CAS-005 CompTIA SecurityX Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CAS-005 CompTIA SecurityX Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.

An administrator needs to craft a single certificate-signing request for a web-server certificate. The server should be able to use the following identities to mutually authenticate other resources over TLS:
• wwwJnt.comptia.org
• webserver01.int.comptia.org
•10.5.100.10
Which of the following certificate fields must be set properly to support this objective?
A systems administrator wants to use existing resources to automate reporting from disparate security appliances that do not currently communicate. Which of the following is the best way to meet this objective?
A security officer performs due diligence activities before implementing a third-party solution into the enterprise environment. The security officer needs evidence from the third party that a data subject access request handling process is in place. Which of the following is the security officer most likely seeking to maintain compliance?
All organization is concerned about insider threats from employees who have individual access to encrypted material. Which of the following techniques best addresses this issue?
During a periodic internal audit, a company identifies a few new, critical security controls that are missing. The company has a mature risk management program in place, and the following requirements must be met:
The stakeholders should be able to see all the risks.
The risks need to have someone accountable for them.
Which of the following actions should the GRC analyst take next?
A security analyst isreviewing the following event timeline from an COR solution:
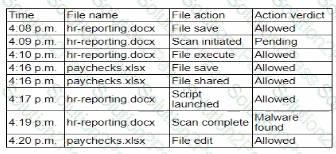
Which of the following most likely has occurred and needs to be fixed?
A systems administrator is working with clients to verify email-based services are performing properly. The administrator wants to have the email server digitally sign outbound emails using the organization's private key. Which of the following should the systems administrator configure?
Which of the following key management practices ensures that an encryption key is maintained within the organization?
Which of the following best describes the challengesassociated with widespread adoption of homomorphic encryption techniques?
A subcontractor develops safety critical avionics software for a major aircraft manufacturer. After an incident, a third-party investigator recommends the company begin to employ formal methods in the development life cycle. Which of the following findings from the investigation most directly supports the investigator's recommendation?
A company designs policies and procedures for hardening containers deployed in the production environment. However, a security assessment reveals that deployed containers are not complying with the security baseline. Which of the following solutions best addresses this issue throughout early life-cycle stages?
An organization currently has IDS, firewall, and DLP systems in place. The systems administrator needs to integrate the tools in the environment to reduce response time. Which of the following should the administrator use?
A security analyst discovered requests associated with IP addresses known for born legitimate 3nd bot-related traffic. Which ofthe following should the analyst use to determine whether the requests are malicious?
Company A and Company D ate merging Company A's compliance reports indicate branchprotections are not in place A security analyst needs to ensure that potential threats to the software development life cycle are addressed. Which of the following should me analyst cons
An audit finding reveals that a legacy platform has not retained loos for more than 30 days The platform has been segmented due to its interoperability with newer technology. As a temporarysolution, the IT department changed the log retention to 120 days. Which of the following should the security engineer do to ensure the logs are being properly retained?
Which of the following includes best practices for validating perimeter firewall configurations?
A global organization wants to manage all endpoint and user telemetry. The organization also needs to differentiate this data based on which office it is correlated to. Which of the following strategies best aligns with this goal?
A company sells a security appliance assembled from globally sourced hardware and software components. Installing the security appliance requires enabling administrative permissions for the service accounts on the appliance. Which of the following allows the company to reassure new and existing customers that the risk introduced by the appliance is minimal?
A security analyst is reviewing the following log:
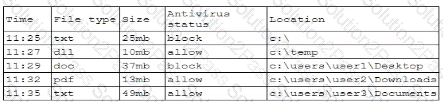
Which of the following possible events should the security analyst investigate further?
An organization has been using self-managed encryption keys rather than the free keys managed by the cloud provider. The Chief Information Security Officer (CISO) reviews the monthly bill and realizes the self-managed keys are more costly than anticipated. Which of the following should the CISO recommend to reduce costs while maintaining a strong security posture?
