350-901 Cisco Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 350-901 Developing Applications using Cisco Core Platforms and APIs (DEVCOR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
AppGigabitEthernet interface is used as data port for a container on a Cisco Catalyst 9000 Series Switch. Which two interface configuration options should be used? (Choose two.)
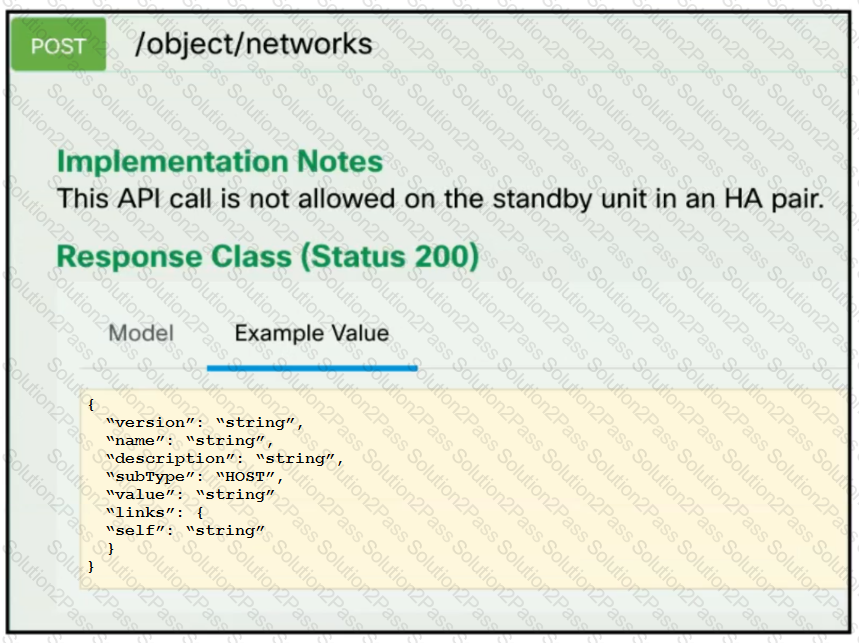
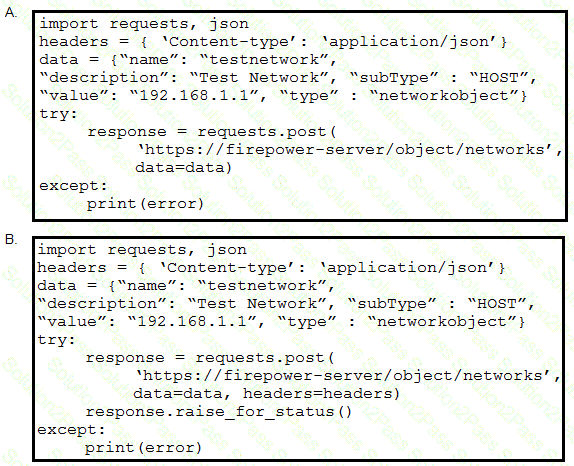
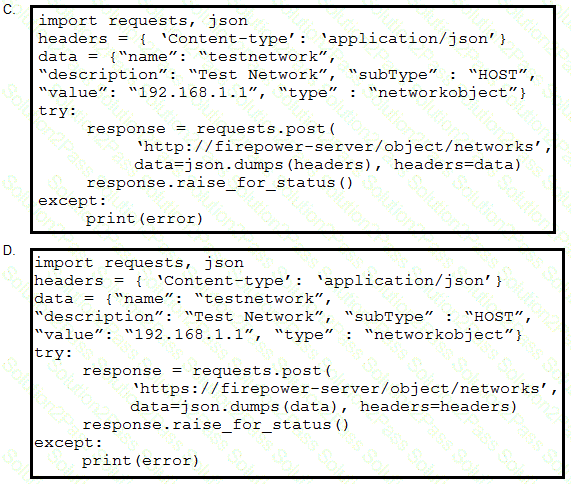
Refer to the exhibit. A developer must create a new network object named testnetwork by using the Cisco Firepower Device Management API. The script must also handle any exceptions that occur during the request and print out any resulting errors. Which script must be used?
Refer to the exhibit.
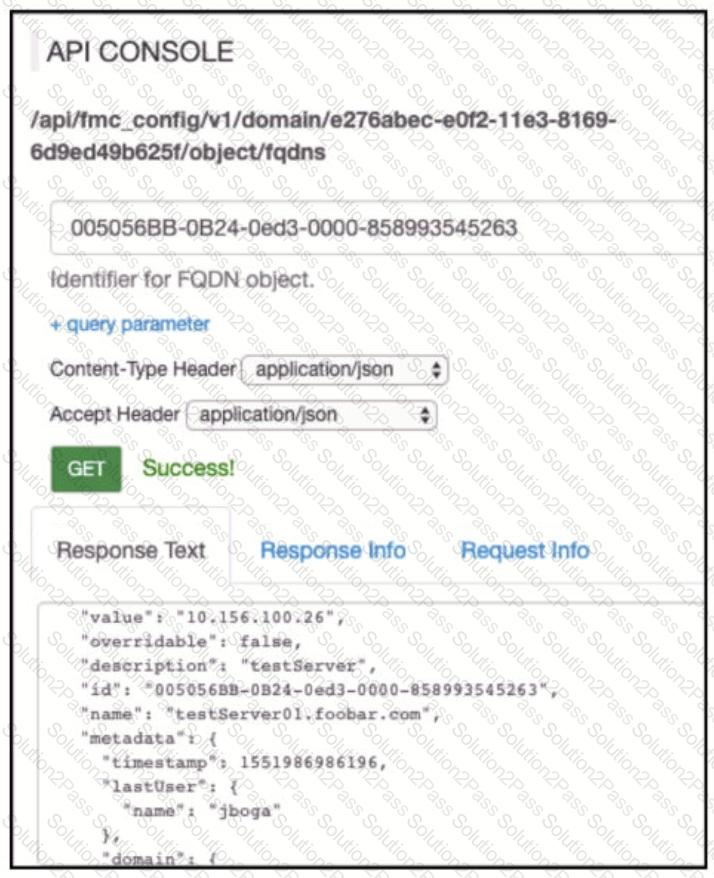
Which AP! call does an engineer use to delete the FQDN object?
What is a consideration for using gRPC as the model-driven telemetry protocol on a Cisco IOS XE device?
Which two techniques protect against injection attacks? (Choose two.)
An architect must optimize traffic that targets a popular API endpoint Currently, the application downloads a large file hourly, but often the file is unchanged and the download causes unnecessary load and delays Which cURL command must be used to determine the last modified date of the file and to optimize the API usage?
An engineer needs to configure an interface named GigabitEthernet3 with an IP address on several RESTCONF-enabled Cisco IOS XE devices. Which code snippet must be placed in the blank in the code to meet this requirement?
An organization manages a large cloud-deployed application that employs a microservices architecture across multiple data centers. Reports have received about application slowness. The container orchestration logs show that faults have been raised in a variety of containers that caused them to fail and then spin up brand new instances.
Which two actions can improve the design of the application to identify the faults? (Choose two.)
An application is hosted on Google Kubernetes Engine. A new JavaScript module is created to work with the existing application. Which task is mandatory to make the code ready to deploy?
Refer to the exhibit , The command docker build -tag=friendlyhello . is run to build a docker image from the given Dockerfile,
requirements,txt, and app.py, Then the command docker run -p 4000:80 friendlyhello is executed to run the application. Which URL is entered in the web browser to see the content served by the application?
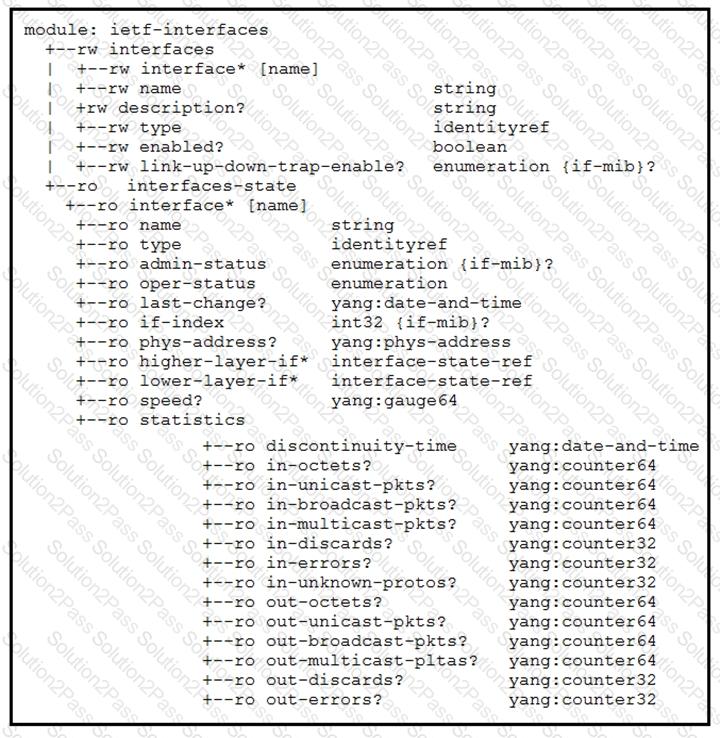
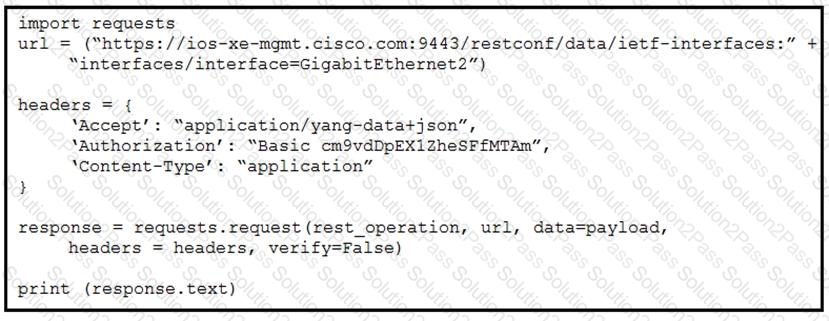
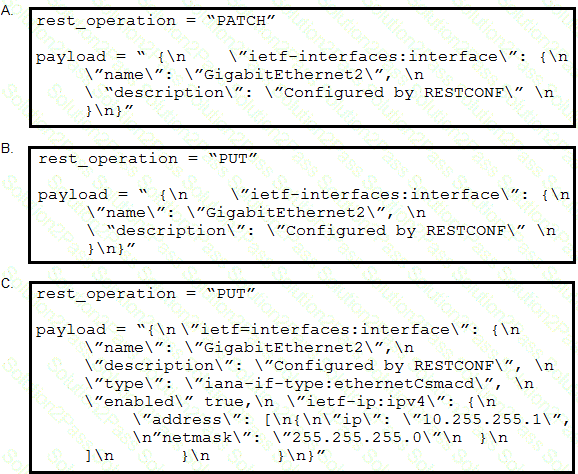
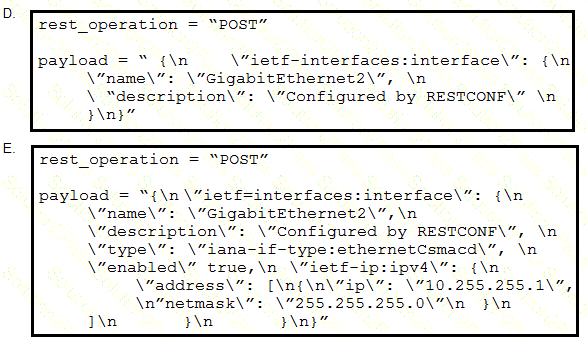
Refer to the exhibits. An interface named “GigabitEthernet2” has been configured on a Cisco IOS XE device. Using RESTCONF APIs as defined by the ietf-interfaces@2014-05-08.yang model, which two combinations of “rest_operation” and “payload” must be added to the Python script to set the “description” to “Configured by RESTCONF”? (Choose two.)
How is client code that consumes gRPC telemetry implemented, assuming that the preferred language is able to be chosen?
Refer to the exhibit.
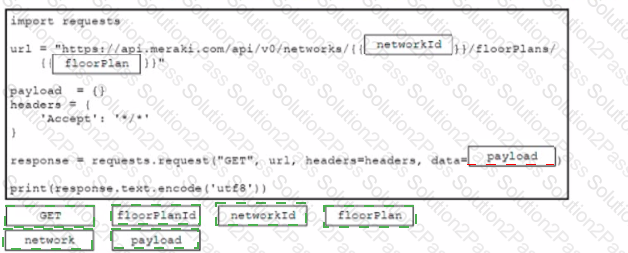
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that will retrieve location data Not all options are used.
Refer to the exhibit.
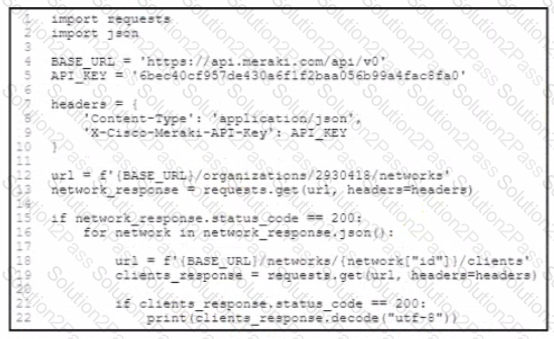
One part of an application routinely uses the Cisco Meraki API to collate data about all clients Other parts of the application also use the Meraki API, but a single API key is used within the application The organization has approximately 4.000 clients across 30 networks Some of the application users report poor performance and missing data. Which two changes improve the performance of the application? (Choose two.)
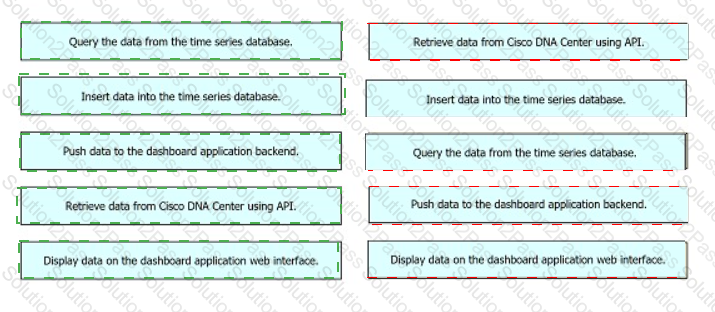
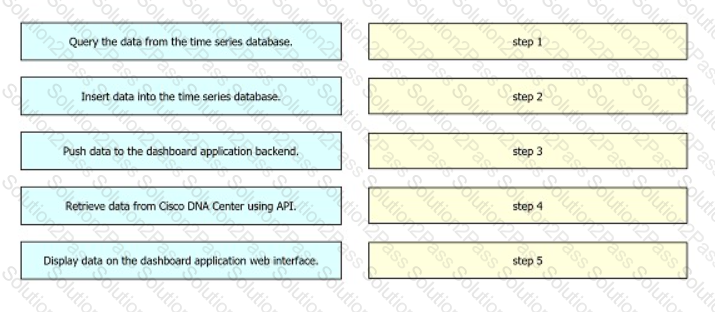
Drag and drop the operations from the left into the order on the right to create a web dashboard that displays Cisco DNA Center data for an organization.
{'lat': 37.4180951010362, 'lng': -122.098531723022, 'address': '', 'serial': 'Q2HP-F5K5-F98Q',
'mac': '88:15:44:ea:f5:bf', 'lanIp': '10.10.10.15',
'url': 'https://n149.meraki.com/DevNet-Sandbox/n/EFZDavc/manage/nodes/new_list/78214561218351',
'model': 'MS220-8P', 'switchProfileId': None, 'firmware': 'switch-11-31', 'floorPlanId': None}
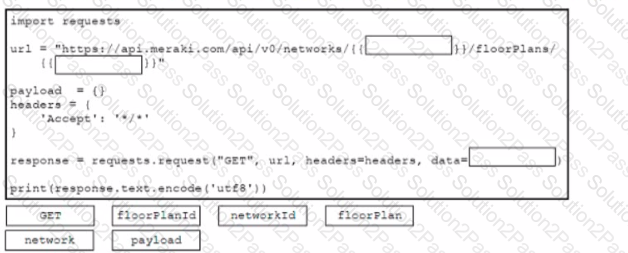
Refer to the exhibit. A developer needs to find the geographical coordinates of a device on the network L_397561557481105433 using a Python script to query the Meraki API. After running response = requests.get() against the Meraki API, the value of response.text is shown in the exhibit.
What Python code is needed to retrieve the longitude and latitude coordinates of the device?
What is the unique identifier in the 0Auth2 three-legged authorization code flow?
Refer to the exhibit.
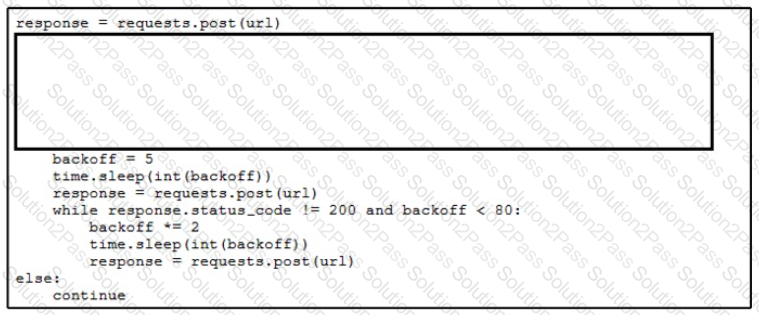
An engineer needs to implement REST API error handling when a timeout or rate limit scenario is present. Which code snippet must be placed into the blank in the code to complete the API request?
A)
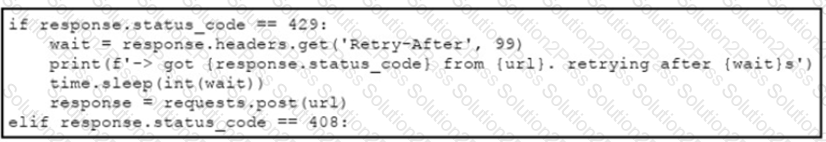
B)
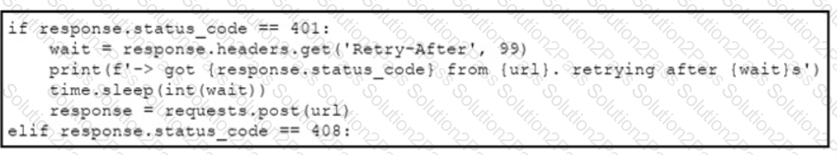
C)
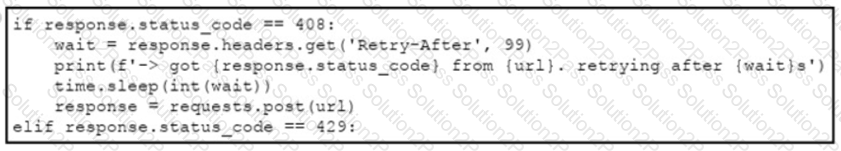
D)
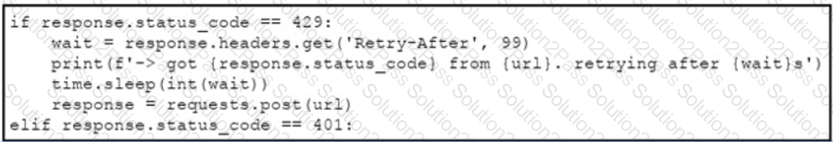
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?
Drag and drop the code from the bottom onto the box where the code is missing the snippet to complete this Ansible Playbook. Not all options are used.