
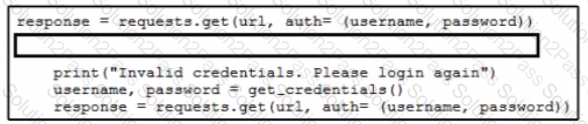
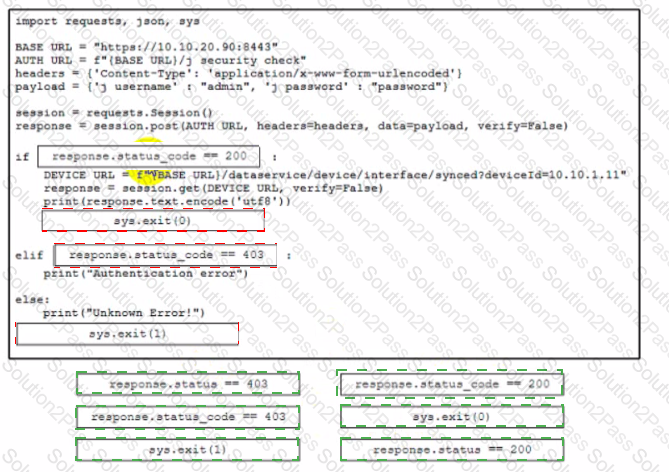
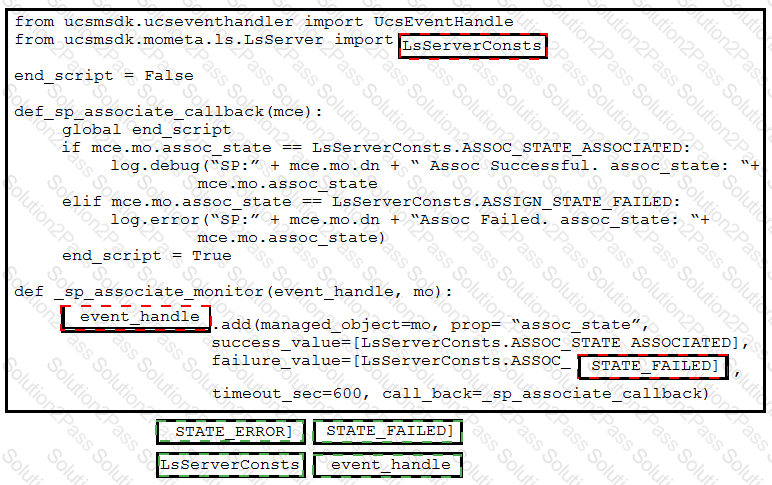
Which code snippet must be added to the blank in the code to automate the evaluation and handling of errors due to wrong credentials when Basic Authorization is used?
A)

B)

C)

D)

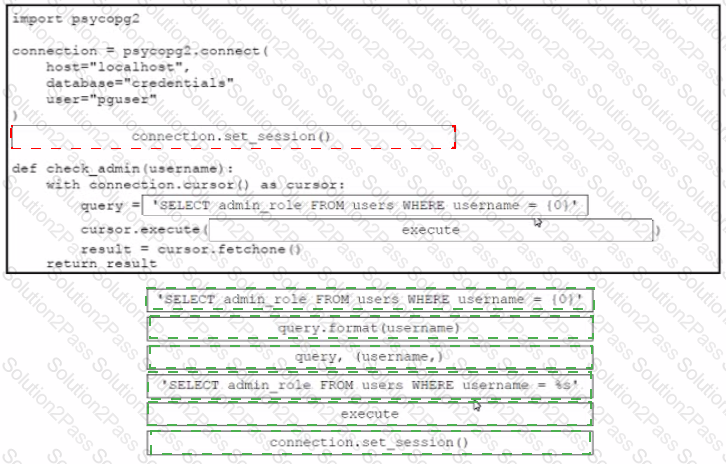
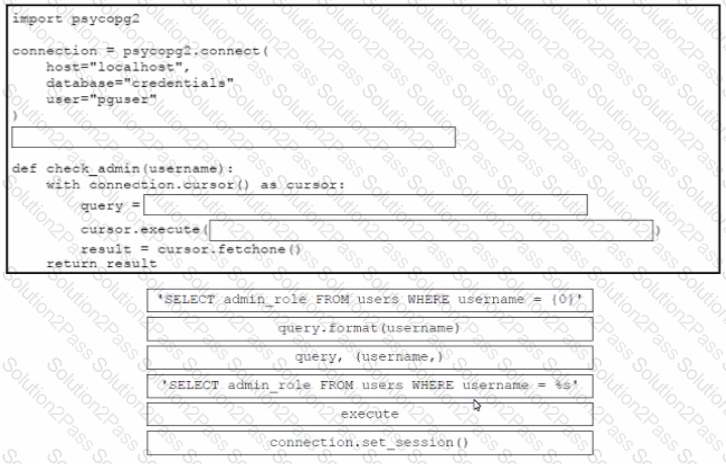
Drag and drop the code from the bottom onto the box where the code is missing in the Python code to query for user permissions while mitigating against SQL Injection Not all options are used.
What is an effective logging strategy according 10 the 12-factor app tenets?
A developer is creating a Python script to analyze errors during REST API call operations. The script will be used with Cisco solution and devices. Drag and drop the code from the bottom to the box where the code is missing to implement control flow for handling unrecoverable REST API calls. Not all options are used.
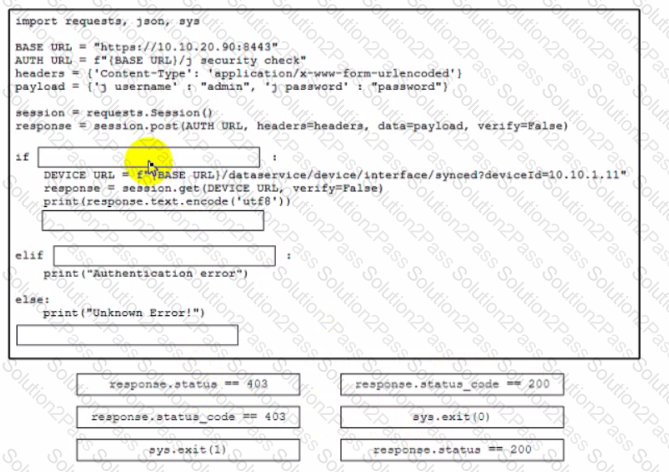
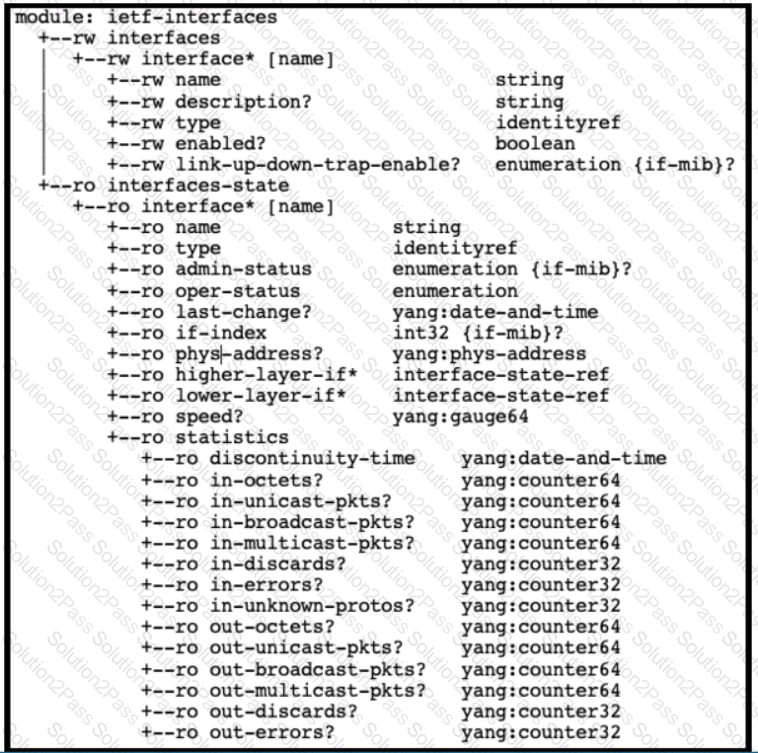
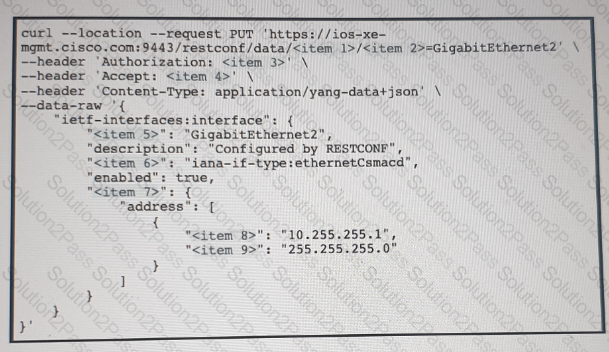
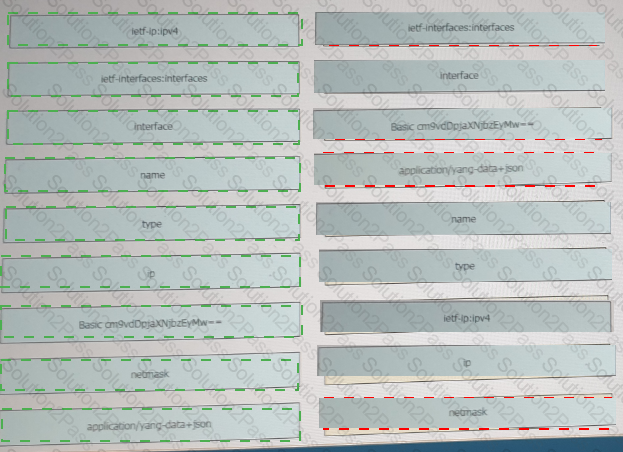
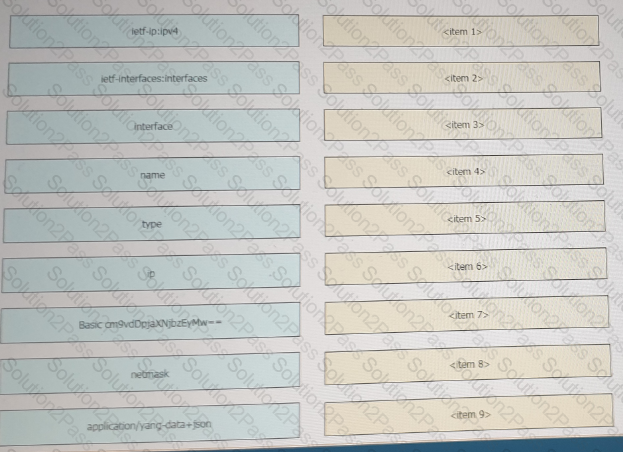
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question. Drag and drop the correct code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the cURL script that will use RESTCONF to update an interface on a CISCO IOS XE device.
Refer to the exhibit.
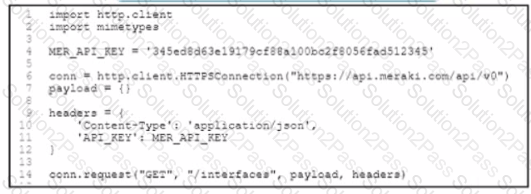
A developer created a Python script to retrieve information about Meraki devices in a local network deployment After requesting a security review of the code the security analyst has observed poor secret storage practices What is the appropriate secret storage approach''
Refer to the exhibit.
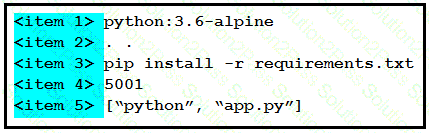
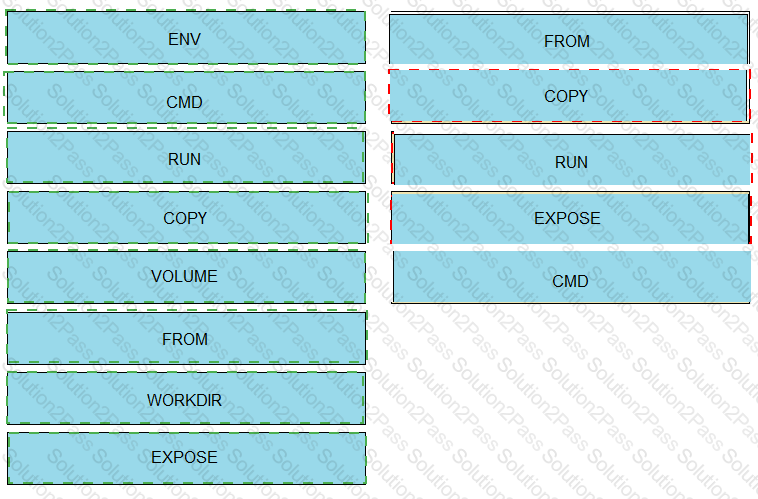
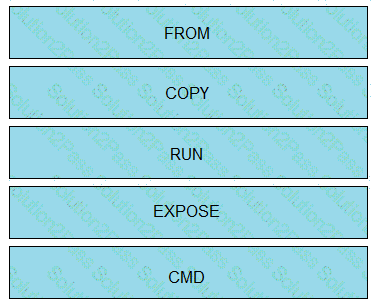
Drag and drop the correct parts of the Dockerfile from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the Dockerfile to successfully build and deploy a container running a Python application. Not all parts of the Dockerfile are used.
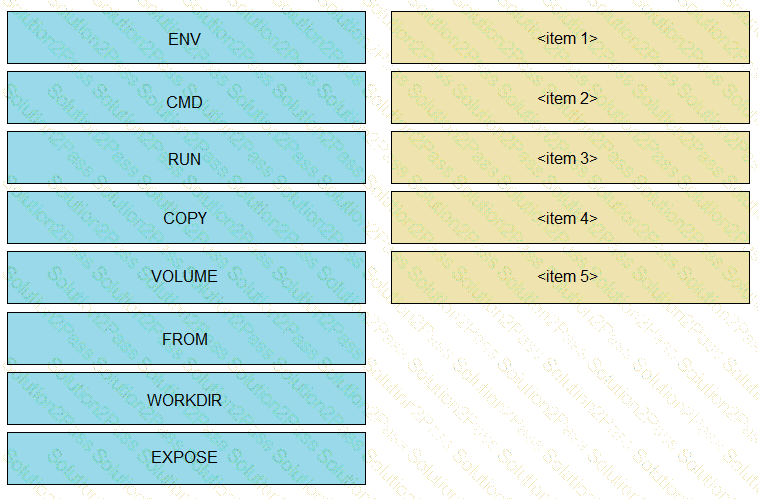
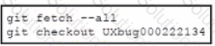
A development team is working on a bug fix in a remote branch named "UXbug000222134' and the current working primary branch is named ,prod409024967’ A developer who just joined the learn needs to checkout the remote branch Which Git commands must be used?
A)

B)

C)

D)
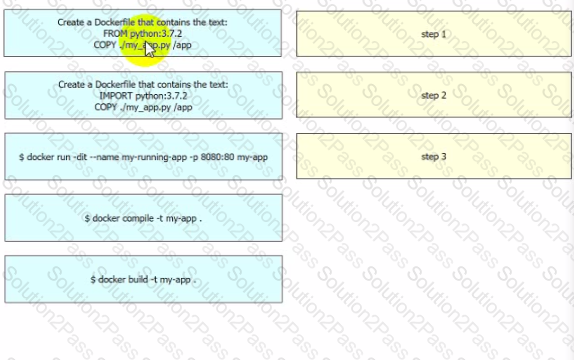
Drag and drop the steps from the left into the order on the right to build and run a customized Python DocKer image. Not all options are used
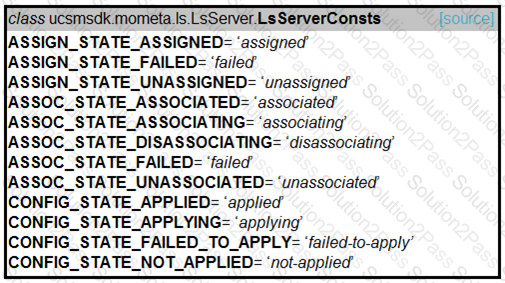
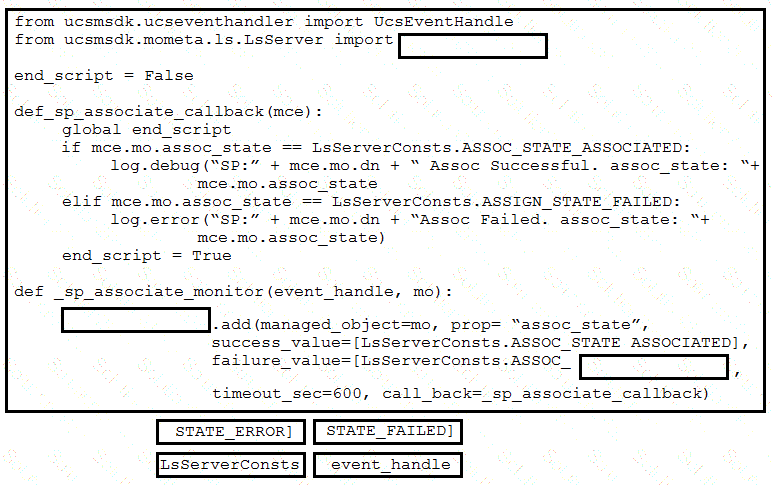
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the code to provision a new UCS server. Not all options are used.
A developer is designing a modem, distributed microservice enterprise application. The application will be integrating with other systems and focus on a large deployment, so control of API calls is necessary. What is the best practice to reduce application response latency and protect the application from excessive use?
Refer to the exhibit.

An architect wrote an application to collect device information from the Cisco Meraki Dashboard API. Every time a network change occurs the application collects information and records new endpoint MAC addresses. The application stopped working after the locations and network equipment of a competitor were acquired. Which application approach must be applied to reduce latency and rate limiting?
How is an OAulh2 three-legged authentication flow initiated?
Refer to the exhibit.
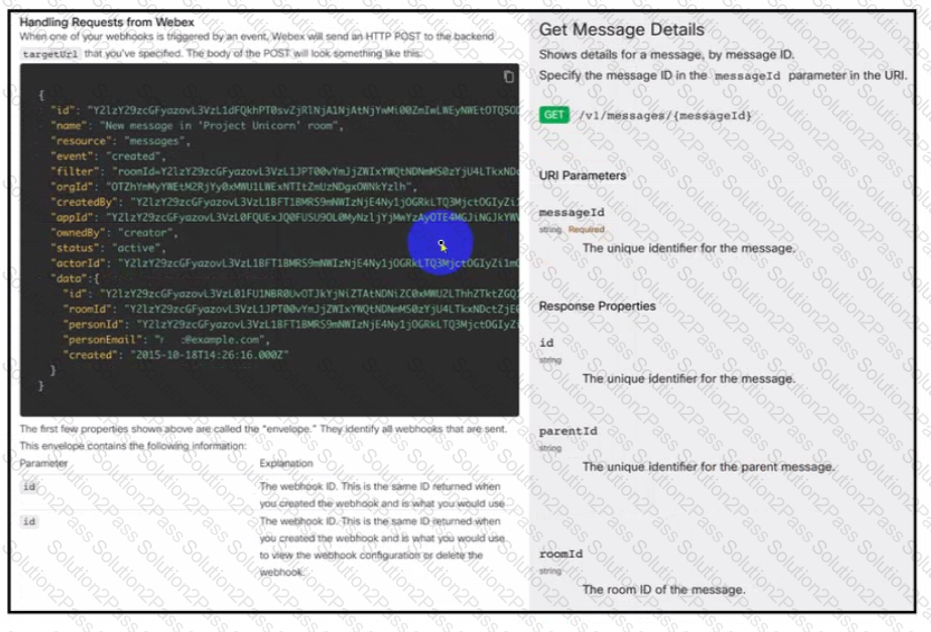
Drag and drop the code from the bottom onto the box where the code is missing to complete the API request. An engineer is using this API request to implement Chat-Ops to generate notifications m a Webex space by using webhooks. Not all options are used.
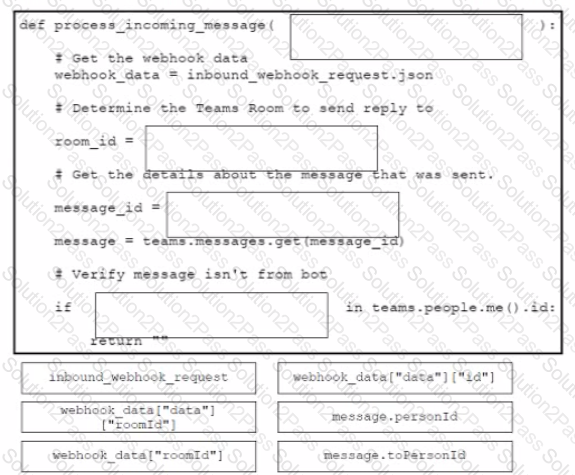
Refer to the exhibit.
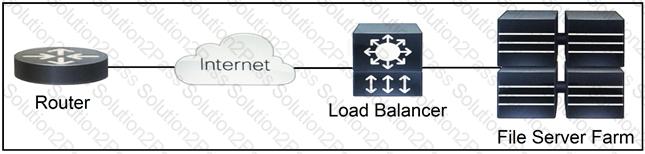
Which two functions are performed by the load balancer when it handles traffic originating from the Internet destined to an application hosted on the file server farm? (Choose two.)
An application has initiated an OAuth authorization code grant flow to get access to an API resource on behalf of an end user.
Which two parameters are specified in the HTTP request coming back to the application as the end user grants access? (Choose two.)
Refer to the exhibit.

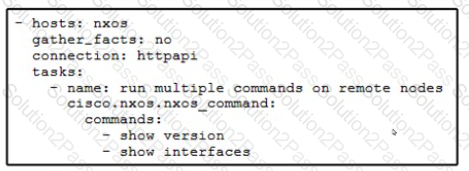
Which type of python dependency file is shown?
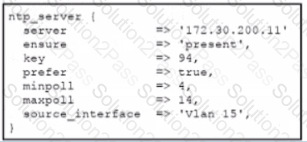
Which Puppet manifest changes the NTP server and generates the traffic from VLAN 15?
A)

B)

C)

D)