350-901 Cisco Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 350-901 Developing Applications using Cisco Core Platforms and APIs (DEVCOR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
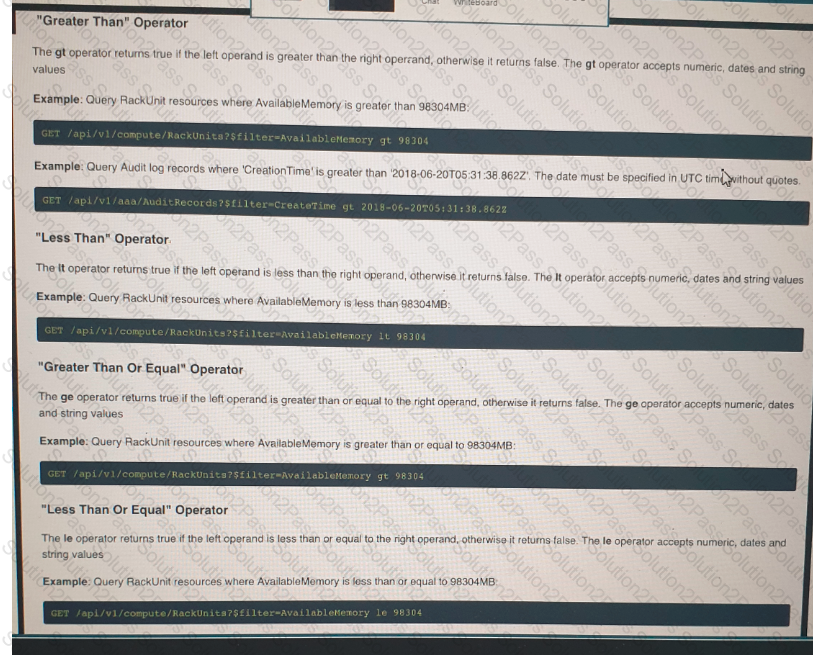
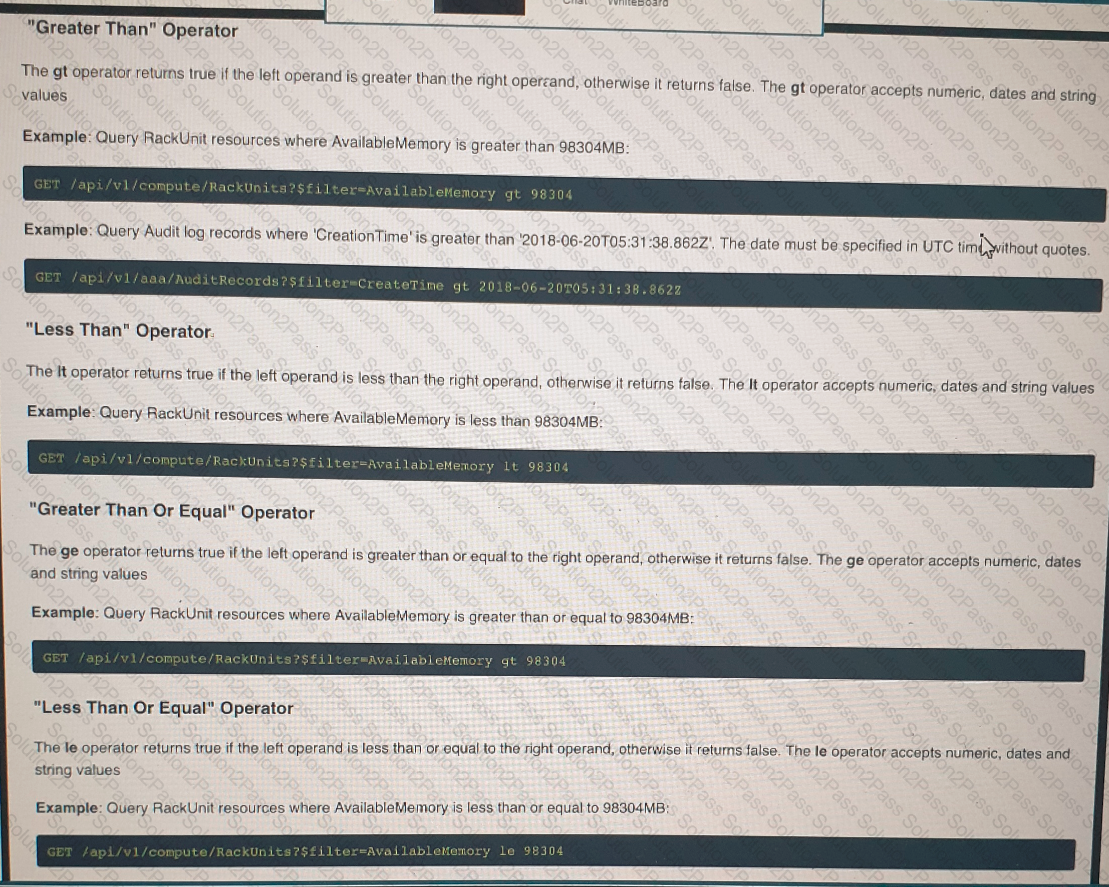
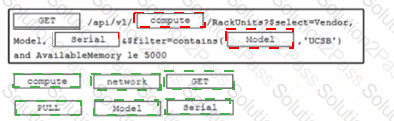
Click on the GET Resource button above to view resources that will help with this question. An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB. Which REST API call accomplishes this task?
A user is receiving a 429 Too Many Requests error. Which scheme is the server employing that causes this error?
Click on the resource lab in the top left comer to view resources to help with this question An engineer is managing a data center with 6000 Cisco UCS servers installed and running The engineer is asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB Drag and drop the code from the bottom onto the blanks in the code snippet to construct a REST API call to accomplish this task Not all options are used.

A developer must deploy a containerized application foe network device inventory management. The developer sets up a Kubernetes duster on two separate hypervisors. The SLA is not currently meeting a specified maximum value for network latencyjitter CPU/memory and disk I/O are functioning property. Which two design approaches resolve the issue'' (Choose two.)
What securely stores and encrypts the API keys and tokens that are used for an application deployment?
Application sometimes store configuration as constants in the code, which is a violation of strict separation of configuration from code. Where should application configuration be stored?
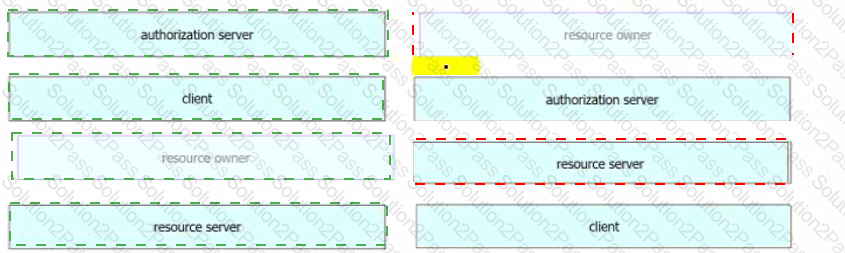
Refer to the exhibit.
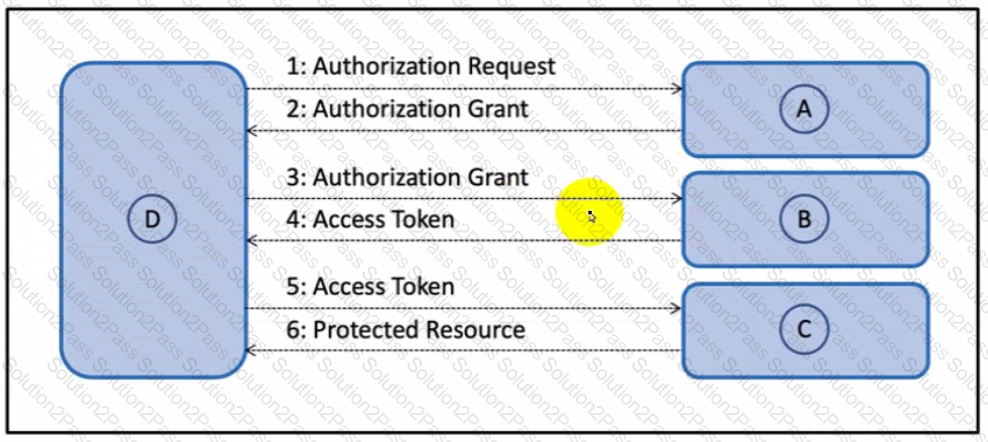
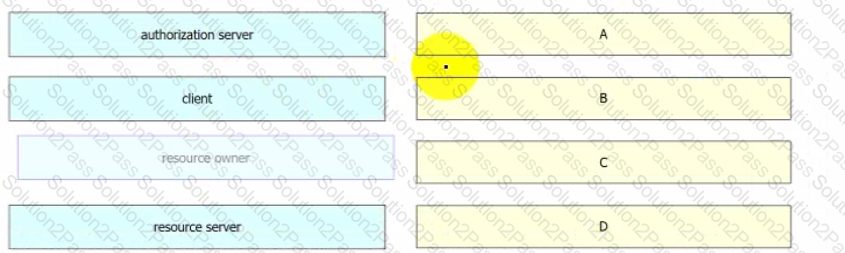
Drag and drop the components from the Oauth2 authorization protocol flow on the left onto the letter that matches the location in the exhibit.
A developer wants to automate virtual infrastructure to provision and manage it. The system will be implemented m large-scale deployment while offering redundancy and scalability with ease of management The solution must meet these requirements:
• Support the provisioning of up to 500 new virtual machines into private datacenters or the public cloud
• Support the modeling of a complex environment that consists of multiple virtual machines while supporting disaster recovery
• Maintain steady-state environments
Which configuration management solution must the developer use?
Refer to the exhibit.
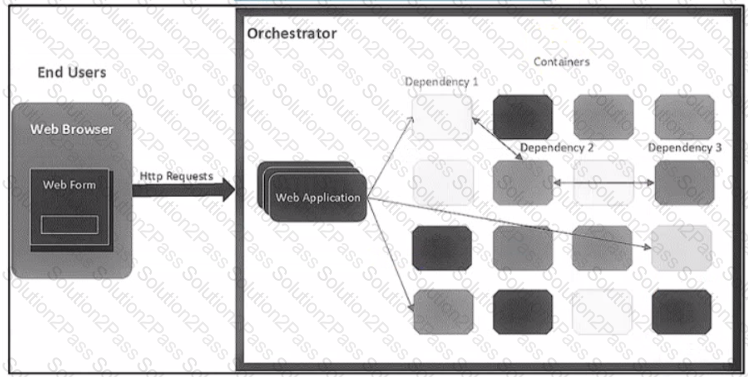
The application follows a containerized microservices architecture that has one container per microservice. The microservices communicate with each other by using REST APIs The double-headed arrows m the diagram display chains of synchronous HTTP calls needed for a single use/request Which action ensures the resilience of the application in the scope of a single user request?
Refer to the exhibit.
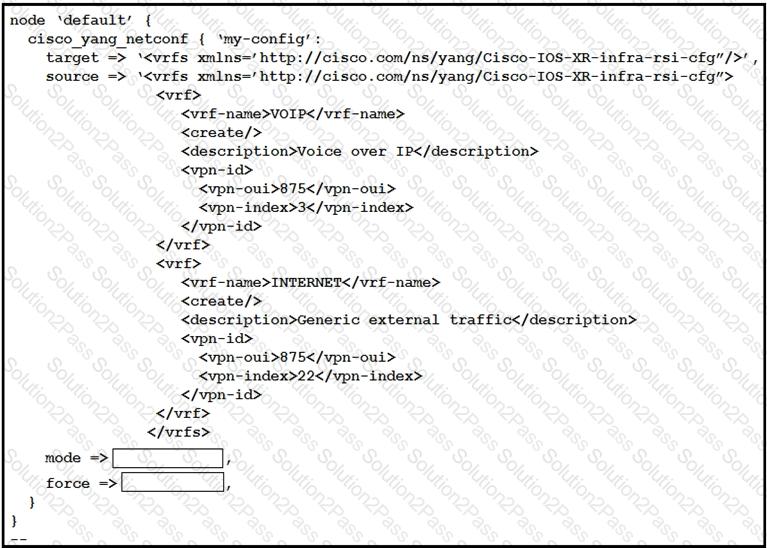
This script uses ciscoyang to configure two VRF instances on a Cisco IOS-XR device using the Yang NETCONF type.
Which two words are required to complete the script? (Choose two.)
How is AppDynamics used to instrument an application?
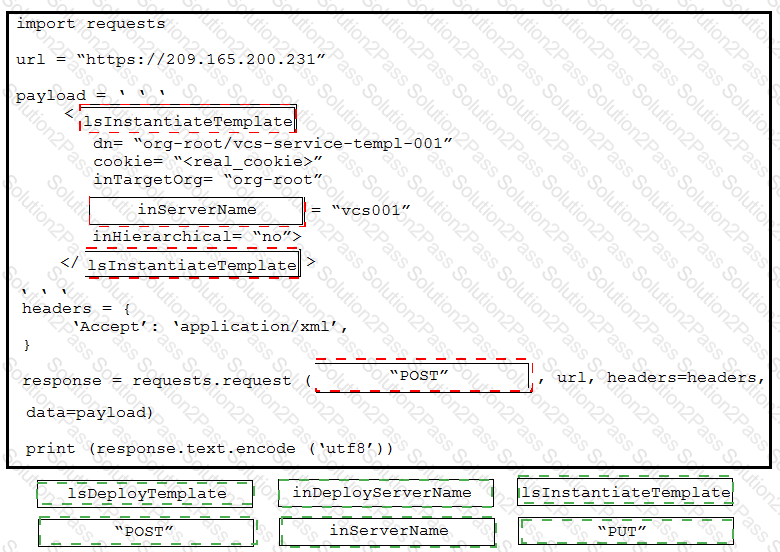
Drag and drop the code from the bottom onto the box where the code is missing to provision a new Cisco Unified Computing System server by using the UCS XML API. Options may be used more than once. Not all options are used.
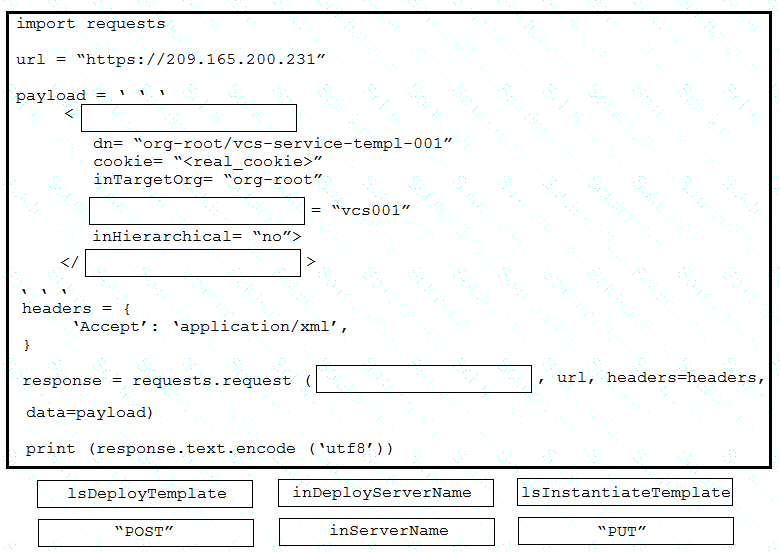
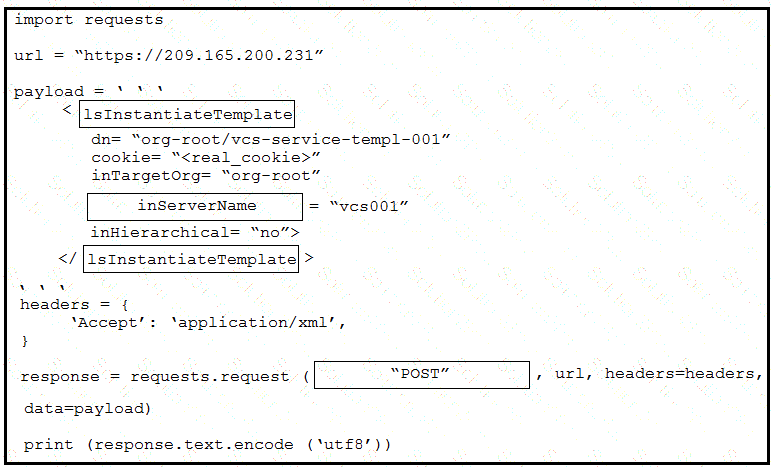
Refer to the exhibit.
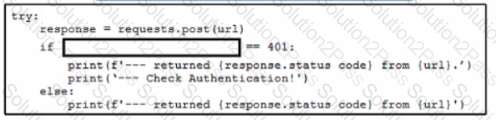
A network engineer writes a script to test authentication workflow using Python and REST API. The engineer wants to ensure that the script handles expected errors by matching output to HTTP status codes The scnpt uses the Python requests module. Which line of code must be added on the snippet where the code is missing?
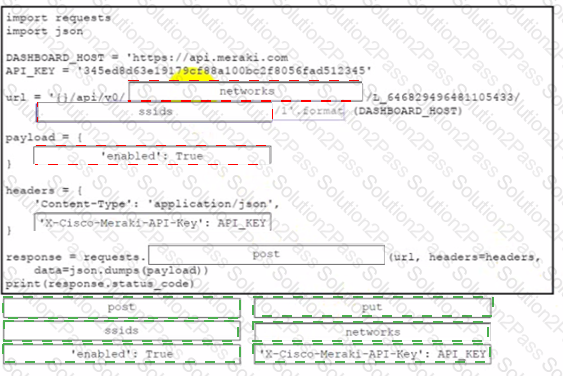
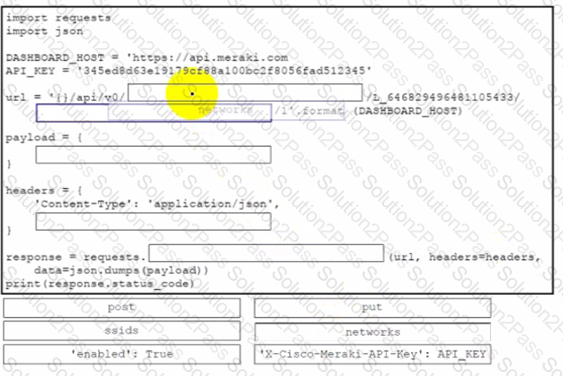
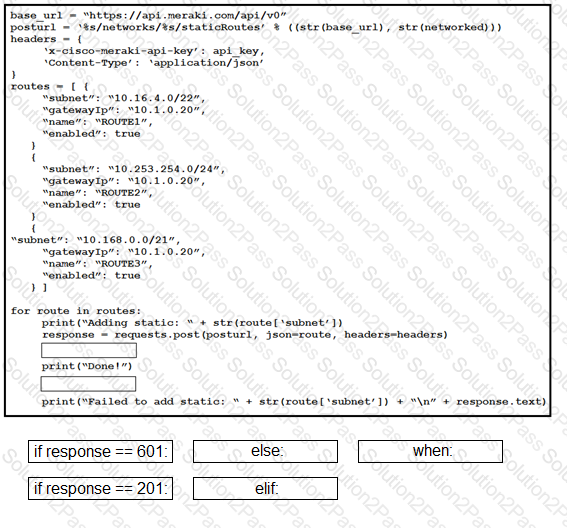
Drag and drop the code from the bottom onto the box where the code is missing to enable an SSID by using the Cisco Meraki Dashboard API. Not all options are used.
Drag and drop the code from the bottom onto the where the code is missing to create a host object by using the Cisco Firepower Device Manager API. Not all options are used.

An engineer needs to automate the configuration on a Cisco NX-OS switch. The solution must meet these requirements:
•Ansible is used
•The transport protocol is encrypted
•Support for Asynchronous requests.
Which two access mechanisms must be used? (Choose two.)
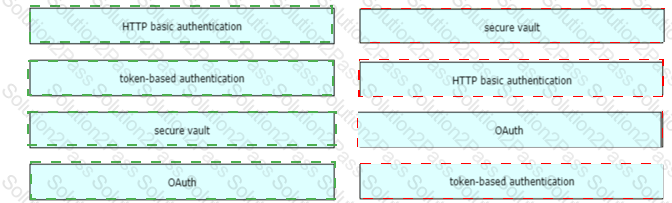
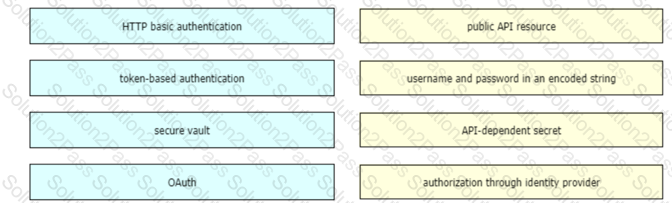
Drag and drop the REST API authentication method from the left to the description on the right
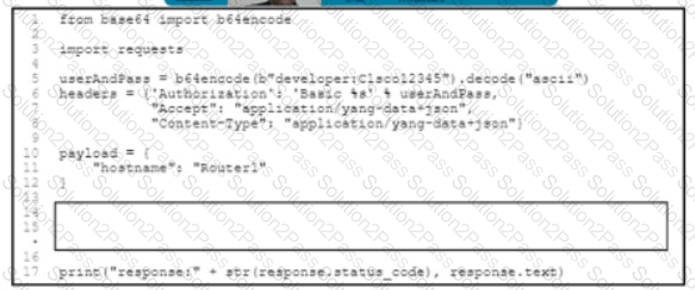
Refer to me exhibit The Python code manages a Cisco CSR 1000V router Which code snippet must be placed in the blank m the code to update the current configuration of the targeted resource?
A)

B)
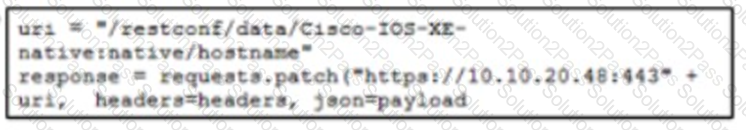
C)

D)

Refer to the exhibit.
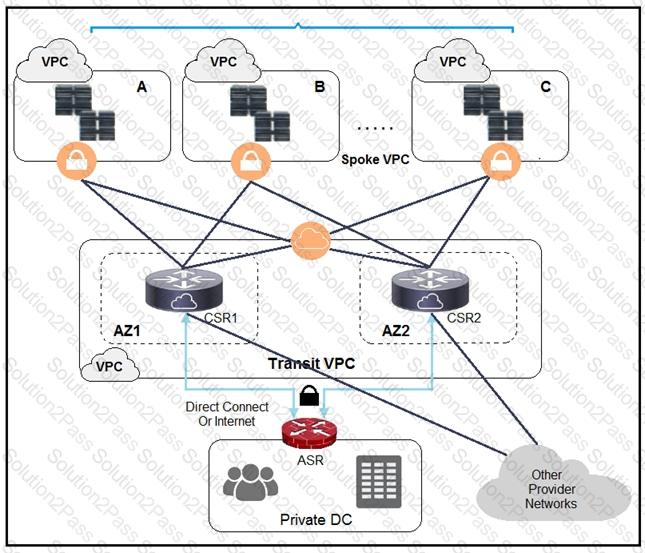
A company has extended networking from the data center to the cloud through Transit VPC.
Which two statements describe the benefits of this approach? (Choose two.)
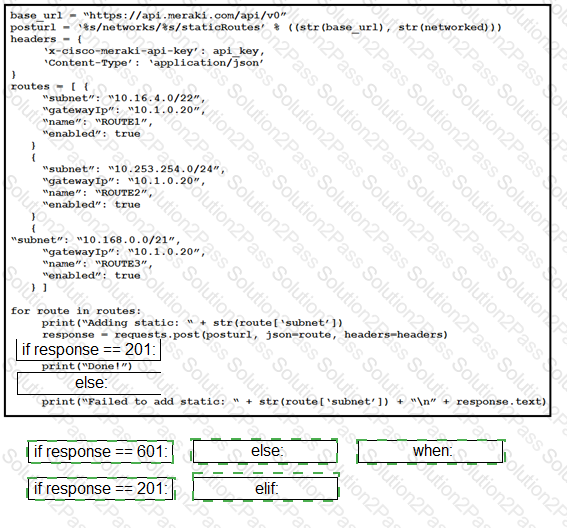
Drag and drop the expressions from below onto the code to implement error handling. Not all options are used.
 Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated