1Y0-440 Citrix Architecting a Citrix Networking Solution Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Citrix 1Y0-440 Architecting a Citrix Networking Solution certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two features are supported on LbaaSV1? (Choose two.)
Which encoding type can a Citrix Architect use to encode the StyleBook content, when importing the StyleBook configuration under source attribute?
Scenario: A Citrix Architect has set up NetScaler MPX devices in high availability mode with version 12.0.53.13 nc. These are placed behind a Cisco ASA 5505 Firewall. The Cisco ASA Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer’s security team:
The NetScaler MPX device:
should monitor the rate of traffic either on a specific virtual entity or on the device. It should be able to mitigate the attacks from a hostile client sending a flood of requests. The NetScaler device should be able to stop the HTTP, TCP, and DNS based requests.
needs to protect backend servers from overloading.
needs to queue all the incoming requests on the virtual server level instead of the service level.
should provide protection against well-known Windows exploits, virus-infected personal computers, centrally managed automated botnets, compromised webservers, known spammers/hackers, and phishing proxies.
should provide flexibility to enforce the decided level of security check inspections for the requests originating from a specific geolocation database.
should block the traffic based on a pre-determined header length, URL length, and cookie length. The device should ensure that characters such as a single straight quote (“); backslash (\); and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which security feature should the architect configure to meet these requirements?
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop environment which will include as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Active Citrix Virtual App and Citrix Virtual Desktop Service subscription
No existing Citrix deployment
Minimization of additional costs
All users should correct directly to the resource locations containing the servers which will host HDX sessions
Click the Exhibit button to view the conceptual environment architecture.
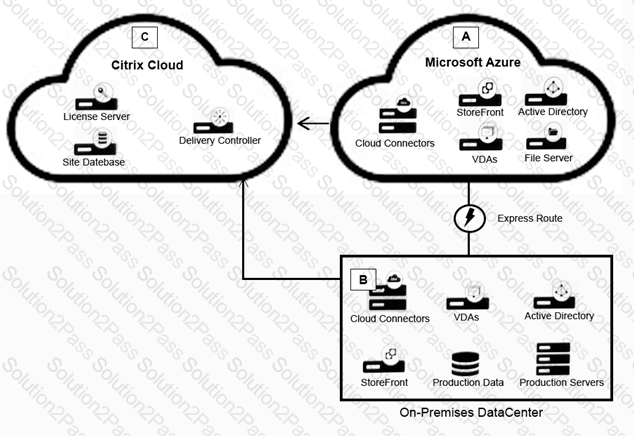
The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect needs to design a new Citrix ADC Gateway deployment to provide secure RDP access to backend Windows machines.
Click the Exhibit button to view additional requirements collected by the architect during the design discussions.
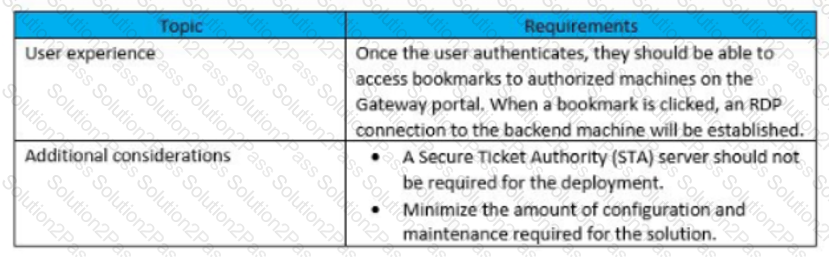
To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a _________ solution. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect holds a design discussion with a team of Workspacelab members, and they capture the following requirements for the Citrix ADC design project:
A pair of Citrlx ADC MPX appliances will be deployed in the DMZ network and another pair in the internal network.
High availability will be accessible between the pair of Citrix ADC MPX appliances in the DMZ network.
Multi-factor authentication must be configured for the Citrix Gateway virtual server.
The Citrix Gateway virtual server is integrated with the StoreFront server.
Load balancing must be configured for the StoreFront server. •Authentication must be deployed for users from the workspacelab.com domain.
The Workspacelab users should be authenticated using Cert Policy and LDAP.
All the client certificates must be SHA 256-signed, 2048 bits, and have UserPrincipalName as the subject.
Single Sign-on must be performed between StoreFront and Citrix Gateway. After deployment the architect observes that LDAP authentication is failing.
Click the Exhibit button to review the output of aaad.debug and the configuration of the authentication policy.
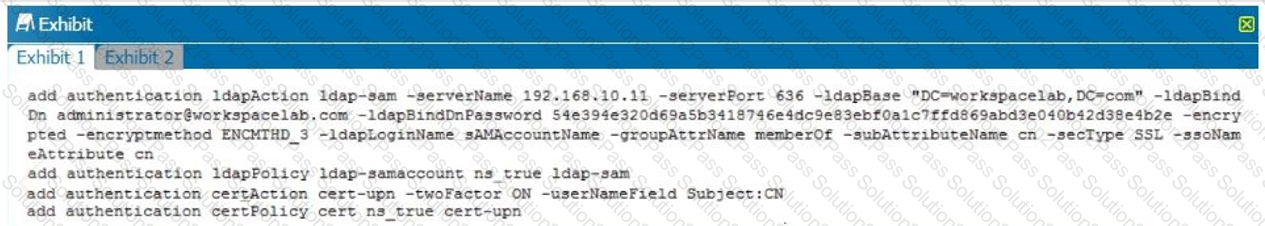
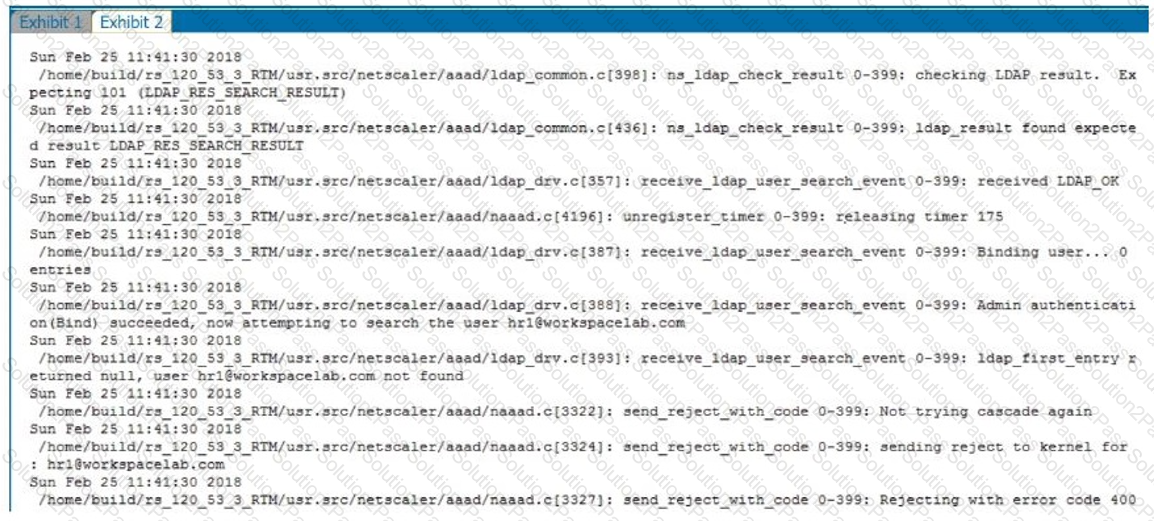
What is causing this issue?
Scenario: A Citrix Architect needs to assess an existing Citrix ADC configuration. The customer recently found that members of certain administrator groups were receiving permissions on the production Citrix ADC appliances that do NOT align with the designed security requirements. Click the Exhibit button to view the configured command policies for the production Citrix ADC deployment.
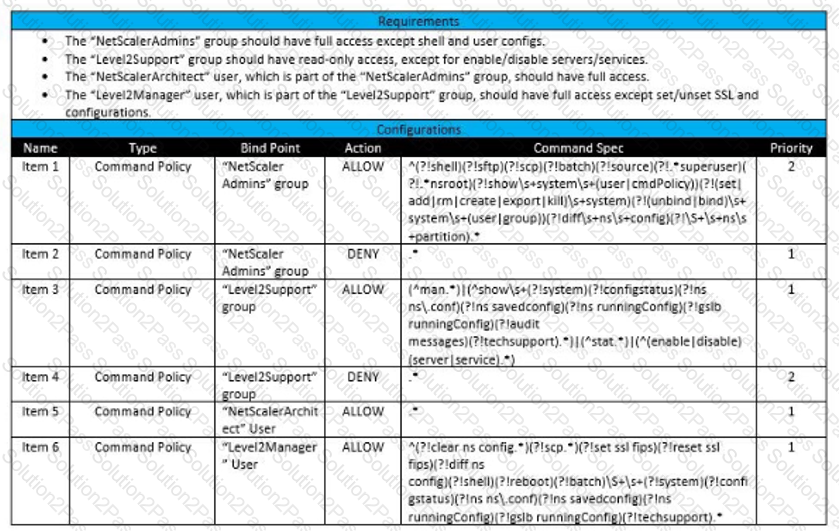
To align the command policy configuration with the security requirements of the organization, the__________for________________should change. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect has met with a team of Workspacelab members for a design discussion. They have captured the following requirements for the Citrix ADC design project:
Multi-factor authentication must be configured for the Citrix Gateway virtual server.
The Citrix Gateway virtual server is integrated with the Citrix Virtual Apps and Desktops environment.
Load balancing must be configured for the StoreFront server.
Authentication must be deployed for the users from the workspacelab.com and vendorlab.com domains.
The logon page must have the workspacelab logo on it.
Certificate verification must be performed to identify and extract the username.
The client certificate must have UserPrincipalName as a subject.
All the managed workstations for the workspacelab users must have the client identification certificate installed on them.
The workspacelab users connecting from the internal network should be authenticated using LDAP.
The workspacelab users connecting from the external network should be authenticated using LDAP and RADIUS.
The vendorlab users should be authenticated using Active Directory Federation Service.
The user credentials must NOT be shared between workspacelab and vendorlab.
Single Sign-on must be performed between StoreFront and Citrix Gateway.
A domain drop down list must be provided if the user connects to the Citrix Gateway virtual server externally.
The domain of the user connecting externally must be identified using the domain selected from the domain drop down list.
Which authentication policy must the architect execute first to meet the design requirements?
Which NetScaler Management and Analytics System (NMAS) utility can a Citrix Architect utilize to verify the configuration template created by the NMAS StyleBook, before actually executing it on the NetScaler?
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop environment which will include as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Active Citrix Virtual App and Citrix Virtual Desktop Service subscription
No existing Citrix deployment
Minimization of additional costs
All users should use same access point, regardless of network location
No multi-factor authentication is required
Click the Exhibit button to view the conceptual environment architecture.
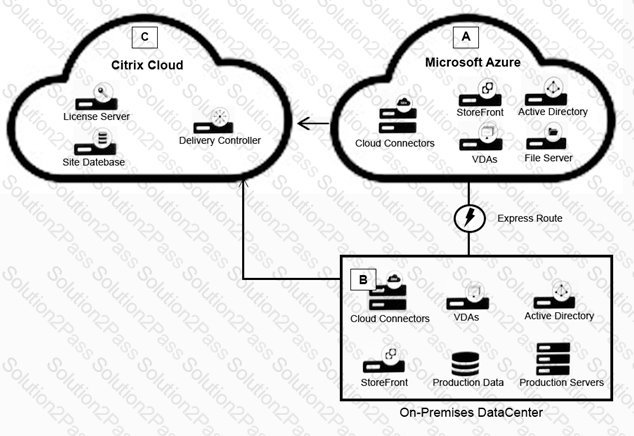
The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)
Which markup language can a Citrix use along with NITRO API to create a StyleBook?
Scenario: A Citrix Architect has setup Citrix ADC MPX devices in high availability mode with version 12.0.53.13 nc. These are placed behind a Cisco ASA 5505 firewall. The Cisco ASA firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall. The following requirements were captured by the architect during the discussion held as part of the Citrix ADC security implementation project with the customer's security team: The Citrix ADC MPX device:
should monitor the rate of traffic either on a specific virtual entity or on the device. It should be able to mitigate the attacks from a hostile client sending a flood of requests. The Citrix ADC device should be able to stop the HTTP. TOP, and DNS based requests.
needs to protect backend servers from overloading.
needs to queue all the incoming requests on the virtual server level instead of the service level.
should provide access to resources on the basis of priority.
should provide protection against well-known Windows exploits, virus-infected personal computers, centrally managed automated botnets. compromised webservers, known spammersThackers. and phishing proxies.
should provide flexibility to enforce the desired level of security check inspections for the requests originating from a specific geolocation database.
should block the traffic based on a predetermined header length, URL length, and cookie length.The device should ensure that characters such as a single straight quote (') backslash (); and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which security feature should the architect implement to meet these requirements?
What are three potential risks when examining the disaster recovery plan and implementation for a company? (Choose three)
Scenario: A Citrix Architect has configured two MPX devices in high availability mode with version 12.0.53.13 nc. After a discussion with the security teamf the architect enabled the Application Firewall feature for additional protection. In the initial deployment phase, the following security features were enabled:
• IP address reputation
• HTML SQL injection check
• Start URL
• HTML Cross-site scripting
• Form-Field consistency
After deployment in pre-production, the team identifies the following additional security features and changes as further requirements:
• Application Firewall should retain the response of form field in its memory. When a client submits the form in the next request Application Firewall should check for inconsistency in the request before sending it to the web server.
• All the requests dropped by Application Firewall should get a pre-configured HTML error page with appropriate information.
• The Application Firewall profile should be able to handle the data from an RSS feed and an ATOM-based site. Click the Exhibit button to view an excerpt of the existing configuration.
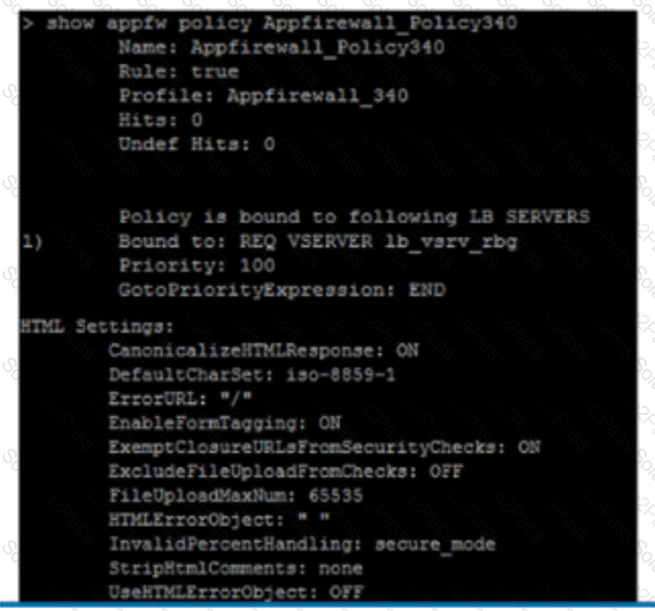
What should the architect do to meet these requirements?
_________ content type supports sending NITRO commands to NetScaler. (Choose the correct option to complete sentence.)
Scenario: A Citrix Architect needs to configure a Content Switching virtual server to provide access to www.workspacelab.com . However, the architect observes that whenever the user tries to access www.worksapcelab.com/CITRIX/WEB , the user receives a "503 - Service Unavailable" response. The configuration snippet is as follows:
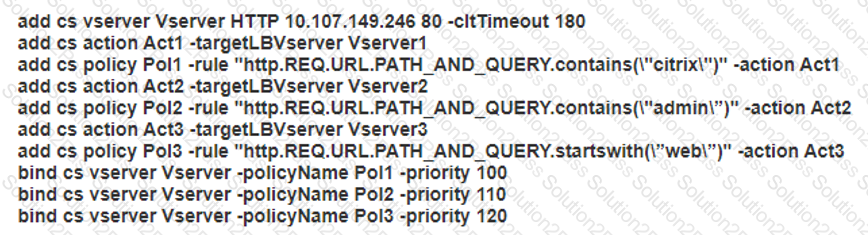
What should the architect modify to resolve this issue?
Under which two circumstances will a service be taken out of the slow start phase with automated slow start? (Choose Two)
A Citrix Architect needs to make sure that maximum concurrent AAA user sessions are limited to 4000 as a security restriction.
Which authentication setting can the architect utilize to view the current configuration?
Which three tasks can a Citrix Architect select and schedule using the Citrix ADC maintenance tasks? (Choose three.)
Scenario: A Citrix Architect needs to assess an existing NetScaler configuration. The customer recently found that certain user groups were receiving access to an internal web server with an authorization configuration that does NOT align with the designed security requirements.
Click the Exhibit button view the configured authorization settings for the web server.
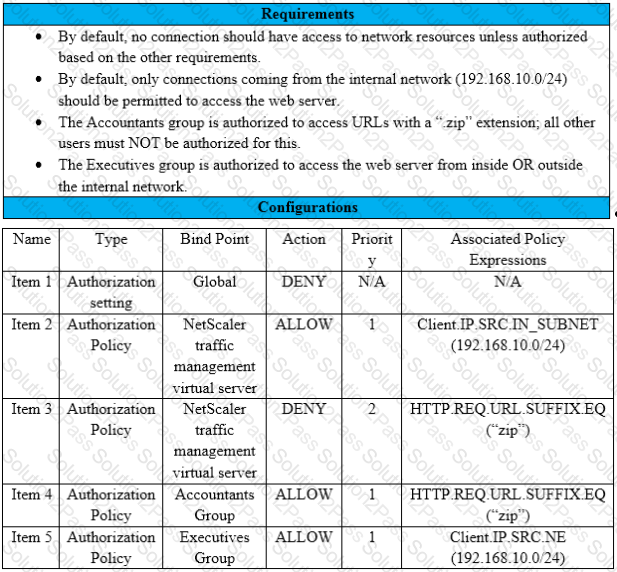
Which item should the architect change or remove to align the authorization configuration with the security requirements of the organization?
