CAS-004 CompTIA SecurityX Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CAS-004 CompTIA SecurityX Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An organization has deployed a cloud-based application that provides virtual event services globally to clients. During a typical event, thousands of users access various entry pages within a short period of time. The entry pages include sponsor-related content that is relatively static and is pulled from a database. When the first major event occurs, users report poor response time onthe entry pages. Which of the following features is the most appropriate for the company to implement?
A security architect wants to ensure a remote host's identity and decides that pinning the X.509 certificate to the device is the most effective solution. Which of the following must happen first?
A security engineer investigates an incident and determines that a rogue device is on the network. Further investigation finds that an employee's personal device has been set up to access company resources and does not comply with standard security controls. Which of the following should the security engineer recommend to reduce the risk of future reoccurrence?
A security analyst is configuring an IPSec tunnel to use the strongest encryption currently available. Which of the following algorithms should be deployed to provide the most secure initial key exchange?
Signed applications reduce risks by:
A software developer must choose encryption algorithms to secure two parts of a mobile application. Given the following part descriptions and requirements:
•The first part of the application is used to transfer large files and must support file parts with transfer start/stop/resume. This part requires strong file encryption.
•The second part of the application uses a bit stream to continuously authenticate both ends of the connection. This part must implement confidentiality for the stream.
Which of the following encryption algorithms should the developer implement in the code to support both parts of the application? (Select two).
An organization is designing a MAC scheme (or critical servers running GNU/Linux. The security engineer is investigating SELinux but is confused about how to read labeling contexts. The engineer executes the command stat ./secretfile and receives the following output:

Which of the following describes the correct order of labels shown in the output above?
Which of the following technologies would need to be in an unmanaged state to perform forensic analysis on a laptop with an unknown encryption key?
An organization developed a containerized application. The organization wants to run the application in the cloud and automatically scale it based on demand. The security operations team would like to use container orchestration but does not want to assume patching responsibilities. Which of the following service models best meets these requirements?
An IT director is working on a solution to meet the challenge of remotely managing laptop devices and securely locking them down. The solution must meet the following requirements:
• Cut down on patch management.
• Make use of standard configurations.
• Allow for custom resource configurations.
• Provide access to the enterprise system from multiple types of devices.
Which of the following would meet these requirements?
A security engineer needs to select the architecture for a cloud database that will protect an organization's sensitive data. The engineer has a choice between a single-tenant or a multitenant database architecture offered by a cloud vendor. Which of the following best describes the security benefits of the single-tenant option? (Select two).
A security engineer is assessing a legacy server and needs to determine if FTP is running and on which port The service cannot be turned off, as it would impact a critical application's ability to function. Which of the following commands would provide the information necessary to create a firewall rule to prevent that service from being exploited?
A security engineer is implementing DLP. Which of the following should the security engineer include in the overall DLP strategy?
While performing mandatory monthly patch updates on a production application server, the security analyst reports an instance of buffer overflow for a new application that was migrated to the cloud and is also publicly exposed. Security policy requires that only internal users have access to the application. Which of the following should the analyst implement to mitigate the issues reported? (Select two).
The Chief Information Security Officer (CISO) at a software company is trying to document the technical and security requirements needed to connect the company’s network to an external system. The additional requirements include procedural and planning information. Which of the following should the CISO use to best accomplish this objective?
Which of the following security features do email signatures provide?
A security technician is trying to connect a remote site to the central office over a site-to-site VPN. The technician has verified the source and destination IP addresses are correct, but the technician is unable to get the remote site to connect. The following error message keeps repeating:
"An error has occurred during Phase 1 handshake. Deleting keys and retrying..."
Which of the following is most likely the reason the connection is failing?
A company uses a CSP to provide a front end for its new payment system offering. The new offering is currently certified as PCI compliant. In order for the integrated solution to be
compliant, the customer:
To bring digital evidence in a court of law the evidence must be:
A company hired a third-party consultant to run a cybersecurity incident simu-lation in order to identify security gaps and prepare stakeholders for a potential incident. Which of the following best describes this activity?
A SaaS startup is maturing its DevSecOps program and wants to identify weaknesses earlier in the development process in order to reduce the average time to identify serverless application vulnerabilities and the costs associated with remediation The startup began its early security testing efforts with DAST to cover public-facing application components and recently implemented a bug bounty program Which of the following will BEST accomplish the company's objectives?
A security engineer is reviewing Apache web server logs and has identified the following pattern in the log:
GET https://example.com/image5/../../etc/passwd HTTP/1.1 200 OK
The engineer has also reviewed IDS and firewall logs and established a correlation to an external IP address. Which of the following can be determined regarding the vulnerability and response?
A security architect is reviewing the following organizational specifications for a new application:
• Be sessionless and API-based
• Accept uploaded documents with Pll, so all storage must be ephemeral
• Be able to scale on-demand across multiple nodes
• Restrict all network access except for the TLS port
Which of the following ways should the architect recommend the application be deployed in order to meet security and organizational infrastructure requirements?
A security technician is investigating a system that tracks inventory via a batch update each night. The technician is concerned that the system poses a risk to the business, as errors are occasionally generated and reported inventory appears incorrect. The following output log is provided:
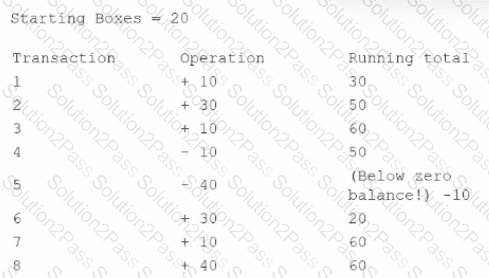
The technician reviews the output of the batch job and discovers that the inventory was never less than zero, and the final inventory was 100 rather than 60. Which of the following should the technician do to resolve this issue?
A company wants to prevent a partner company from denying agreement to a transaction. Which of the following is the best solution for the company?
In support of disaster recovery objectives, a third party agreed to provide 99.999% uptime. Recently, a hardware failure impacted a firewall without service degradation. Which of the following resiliency concepts was most likely in place?
After investigating a recent security incident, a SOC analyst is charged with creating a reference guide for the entire team to use. Which of the following should the analyst create to address future incidents?
An organization wants to implement an access control system based on its data classification policy that includes the following data types:
Confidential
Restricted
Internal
Public
The access control system should support SSO federation to map users into groups. Each group should only access systems that process and store data at the classification assigned to the group. Which of the following should the organization implement to enforce its requirements with minimal impact to systems and resources?
Which of the following describes how a risk assessment is performed when an organization has a critical vendor that provides multiple products?
An organization needs to classify its systems and data in accordance with external requirements. Which of the following roles is best qualified to perform this task?
