1Y0-440 Citrix Architecting a Citrix Networking Solution Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Citrix 1Y0-440 Architecting a Citrix Networking Solution certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Scenario: A Citrix Architect and a team of Workspacelab members have met for a design discussion about the NetScaler Design Project. They captured the following requirements:
Two pairs of NetScaler MPX appliances will be deployed in the DMZ network and the internal network.
High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
The NetScaler Gateway virtual server is integrated with XenApp/XenDesktop environment.
Load balancing must be deployed for the users from the workspacelab.com and vendorlab.com domains.
The logon page must show the workspacelab logo.
Certificate verification must be performed to identify and extract the username.
The client certificate must have UserPrincipalName as a subject.
All the managed workstations for the workspace users must have a client identifications certificate installed on it.
The workspacelab users connecting from a managed workstation with a client certificate on it should be authenticated using LDAP.
The workspacelab users connecting from a workstation without a client certificate should be authenticated using LDAP and RADIUS.
The vendorlab users should be authenticated using Active Directory Federation Service.
The user credentials must NOT be shared between workspacelab and vendorlab.
Single Sign-on must be performed between StoreFront and NetScaler Gateway.
A domain drop down list must be provided if the user connects to the NetScaler Gateway virtual server externally.
The domain of the user connecting externally must be identified using the domain selected from the domain drop down list.
On performing the deployment, the architect observes that users are always prompted with two-factor authentication when trying to assess externally from an unmanaged workstation.
Click the exhibit button to view the configuration.
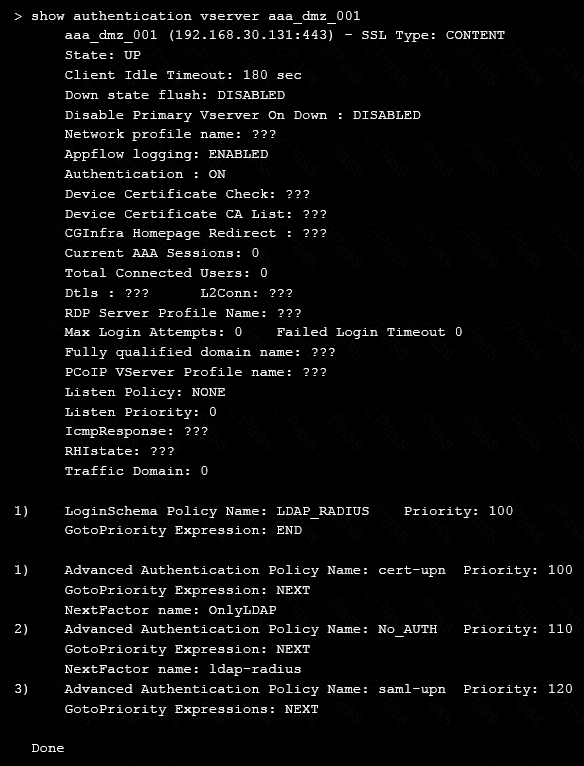
What should the architect do to correct this configuration?
Which two parameters are required to ensure that after authentication, the cookies can be transferred from browser to non-browser applications? (Choose two.)
Which four load-balancing methods support Citrix ADC Virtual Server-Level Slow Start? (Choose four.)
Scenario: A Citrix Architect needs to deploy a NetScaler appliance for Workspacelab, which will provide application load balancing services to Partnerlab and Vendorlab.
The setup requirements are as follows:
A pair of NetScaler MPX appliances will be deployed in the DMZ network.
High availability will be accessible on the NetScaler MPX in the DMZ Network.
Load balancing should be performed for the mail servers for Partnerlab and Vendorlab.
The traffic for both of the organizations must be isolated.
Separate Management accounts must be available for each client.
The load-balancing IP addresses must be identical.
A separate VLAN must be utilized for communication for each client.
Which solution can the architect utilize to meet the requirements?
What can help a Citrix Architect prepare to discuss time scales and resource requirements?
Scenario: A Citrix Architect needs to deploy three VPX instances on NetScaler SDX 11500 device to meet the following design requirements:
Three (3) VPX instances must be provisioned on the SDX device.
Instance 1 must be utilized for deploying NetScaler Gateway virtual server.
Instance 2 must be utilized for deploying load balancing virtual servers for XML, Director, StoreFront, and Active Directory servers.
Separate IP address must be utilized for the communication with XenApp environment and LDAP communication.
Instance 3 must be used for deploying the test environment.
In the test environment, NetScaler Gateway virtual server, load balancing virtual servers for XML, Director, StoreFront and Active Directory servers must be configured.
How many IP addresses will be required to meet these design requirements?
Which three parameters must a Citrix Architect designate when creating a new session policy? (Choose three.)
A Citrix Architect can execute a configuration job using a DeployMasterConfiguration template on a NetScaler_________deployed_________. (Choose the correct option to complete sentence.)
Scenario: A junior Citrix Architect would like to use nFactor to perform authentication based on the domain. The junior architect has reached out to a supervisor for assistance and has been provided with the following step-by-step configuration guide:
Create Authentication policy for LDAP. RADIUS.
Create logon schema for Domain drop down. LDAP. LDAP+RADIUS, and noschema.
Create Authentication policy label for OnlyLDAR LDAP+RADIUS, and RADIUS.
Bind DOMAIN drop down as default logon schema policy
Create Authentication profile to bind the AAA virtual server.
Bind Authentication profile to Traffic management virtual server or Citrix Gateway virtual server.
What must the junior architect bind In order for the authentication to work correctly?
Scenario: A Citrix Architect has implemented two high availability pairs of MPX 5500 and MPX 11500 devices respectively with 12.0.53.13 nc version. The Citrix ADC devices are set up to handle Citrix Gateway. Load Balancing. Application Firewall, and Content Switching. The Workspacelab infrastructure is set up to be monitored with Citrix Application Delivery Management version 12.0.53.13 nc by the Workspacelab administrators. The Workspacelab team wants to implement one more pair(s) of Citrix ADC MPX 7500 devices with version 12.0.53.13 nc.
The Citrix consulting team has assigned the task to implement these Citrix ADC devices in the infrastructure and set them up to be monitored and managed by Citrix ADC Management and Analytics {Citrix Application Delivery Management).
The following are the requirements that were discussed during the project initiation call:
Citrix Application Delivery Management should be configured to get the infrastructure information under sections such as HDX Insight, WEB Insight, and Security Insight.
Configuration on the new MPX devices should be identical to that of MPX 11500 devices.
Configuration changes after the deployment and initial setup should be optimized using Citrix Application Delivery Management.
Citrix Application Delivery Management should be utilized to configure templates that can be utilized by the Workspacelab team in future deployments.
As per the requirement from the Workspacelab team, Citrix Application Delivery Management should store the audited data for only 15 days.
However, the architect is NOT able to view any Information under Analytics. What should the architect do to fix this issue?
Which two options should a Citrix Architect evaluate during a capabilities assessment? (Choose two.)
Scenario: A Citrix Architect has configured NetScaler Gateway integration with a XenApp environment to provide access to users from two domains: vendorlab.com and workslab.com. The Authentication method used is LDAP.
Which two steps are required to achieve Single Sign-on StoreFront using a single store? (Choose two.)
Scenario: A Citrix Architect has deployed two MPX devices. 12.0.53.13 nc and MPX 11500 models, in a high availability (HA) pair for the Workspace labs team. The deployment method is two-arm and the devices are installed behind a CISCO ASA 5585 Firewall. The architect enabled the following features on the Citrix ADC devices. Content Switching. SSL Offloading, Load Balancing, Citrix Gateway. Application Firewall in hybrid security and Appflow. All are enabled to send monitoring information to Citrix Application Delivery Management 12.0.53.13 nc build. The architect is preparing to configure load balancing for Microsoft Exchange 2016 server.
The following requirements were discussed during the implementation:
All traffic needs to be segregated based on applications, and the fewest number of IP addresses should be utilized during the configuration.
All traffic should be secured and any traffic coming Into FITTP should be redirected to HTTPS.
Single Sign-on should be created for Microsoft Outlook web access (OWA).
Citrix ADC should recognize Uniform Resource Identifier (URI) and close the session to Citrix ADC when users hit the Logoff button In Microsoft Outlook web access.
Users should be able to authenticate using either user principal name (UPN) or sAMAccountName.
The Layer 7 monitor should be configured to monitor the Microsoft Outlook web access servers and the monitor probes must be sent on SSL.
Which monitor will meet these requirements?
Scenario: A Citrix Architect needs to assess a NetScaler Gateway deployment that was recently completed by a customer and is currently in pre-production testing. The NetScaler Gateway needs to use ICA proxy to provide access to a XenApp and XenDesktop environment. During the assessment, the customer informs the architect that users are NOT able to launch published resources using the Gateway virtual server.
Click the Exhibit button to view the troubleshooting details collected by the customer.
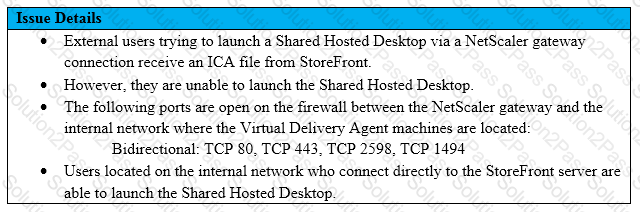
What is the cause of this issue?
For which two reasons should a Citrix Architect perform a capabilities assessment when designing and deploying a new Citrix ADC in an existing environment? (Choose two.)
A Citrix Architect needs to define the architect and operational processes required to implement and maintain the production environment.
In which phase of the Citrix Methodology will the architect define this?
Scenario: A Citrix Architect has set up Citrix ADC MPX devices in high availability mode with version 12.0.53.13 nc. These are placed behind a Cisco ASA 5505 firewall. The Cisco ASA firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall. The following requirements were captured by the architect during the discussion held as part of the Citrix ADC security implementation project with the customer's security team: The Citrix ADC MPX device:
• should monitor the rate of traffic either on a specific virtual entity or on the device. It should be able to mitigate the attacks from a hostile client sending a flood of requests. The Citrix ADC device should be able to stop the HTTP, TOP, and DNS based requests.
• needs to protect backend servers from overloading.
• needs to queue all the incoming requests on the virtual server level instead of the service level.
• should provide access to resources on the basis of priority.
• should provide protection against well-known Windows exploits, virus-infected personal computers, centrally managed automated botnets. compromised webservers, known spammersThackers. and phishing proxies.
• should provide flexibility to enforce the desired level of security check inspections for the requests originating from a specific geolocation database.
• should block the traffic based on a predetermined header length, URL length, and cookie length.The device should ensure that characters such as a single straight quote (') backslash (): and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which security feature should the architect implement to meet these requirements?
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.
Which setting is preventing the security requirements of the organization from being met?
Scenario: A Citrix Architect has implemented two high availability pairs of MPX 5500 and MPX 11500 devices respectively with 12.0.53.13 nc version. The NetScaler devices are set up to handle NetScaler Gateway, Load Balancing, Application Firewall, and Content Switching. The Workspacelab infrastructure is set up to be monitored with NMAS version 12.0.53.13 nc by the Workspacelab administrators. The Workspacelab team wants to implement one more pair of NetScaler MPX 7500 devices with version 12.0.53.13 nc.
The Citrix consulting team has assigned the task to implement these NetScaler devices in the infrastructure and set them up to be monitored and managed by NMAS.
The following are the requirements that were discussed during the project initiation call:
NMAS should be configured to get the infrastructure information under sections such as HDX Insight, WEB Insight, and Security Insight.
Configuration on the new MPX devices should be identical to MPX 11500 devices.
Configuration changes after the deployment and initial setup should be optimized using NMAS.
NMAS should be utilized to configure templates that can be utilized by the Workspacelab team in future deployment.
As per the requirement from the Workspacelab team, NMAS should be store the audited data for only 15 days.
Which process should the architect utilize to ensure that the deployment of MPX 11500 devices are optimized and that it is correct, before deploying the devices in production?
Which two settings must a Citrix Architect enable to deploy a shared VLAN on Citrix ADC VPX instance on an ESX platform? (Choose two.)
