CNX-001 CompTIA CloudNetX Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CNX-001 CompTIA CloudNetX Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A network architect must ensure only certain departments can access specific resources while on premises. Those same users cannot be allowed to access those resources once they have left campus. Which of the following would ensure access is provided according to these requirements?
Throughout the day, a sales team experiences videoconference performance issues when the accounting department runs reports. Which of the following is the best solution?
A security architect needs to increase the security controls around computer hardware installations. The requirements are:
Auditable access logs to computer rooms
Alerts for unauthorized access attempts
Remote visibility to the inside of computer rooms
Which of the following controls best meet these requirements? (Choose two.)
A network engineer is working on securing the environment in the screened subnet. Before penetration testing, the engineer would like to run a scan on the servers to identify the OS, application versions, and open ports. Which of the following commands should the engineer use to obtain the information?
A developer reports errors when trying to access a web application. The developer uses Postman to troubleshoot and receives the following error:
HTTP Status: 403 Forbidden
Headers include authentication-related variables such as access_key, signature, salt, and timestamp
The request is a GET request to a payment methods API
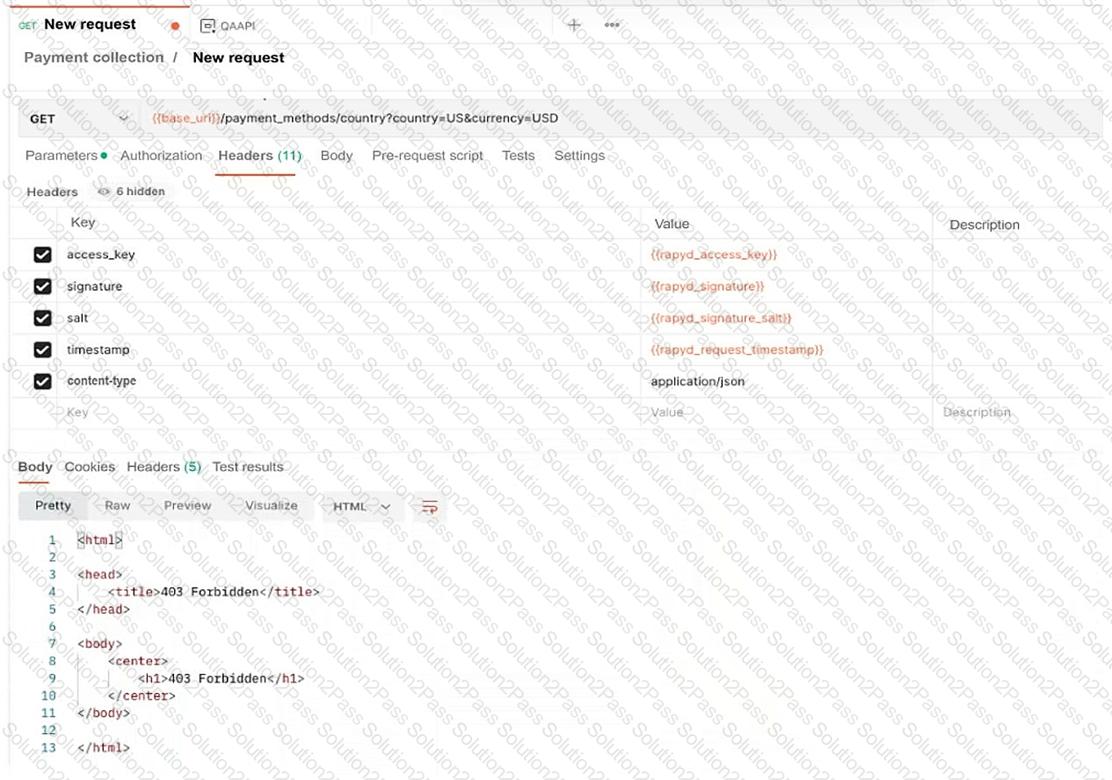
Which of the following is the cause of the issue?
A network administrator receives a ticket from one of the company's offices about video calls that work normally for one minute and then get very choppy. The network administrator pings the video server from that site to ensure that it is reachable:
(Ping output shows responses with varying latency times, including spikes: 11ms, 672ms, 849ms, 92ms, etc.)
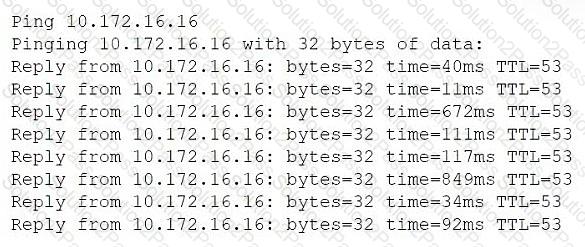
Which of the following is most likely the cause of the video call issue?
A network security engineer must secure a web application running on virtual machines in a public cloud. The virtual machines are behind an application load balancer. Which of the following technologies should the engineer use to secure the virtual machines? (Choose two.)
A network engineer needs to implement a cloud-native solution. The solution must allow the recording of network conversation metadata of the host and appliances attached to a VPC. Which of the following will accomplish these goals with the least effort?
A company is transitioning from on-premises to a hybrid environment. Due to regulatory standards, the company needs to achieve a high level of reliability and high availability for the connection between its data center and the cloud provider. Which of the following solutions best meets the requirements?
A network engineer at an e-commerce organization must improve the following dashboard due to a performance issue on the website:
(Refer to the image: Website performance monitoring dashboard showing metrics like network usage, CPU usage, memory usage, and disk usage over time.)
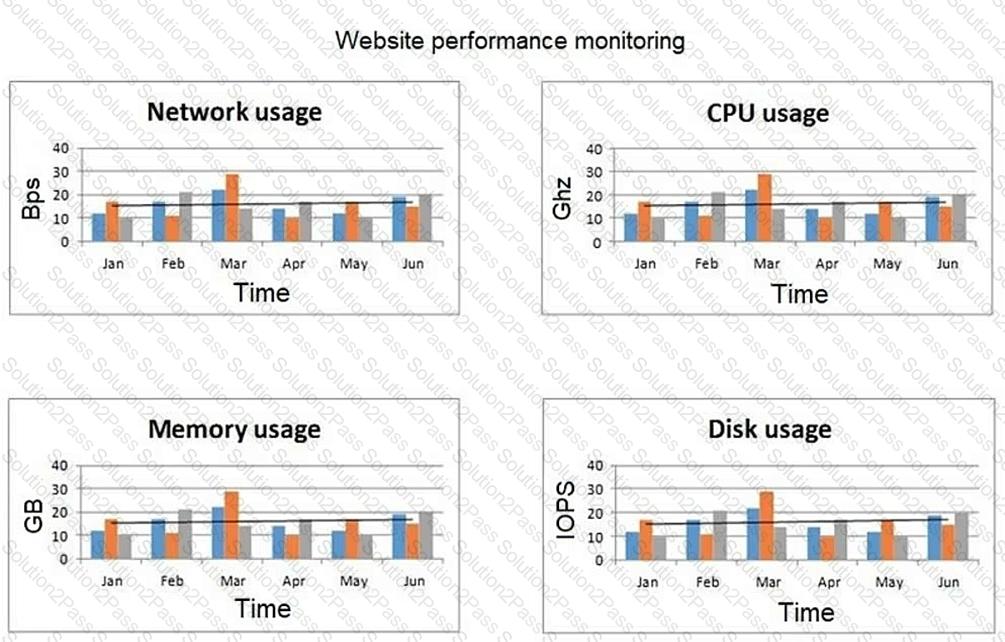
Which of the following is the most useful information to add to the dashboard for the operations team?
An administrator logged in to a cloud account on a shared machine but forgot to log out after the session ended. Which of the following types of security threats does this action pose?
A network administrator must connect a remote building at a manufacturing plant to the main building via a wireless connection. Which of the following should the administrator choose to get the greatest possible range from the wireless connection? (Choose two.)
A company deployed new applications in the cloud and configured a site-to-site VPN to connect the internal data center with the cloud. The IT team wants the internal servers to connect to those applications without using public IP addresses. Which of the following is the best solution?
A network architect is designing an expansion solution for the branch office network and requires the following business outcomes:
Maximize cost savings with reduced administration overhead
Easily expand connectivity to the cloud
Use cloud-based services to the branch offices
Which of the following should the architect do to best meet the requirements?
A partner is migrating a client from on-premises to a hybrid cloud. Given the following project status information, the initial project timeline estimates need to be revised:
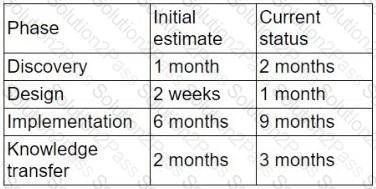
(Refer to image: Phases like Discovery, Design, Implementation, and Knowledge Transfer have all exceeded their initial estimated timelines.)
Which of the following documents needs to be revised to best reflect the current status of the project?
A network engineer is designing a Layer 2 deployment for a company that occupies severalfloors in an office building. The engineer decides to make each floor its own VLAN but still allow for communication between all user VLANs. The engineer also wants to reduce the time necessary for STP convergence to occur when new switches come online. Which of the following should the engineer enable to accomplish this goal?
A network administrator is configuring firewall rules to lock down the network from outside attacks. Which of the following should the administrator configure to create the most strict set of rules?
An application is hosted on a three-node cluster in which each server has identical compute and network performance specifications. A fourth node is scheduled to be added to the cluster with three times the performance as any one of the preexisting nodes. The network architect wants to ensure that the new node gets the same approximate number of requests as all of the others combined. Which of the following load-balancing methodologies should the network architect recommend?
A network engineer is setting up guest access on a Wi-Fi network. After a recent network analysis, the engineer discovered that a user could access the guest network and attack the corporate network, since the networks share the same VLAN. Which of the following should the engineer do to prevent an attack like this one from happening?
A cloud architect must recommend an architecture approach for a new medical application that requires the lowest downtime possible. Which of the following is the best application deployment strategy given the high-availability requirement?
