350-901 Cisco Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 350-901 Developing Applications using Cisco Core Platforms and APIs (DEVCOR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
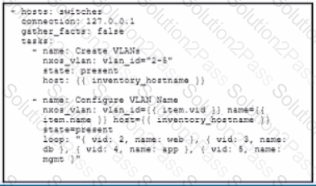
A developer must create VLANs 2-5 on a remote Cisco NX-OS switch by using an Ansible playbook The playbook must meet these requirements
• Configure the VLANs and a name for each VLAN
• Only run against the switches inventory group
• Execute from the local Ansible controller
• Prevent the collection of system information prior to execution
Which playbook must be used?
A)

B)

C)

D)
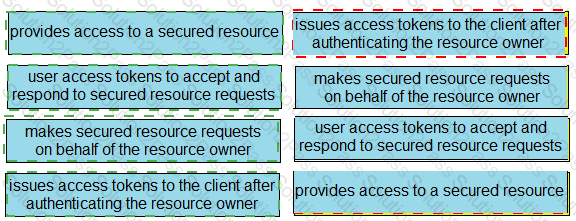
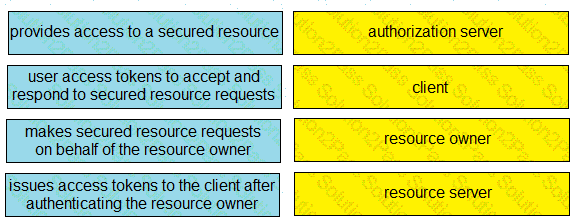
Drag and drop the descriptions from the left onto the related OAuth-defined roles on the right.
A developer must deploy a containerized application for network device inventory management. The developer sets up a Kubernetes cluster on two separate hypervisors The SLA is not currently meeting a specified maximum value for network latency/jitter. CPU/memory and disk 1,0 are functioning property.
Which two design approaches resolve the issue? (Choose two.)
Refer to the exhibit.
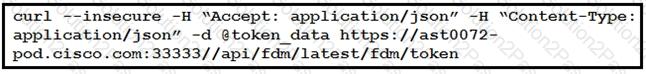
The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file “@token_data” that cURL is handling?
Which RFC5988 (Web Linking) relation type is used in the Link header to control pagination in APIs?
Refer to the exhibit.
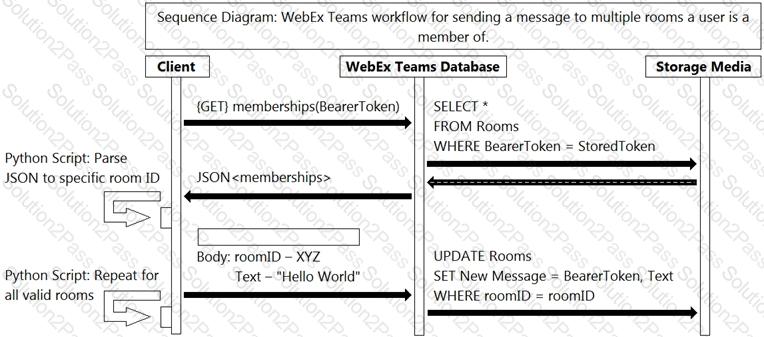
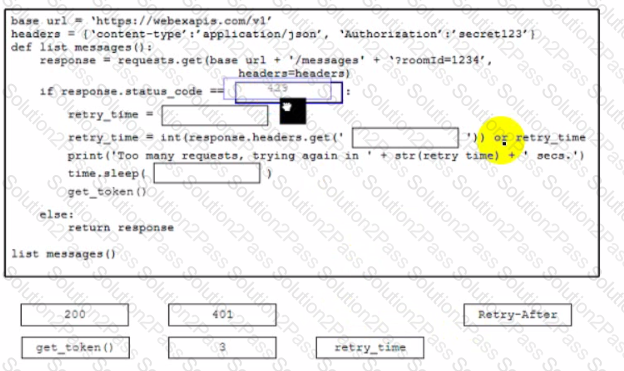
Which action will complete the workflow that represents how an API call sends multiple messages?
Refer to the exhibit.

An application is being developed as an information repository. The application will be used to store details about television shows, including the scenario, year, and category. Which database type must used for high performance for the data structure?
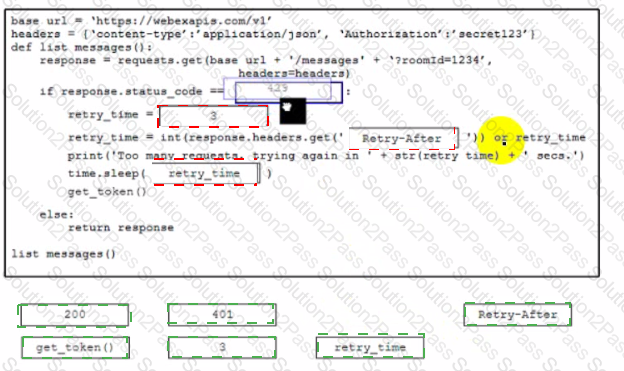
Drag and drop the code snippets from the bottom onto the boxes where the code is missing to complete the API call to implement error handling Not all options are used.
What is submitted when an SSL certificate is requested?
Which command is used 10 enable application hosting on a Cisco IOS XE device?
Where should distributed load balancing occur in a horizontally scalable architecture?
Refer to the exhibit.
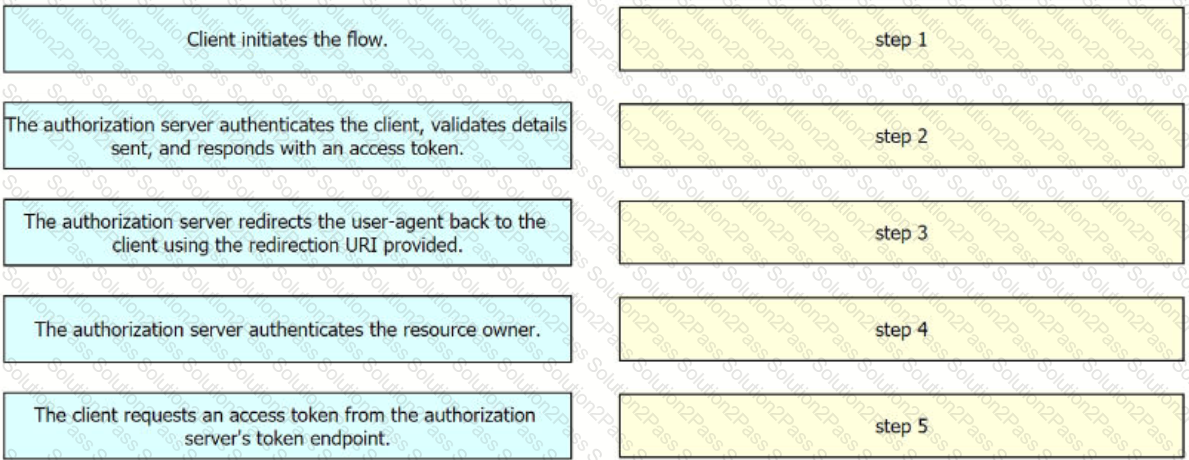
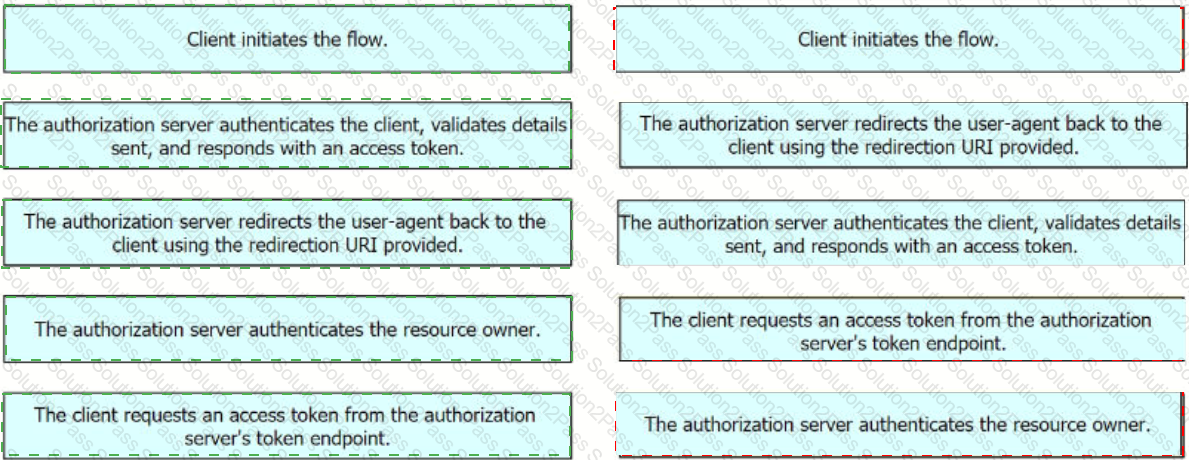
Drag and drop the steps from the left into the order of operation on the right for a successful OAuth2 three-legged authorization code grant flow,
Which function does Fluentd fulfill for application logging in Kubernetes?
Refer to the exhibit.
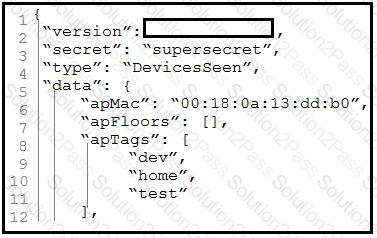
Which parameter is missing from the JSON response to confirm the API version that is
used?
Refer to the exhibit.
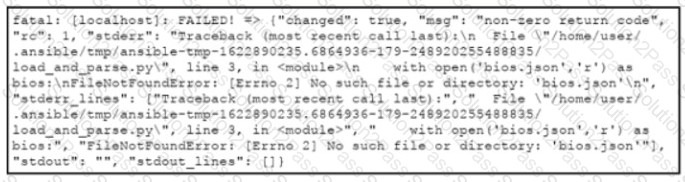
An engineer creates an application that leverages the Ansible framework to provision CPE endpoints that have configuration changes. The application contains an Ansible playbook named provision_cpes.yml that uses the ansible.builtin.script Ansible module to execute these two Python scripts:
•gather and_create.py. which creates a JSON file named bios.json that contains the CPE models and their respective IOS file information
•load and parse.py. which loads the file data and parses it for later consumption
After several successful runs, the application fails. During a review of the Ansible execution logs, the engineer discovers an error output that indicates that one of the stages failed. What is the cause of this issue?
Which configuration stop must be performed on a Cisco IOS XE device to present collected data in Cisco DNA Center?
What is a characteristic of event-driven architecture?
What are two building blocks of the 12-factor app? (Choose two.)
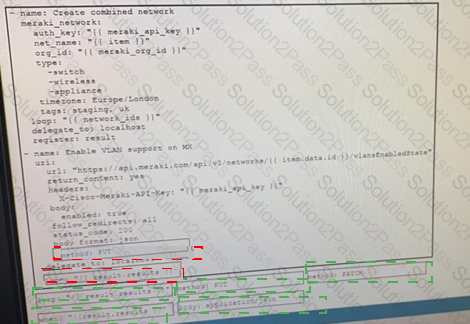
Drag and drop the code from the bottom onto the box where the code is missing on the Ansible task to enable a VLAN on a Meraki MX Device, Not all options are used.
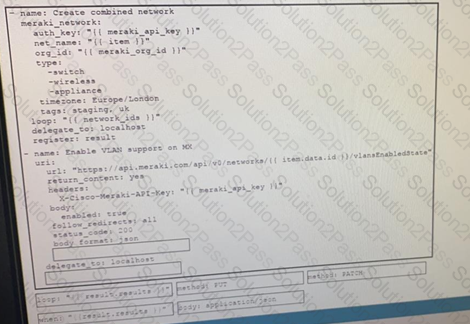
Refer to the exhibit.

A developer created a Python script to retrieve interface information for the devices in a MeraKi network environment. A security analyst has reviewed the code and observed poor secret storage practices. What is the appropriate password storage approach?