400-007 Cisco Certified Design Expert (CCDE v3.1) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 400-007 Cisco Certified Design Expert (CCDE v3.1) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which design consideration is valid when you contrast FabricPath and TRILL?
Company XYZ has a new network based on IPv6. Some of the subnets that they are planning to use will be confidential and need an addressing scheme that confines them to the local campus network. Which type of IPv6 addresses can be used for these networks in the IPv6 addressing design?
You are tasked to design a QoS policy for a service provider so they can include it in the design of their MPLS core network. If the design must support an MPLS network with six classes, and CEs will be managed by the service provider, which QoS policy should be recommended?
Over the years, many solutions have been developed to limit control plane state which reduces the scope or the speed of control plane information propagation. Which solution removes more specific information about a particular destination as topological distance is covered in the network?
An architect receives a business requirement from a CTO that states the RTO and RPO for a new system should be as close as possible to zero. Which replication method and data center technology should be used?
An existing wireless network was designed to support data traffic only. You must now install context-aware services for location tracking. What changes must be applied to the existing wireless network to increase the location accuracy? (Choose two)
An architect prepares a network design for a startup company. The design must meet business requirements while the business grows and divests due to rapidly changing markets. What is the highest priority in this design?
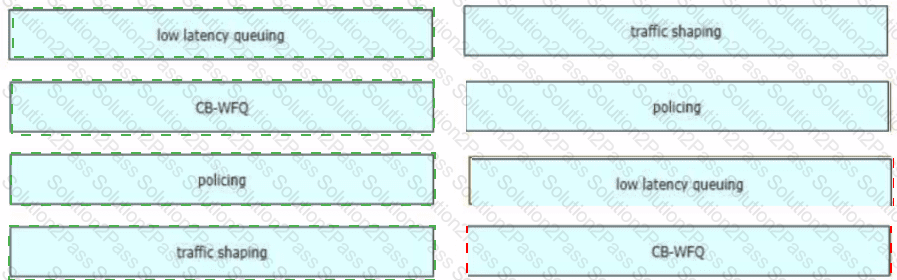
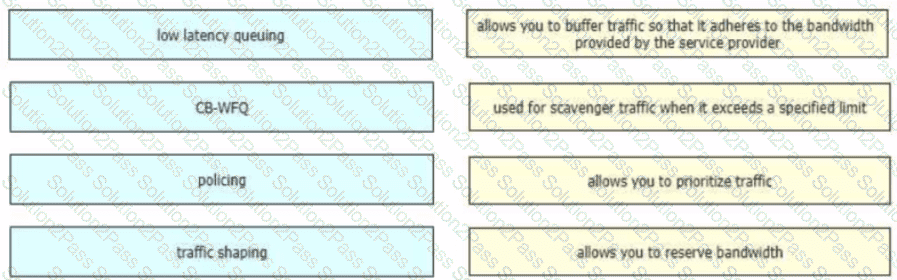
Drag and drop the QoS technologies from the left onto the correct capabilities on the right
Which parameter is the most important factor to consider when deciding service placement in a cloud solution?
Company XYZ is designing their network using the three-layer hierarchical model. At which layer must the QoS design classify or mark the traffic?
Company XYZ has 30 sites using MPLS L3 VPN and is concerned about data integrity. They want a centralized configuration model and minimal overhead. Which technology can be used?
Which statement about hot-potato routing architecture design is true?
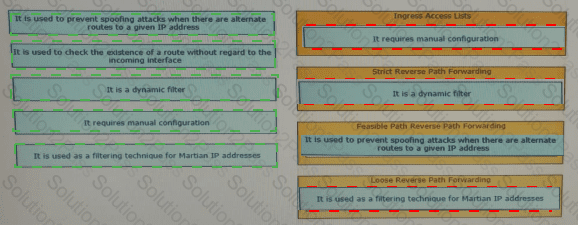
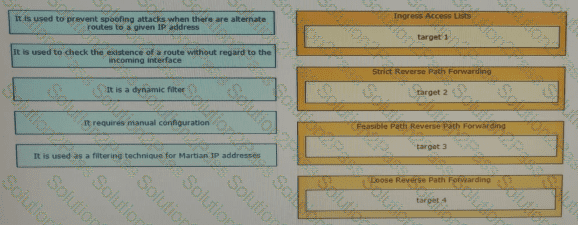
Drag and drop the design characteristics from the left onto the correct network filter techniques on the right. Not all options are used.
You were tasked to enhance the security of a network with these characteristics:
A pool of servers is accessed by numerous data centers and remote sites
The servers are accessed via a cluster of firewalls
The firewalls are configured properly and are not dropping traffic
The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology should you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
Which two actions must merchants do to be compliant with the Payment Card Industry Data Security Standard (PCI DSS)? (Choose two.)
A software-defined network exposes an API to the RIB and forwarding engine, allowing off-box control of routing—what SDN model is used?
During a pre-sales meeting with a potential customer, the customer CTO asks a question about advantages of controller-based networks versus a traditional network. What are two advantages to mention? (Choose two)
Company XYZ connects its sites over a private WAN. Their overlay network is running a DMVPN setup where the headquarters site is the hub. The company is planning on implementing multicast routing on the network. What should be used in the multicast routing design?
What are two key design principles when using a hierarchical core-distribution-access network model? (Choose two.)
Which optimal use of interface dampening on a fast convergence network design is true?