CAS-005 CompTIA SecurityX Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CAS-005 CompTIA SecurityX Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A security engineer is reviewing the following vulnerability scan report:
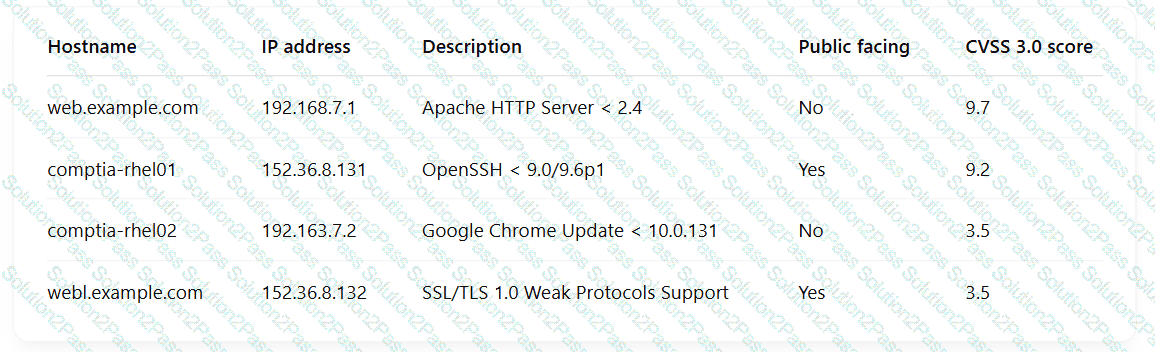
Which of the following should the engineer prioritize for remediation?
A healthcare system recently suffered from a ransomware incident. As a result, the board of directors decided to hire a security consultant to improve existing network security. The security consultant found that the healthcare network was completely flat, had no privileged access limits, and had open RDP access to servers with personal health information. As the consultant builds the remediation plan, which of the following solutions would best solve these challenges? (Select three).
A security professional is investigating a trend in vulnerability findings for newly deployed cloud systems Given the following output:
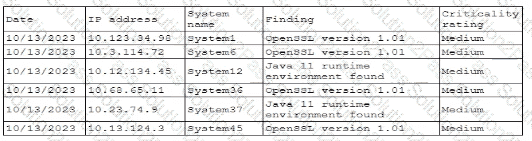
Which of the following actions would address the root cause of this issue?
A company that relies on an COL system must keep it operating until a new solution is available Which of the following is the most secure way to meet this goal?
A security team determines that the most significant risks within the pipeline are:
• Unauthorized code changes
• The current inability to perform independent verification of software modules
Which of the following best addresses these concerns?
A social media company wants to change encryption ciphers after identifying weaknesses in the implementation of the existing ciphers. The company needs the new ciphers to meet the following requirements:
• Utilize less RAM than competing ciphers.
• Be more CPU-efficient than previous ciphers.
• Require customers to use TLS 1.3 while broadcasting video or audio.
Which of the following is the best choice for the social media company?
A security analyst Detected unusual network traffic related to program updating processes The analyst collected artifacts from compromised user workstations. The discovered artifacts were binary files with the same name as existing, valid binaries but. with different hashes which of the following solutions would most likely prevent this situation from reoccurring?
A security manager at a local hospital wants to secure patient medical records. The manager needs to:
• Choose an access control model that clearly defines who has access to sensitive information.
• Prevent those who enter new patient information from specifying who has access to this data.
Which of the following access control models is the best way to ensure the lowest risk of granting unintentional access?
An organization wants to implement a secure cloud architecture across all instances. Given the following requirements:
· Establish a standard network template.
· Deployments must be consistent.
· Security policies must be able to be changed at scale.
Which of the following technologies meets these requirements?
Anorganization has noticed an increase in phishing campaigns utilizingtyposquatting. A security analyst needs to enrich the data for commonly used domains against the domains used in phishing campaigns. The analyst uses a log forwarder to forward network logs to the SIEM. Which of the following would allow the security analyst to perform this analysis?
A technician is reviewing the logs and notices a large number of files were transferred to remote sites over the course of three months. This activity then stopped. The files were transferred via TLS-protected HTTP sessions from systems that do not normally send traffic to those sites. The technician will define this threat as:
An organization recently experienced a security incident due to an exterior door in a busy area getting stuck open. The organization launches a security campaign focused on the motto, "See Something, Say Something." Which of the following best describes what the organization wants to educate employees about?
A company receives several complaints from customers regarding its website. An engineer implements a parser for the web server logs that generates the following output:
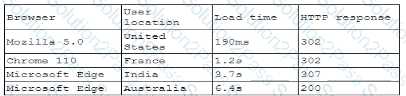
which of the following should the company implement to best resolve the issue?
An endpoint security engineer finds that a newly acquired company has a variety of non-standard applications running and no defined ownership for those applications. The engineer needs to find a solution thatrestricts malicious programs and software from running in that environment, while allowing the non-standard applications to function without interruption. Which of the following application control configurations should the engineer apply?
A security engineer wants to improve the security of an application as part of the development pipeline. The engineer reviews the following component of an internally developed web application that allows employees to manipulate documents from a number of internal servers:
response = requests.get(url)
Users can specify the document to be parsed by passing the document URL to the application as a parameter. Which of the following is the best solution?
After some employees were caught uploading data to online personal storage accounts, a company becomes concerned about data leaks related to sensitive, internal documentation. Which of the following would the company most likely do to decrease this type of risk?
An ISAC supplied recent threat intelligence information about pictures used on social media that provide reconnaissance of systems in use in secure facilities. In response, the Chief Information Security Officer (CISO) wants several configuration changes implemented via the MDM to ensure the following:
• Camera functions and location services are blocked for corporate mobile devices.
• All social media is blocked on the corporate and guest wireless networks.
Which of the following is the CISO practicing to safeguard against the threat?
A pharmaceutical lab hired a consultant to identify potential risks associated with Building 2, a new facility that is under construction. The consultant received the IT project plan, which includes the following VLAN design:
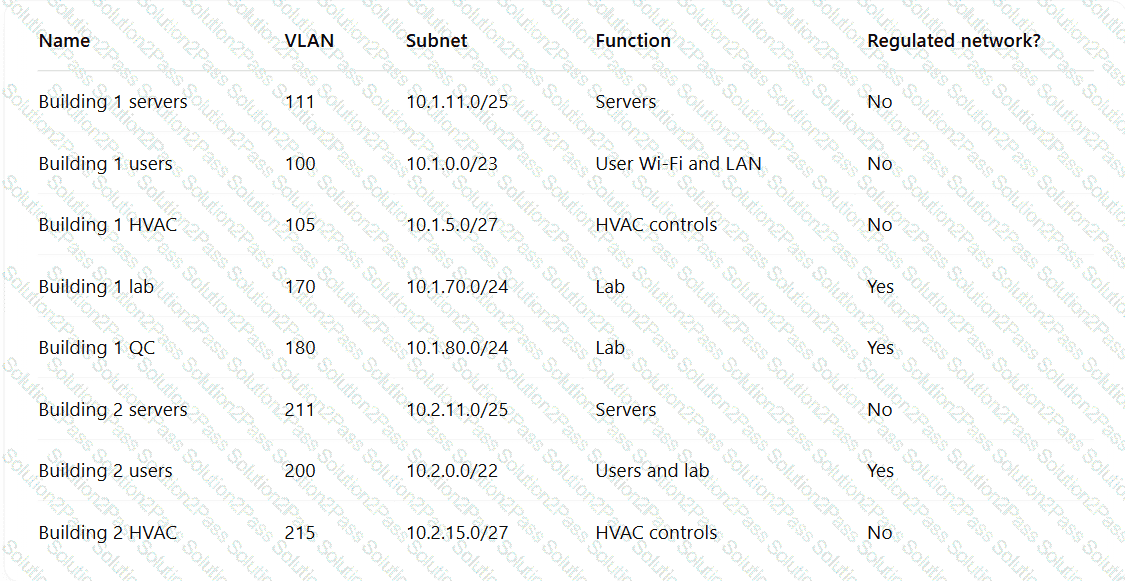
Which of the following TTPs should the consultant recommend be addressed first?
A company migrated a critical workload from its data center to the cloud. The workload uses a very large data set that requires computational-intensive data processing. The business unit that uses the workload is projecting the following growth pattern:
• Storage requirements will double every six months.
• Computational requirements will fluctuate throughout the year.
• Average computational requirements will double every year.
Which of the following should the company do to address the business unit's requirements?
A malware researcher has discovered a credential stealer is looking at a specific memory register to harvest passwords that will be used later for lateral movement in corporate networks. The malware is using TCP 4444 to communicate with other workstations. The lateral movement would be best mitigated by:
