400-007 Cisco Certified Design Expert (CCDE v3.1) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 400-007 Cisco Certified Design Expert (CCDE v3.1) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which three items do you recommend for control plane hardening of an infrastructure device? (Choose three.)
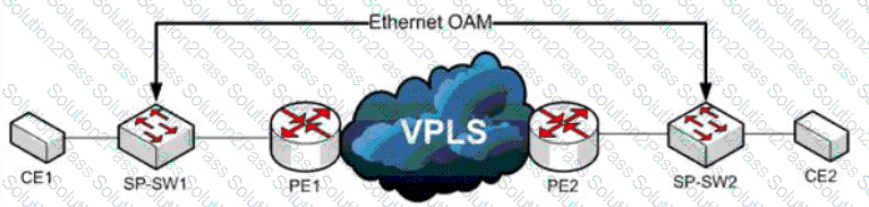
Refer to the exhibit. A service provider has a requirement to use Ethernet OAM to detect end-to-end connectivity failures between SP-SW1 and SP-SW2. Which two ways to design this solution are true? (Choose two)
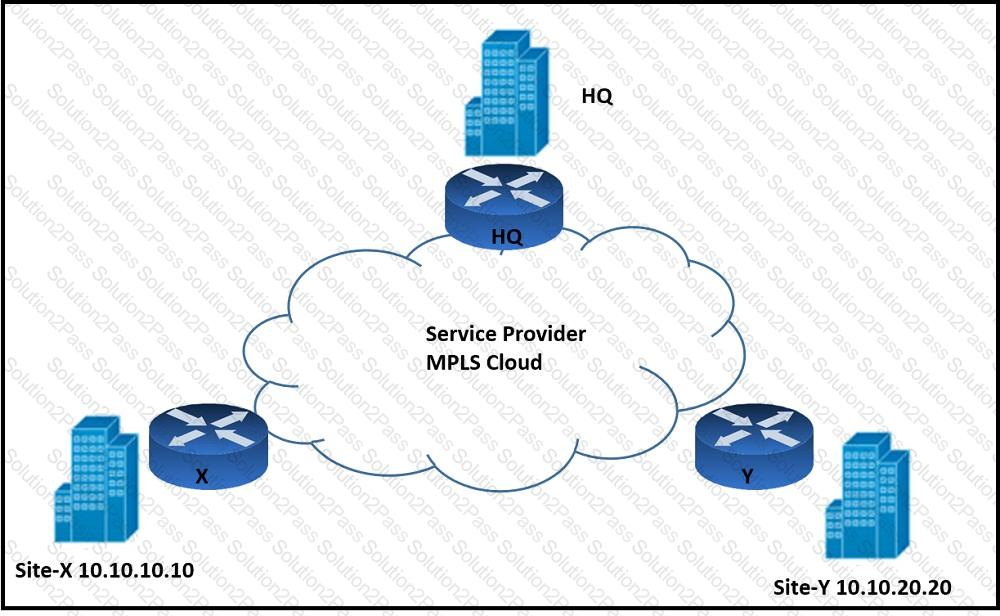
Refer to the exhibit. An architect must design an enterprise WAN that connects the headquarters with 22 branch offices. The number of remote sites is expected to triple in the next three years. The final solution must comply with these requirements:
Only the loopback address of each of the enterprise CE X and Y routers must be advertised to the interconnecting service provider cloud network.
The transport layer must carry the VPNv4 label and VPN payload over the MP-BGP control plane.
The transport layer must not be under service provider control.
Which enterprise WAN transport virtualization technique meets the requirements?
While reviewing an existing network design, you are discussing the characteristics of different STP versions. Which protocol minimizes unicast flooding during a Topology Change Notification in a Layer 2 switched network with many VLANs?
A company uses equipment from multiple vendors in a data center fabric to deliver SDN, enable maximum flexibility, and provide the best return on investment. Which YANG data model should be adopted for comprehensive features to simplify and streamline automation for the SDN fabric?
An external edge router provides connectivity from a service provider to an enterprise. Which two Internet edge best practices meet compliance regulations? (Choose two)
A healthcare customer requested that SNMP traps must be sent over the MPLS Layer 3 VPN service. Which protocol must be enabled?
Which two actions ensure voice quality in a branch location with a low-speed, high-latency WAN connection? (Choose two.)
Which extensions to GRE tunneling provide session tracking and in-order packet delivery in exchange for additional state stored in tunnel endpoints?
Refer to the table.
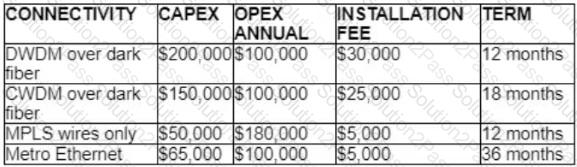
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The migration is estimated to take 20 months to complete but might extend an additional 10 months if issues arise. All connectivity options meet the requirements to migrate workloads. Which transport technology provides the best ROI based on cost and flexibility?
Refer to the exhibit.
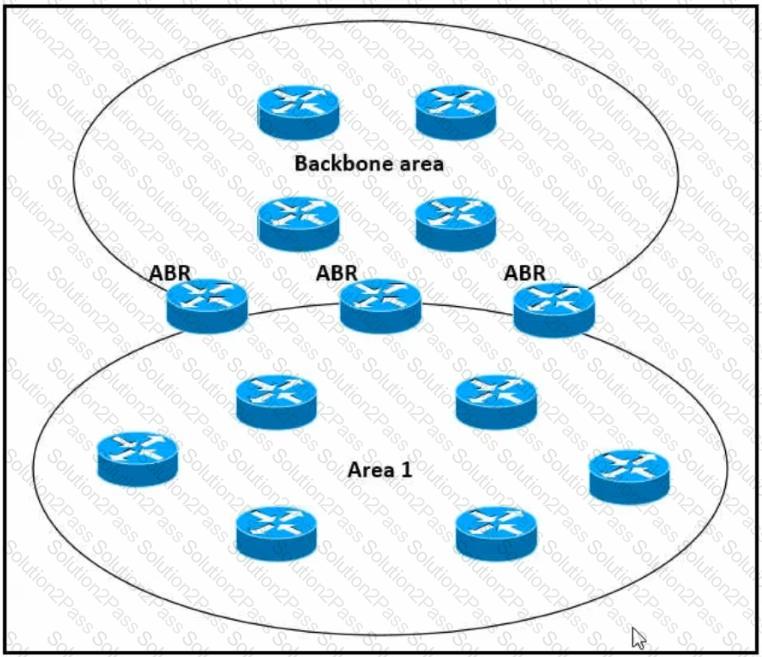
Which impact of using three or more ABRs between the backbone area and area 1 is true?
Company XYZ is running SNMPv1 in their network and understands that it has some flaws. They want to change the security design to implement SNMPv3 in the network. Which network threat is SNMPv3 effective against?
Which two foundational aspects of IoT are still evolving and being worked on by the industry at large? (Choose two)
Organizations that embrace Zero Trust initiatives ranging from business policies to technology infrastructure can reap business and security benefits. Which two domains should be covered under Zero Trust initiatives? (Choose two)
What is a description of a control plane action?
Which two benefits can software defined networks provide to businesses? (Choose two.)
What is the most important operational driver when building a resilient and secure modular network design?
A business customer deploys workloads in the public cloud but now faces governance issues related to IT traffic flow and data security. Which action helps identify the issue for further resolution?
Which mechanism provides Layer 2 fault isolation between data centers?
Company XYZ is designing the IS-IS deployment strategy for their multiarea IS-IS domain. They want IS-IS neighbor relationships minimized on each segment and the LSDB size optimized. Which design can be used?
