CAS-004 CompTIA SecurityX Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CAS-004 CompTIA SecurityX Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A security compliance requirement states that specific environments that handle sensitive data must be protected by need-to-know restrictions and can only connect to authorized endpoints. The requirement also states that a DLP solution within the environment must be used to control the data from leaving the environment.
Which of the following should be implemented for privileged users so they can support the environment from their workstations while remaining compliant?
As part of its risk strategy, a company is considering buying insurance for cybersecurity incidents.
Which of the following BEST describes this kind of risk response?
city government's IT director was notified by the City council that the following cybersecurity requirements must be met to be awarded a large federal grant:
+ Logs for all critical devices must be retained for 365 days to enable monitoring and threat hunting.
+ All privileged user access must be tightly controlled and tracked to mitigate compromised accounts.
+ Ransomware threats and zero-day vulnerabilities must be quickly identified.
Which of the following technologies would BEST satisfy these requirements? (Select THREE).
A security architect is given the following requirements to secure a rapidly changing enterprise with an increasingly distributed and remote workforce
• Cloud-delivered services
• Full network security stack
• SaaS application security management
• Minimal latency for an optimal user experience
• Integration with the cloud 1AM platform
Which of the following is the BEST solution?
A company’s Chief Information Security Officer is concerned that the company’s proposed move to the cloud could lead to a lack of visibility into network traffic flow logs within the VPC.
Which of the following compensating controls would be BEST to implement in this situation?
Which of the following represents the MOST significant benefit of implementing a passwordless authentication solution?
An architectural firm is working with its security team to ensure that any draft images that are leaked to the public can be traced back to a specific external party. Which of the following would BEST accomplish this goal?
A security operations center analyst is investigating anomalous activity between a database server and an unknown external IP address and gathered the following data:
• dbadmin last logged in at 7:30 a.m. and logged out at 8:05 a.m.
• A persistent TCP/6667 connection to the external address was established at 7:55 a.m. The connection is still active.
• Other than bytes transferred to keep the connection alive, only a few kilobytes of data transfer every hour since the start of the connection.
• A sample outbound request payload from PCAP showed the ASCII content: "JOIN #community".
Which of the following is the MOST likely root cause?
A software development company is building a new mobile application for its social media platform. The company wants to gain its Users' rust by reducing the risk of on-path attacks between the mobile client and its servers and
by implementing stronger digital trust. To support users’ trust, the company has released the following internal guidelines:
* Mobile clients should verify the identity of all social media servers locally.
* Social media servers should improve TLS performance of their certificate status.
* Social media servers should inform the client to only use HTTPS.
Given the above requirements, which of the following should the company implement? (Select TWO).
A small business would like to provide guests who are using mobile devices encrypted WPA3 access without first distributing PSKs or other credentials. Which of the following features will enable the business to meet this objective?
Users are claiming that a web server is not accessible. A security engineer logs for the site. The engineer connects to the server and runs netstat -an and receives the following output:
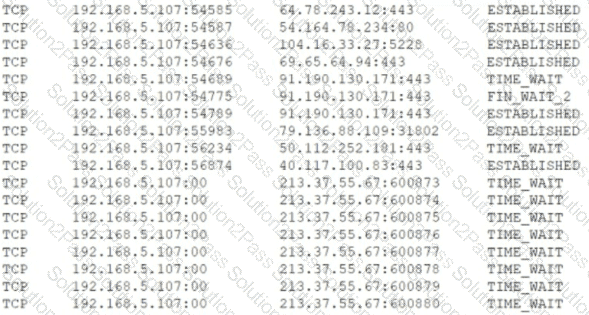 Which of the following is MOST likely happening to the server?
Which of the following is MOST likely happening to the server?
An organization decided to begin issuing corporate mobile device users microSD HSMs that must be installed in the mobile devices in order to access corporate resources remotely. Which of the following features of these devices MOST likely led to this decision? (Select TWO.)
Immediately following the report of a potential breach, a security engineer creates a forensic image of the server in question as part of the organization incident response procedure. Which of the must occur to ensure the integrity of the image?
As part of the customer registration process to access a new bank account, customers are required to upload a number of documents, including their passports and driver’s licenses. The process also requires customers to take a current photo of themselves to be compared against provided documentation.
Which of the following BEST describes this process?
An organization is prioritizing efforts to remediate or mitigate risks identified during the latest assessment. For one of the risks, a full remediation was not possible, but the organization was able to successfully apply mitigations to reduce the likelihood of impact.
Which of the following should the organization perform NEXT?
An organization developed a social media application that is used by customers in multiple remote geographic locations around the world. The organization’s headquarters and only datacenter are located in New York City. The Chief Information Security Officer wants to ensure the following requirements are met for the social media application:
Low latency for all mobile users to improve the users’ experience
SSL offloading to improve web server performance
Protection against DoS and DDoS attacks
High availability
Which of the following should the organization implement to BEST ensure all requirements are met?
A user experiences an HTTPS connection error when trying to access an Internet banking website from a corporate laptop. The user then opens a browser on a mobile phone and is able to access the same Internet banking website without issue. Which of the following security configurations is MOST likely the cause of the error?
A company is rewriting a vulnerable application and adding the inprotect () system call in multiple parts of the application's code that was being leveraged by a recent exploitation tool. Which of the following should be enabled to ensure the application can leverage the new system call against similar attacks in the future?
The security analyst discovers a new device on the company’s dedicated loT subnet during the most recent vulnerability scan. The scan results show numerous open ports and insecure protocols in addition to default usernames and passwords. A camera needs to transmit video to the security server in the loT subnet. Which of the following should the security analyst recommend to securely operate the camera?
A security engineer is assessing a new tool to segment data and communications between domains. The assessment must determine how data transmission controls can be bypassed without detection. Which of the following techniques should the security engineer use?
A company has data it would like to aggregate from its PLCs for data visualization and predictive maintenance purposes. Which of the following is the most likely destination for the tag data from the PLCs?
A company's finance department acquired a new payment system that exports data to an unencrypted file on the system. The company implemented controls on the file so only appropriate personnel are allowed access. Which of the following risk techniques did the department use in this situation?
A penetration tester inputs the following command:

This command will allow the penetration tester to establish a:
A customer requires secure communication of subscribed web services at all times, but the company currently signs its own certificate requests to an internal CA. Which of the following approaches will best meet the customer's requirements?
A company with customers in the United States and Europe wants to ensure its content is delivered to end users with low latency. Content includes both sensitive and public information. The company's data centers are located on the West Coast of the United States. Users on the East Coast of the United States and users in Europe are experiencing slow application response. Which of the following would allow the company to improve application response quickly?
A regulated company is in the process of refreshing its entire infrastructure. The company has a business-critical process running on an old 2008 Windows server. If this server fails, the company would lose millions of dollars in revenue. Which of the following actions should the company take?
An organization does not have visibility into when company-owned assets are off network or not connected via a VPN. The lack of visibility prevents the organization from meeting security and operational objectives. Which of the following cloud-hosted solutions should the organization implement to help mitigate the risk?
A security architect is improving a healthcare organization's security posture. Most of the software is cloud-based, but some old applications are still running on a server on-site. Medical devices using such applications require very low latency. The most important consideration isconfidentiality, followed byavailability, and thenintegrity. Which of the following is thefirst stepthe security architect should implement to protect PII?
A bank hired a security architect to improve its security measures against the latest threats The solution must meet the following requirements
• Recognize and block fake websites
• Decrypt and scan encrypted traffic on standard and non-standard ports
• Use multiple engines for detection and prevention
• Have central reporting
Which of the following is the BEST solution the security architect can propose?
During a recent breach, an attacker was able to get a user's login credentials by cracking a password that was retrieved via a stolen laptop. The attacker accessed the hashed passwords from the hard drive when it was connected to another device. Which of the following security measures could have helped prevent this account from being compromised?
