CS0-003 CompTIA CyberSecurity Analyst CySA+ Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CS0-003 CompTIA CyberSecurity Analyst CySA+ Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An analyst wants to ensure that users only leverage web-based software that has been pre-approved by the organization. Which of the following should be deployed?
A company was able to reduce triage time by focusing on historical trend analysis. The business partnered with the security team to achieve a 50% reduction in phishing attempts year over year. Which of the following action plans led to this reduced triage time?
A company is in the process of implementing a vulnerability management program, and there are concerns about granting the security team access to sensitive data. Which of the following scanning methods can be implemented to reduce the access to systems while providing the most accurate vulnerability scan results?
An analyst is reviewing a dashboard from the company's SIEM and finds that an IP address known to be malicious can be tracked to numerous high-priority events in the last two hours. The dashboard indicates that these events relate to TTPs. Which of the following is the analyst most likely using?
After an upgrade to a new EDR, a security analyst received reports that several endpoints were not communicating with the SaaS provider to receive critical threat signatures. To comply with the incident response playbook, the security analyst was required to validate connectivity to ensure communications. The security analyst ran a command that provided the following output:
ComputerName: comptia007
RemotePort: 443
InterfaceAlias: Ethernet 3
TcpTestSucceeded: False
Which of the following did the analyst use to ensure connectivity?
The Chief Information Security Officer wants the same level of security to be present whether a remote worker logs in at home or at a coffee shop. Which of the following should be recommended as a starting point?
A security analyst needs to prioritize vulnerabilities for patching. Given the following vulnerability and system information:
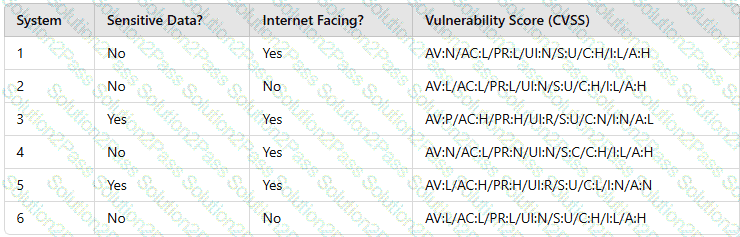
Which of the following systems should the analyst patch first?
A security analyst performs a vulnerability scan. Based on the metrics from the scan results, the analyst must prioritize which hosts to patch. The analyst runs the tool and receives the following output:
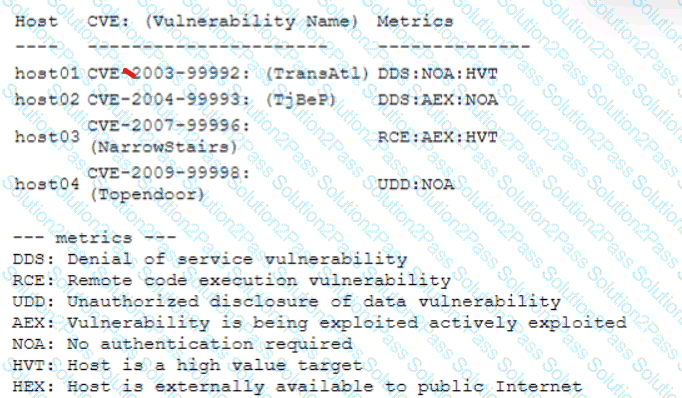
Which of the following hosts should be patched first, based on the metrics?
Which of the following are the most relevant factors related to vulnerability management reporting and communication within an organization?
A penetration tester is conducting a test on an organization's software development website. The penetration tester sends the following request to the web interface:
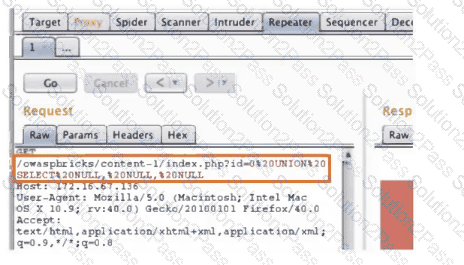
Which of the following exploits is most likely being attempted?
An MSSP received several alerts from customer 1, which caused a missed incident response deadline for customer 2. Which of the following best describes the document that was violated?
A DevOps analyst implements a webhook to trigger code vulnerability scanning for submissions to the repository. Which of the following is the primary benefit of this enhancement?
A vulnerability scan shows the following vulnerabilities in the environment:
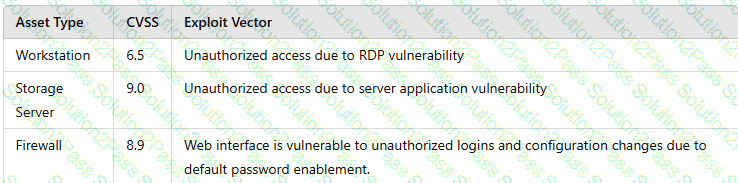
At the same time, the following security advisory was released:
"A zero-day vulnerability with a CVSS score of 10 may be affecting your web server. The vendor is working on a patch or workaround."
Which of the following actions should the security analyst take first?
During a scan of a web server in the perimeter network, a vulnerability was identified that could be exploited over port 3389. The web server is protected by a WAF. Which of the following best represents the change to overall risk associated with this vulnerability?
A cybersecurity analyst is recording the following details
* ID
* Name
* Description
* Classification of information
* Responsible party
In which of the following documents is the analyst recording this information?
After identifying a threat, a company has decided to implement a patch management program to remediate vulnerabilities. Which of the following risk management principles is the company exercising?
A security analyst discovers an ongoing ransomware attack while investigating a phishing email. The analyst downloads a copy of the file from the email and isolates the affected workstation from the network. Which of the following activities should the analyst perform next?
Each time a vulnerability assessment team shares the regular report with other teams, inconsistencies regarding versions and patches in the existing infrastructure are discovered. Which of the following is the best solution to decrease the inconsistencies?
%77%77%77%2e%69%63%65%2d%70%74%69%63%2e%63%6f%6d
Which of the following would most likely explain this behavior?
A web developer reports the following error that appeared on a development server when testing a new application:

Which of the following tools can be used to identify the application's point of failure?
