CS0-003 CompTIA CyberSecurity Analyst CySA+ Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CS0-003 CompTIA CyberSecurity Analyst CySA+ Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A security analyst needs to secure digital evidence related to an incident. The security analyst must ensure that the accuracy of the data cannot be repudiated. Which of the following should be implemented?
The most recent vulnerability scan results show the following
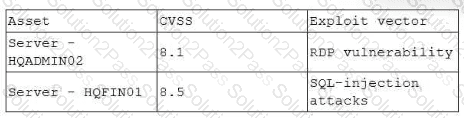
The vulnerability team learned the following from the asset owners:
• Server hqfinoi is a financial transaction database server used in the company's largest business unit.
• Server hqadmin02 is utilized by an end user with administrator privileges to several critical applications.
• No compensating controls exist for either issue.
Which of the following would the vulnerability team most likely do to determine remediation prioritization?
K company has recently experienced a security breach via a public-facing service. Analysis of the event on the server was traced back to the following piece of code:
SELECT ’ From userjdata WHERE Username = 0 and userid8 1 or 1=1;—
Which of the following controls would be best to implement?
An XSS vulnerability was reported on one of the public websites of a company. The security department confirmed the finding and needs to provide a recommendation to the application owner. Which of the following recommendations will best prevent this vulnerability from being exploited? (Select two).
During an extended holiday break, a company suffered a security incident. This information was properly relayed to appropriate personnel in a timely manner and the server was up to date and configured with appropriate auditing and logging. The Chief Information Security Officer wants to find out precisely what happened. Which of the following actions should the analyst take first?
A cybersecurity analyst has recovered a recently compromised server to its previous state. Which of the following should the analyst perform next?
A security analyst has identified outgoing network traffic leaving the enterprise at odd times. The traffic appears to pivot across network segments and target domain servers. The traffic is then routed to a geographic location to which the company has no association. Which of the following best describes this type of threat?
An organization is conducting a pilot deployment of an e-commerce application. The application's source code is not available. Which of the following strategies should an analyst recommend to evaluate the security of the software?
During a cybersecurity incident, one of the web servers at the perimeter network was affected by ransomware. Which of the following actions should be performed immediately?
A SOC analyst is analyzing traffic on a network and notices an unauthorized scan. Which of the following types of activities is being observed?
A security analyst is validating a particular finding that was reported in a web application vulnerability scan to make sure it is not a false positive. The security analyst uses the snippet below:

Which of the following vulnerability types is the security analyst validating?
A security manager has decided to form a special group of analysts who participate in both penetration testing and defending the company's network infrastructure during exercises. Which of the following teams should the group form in order to achieve this goal?
An organization is planning to adopt a zero-trust architecture. Which of the following is most aligned with this approach?
A SOC analyst determined that a significant number of the reported alarms could be closed after removing the duplicates. Which of the following could help the analyst reduce the number of alarms with the least effort?
A Chief Information Security Officer wants to lock down the users' ability to change applications that are installed on their Windows systems. Which of the following is the best enterprise-level solution?
During the log analysis phase, the following suspicious command is detected-
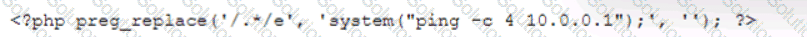
Which of the following is being attempted?
A company is in the process of implementing a vulnerability management program. no-lich of the following scanning methods should be implemented to minimize the risk of OT/ICS devices malfunctioning due to the vulnerability identification process?
A security analyst is performing vulnerability scans on the network. The analyst installs a scanner appliance, configures the subnets to scan, and begins the scan of the network. Which of the following
would be missing from a scan performed with this configuration?
A company's security team is updating a section of the reporting policy that pertains to inappropriate use of resources (e.g., an employee who installs cryptominers on workstations in the office). Besides the security team, which
of the following groups should the issue be escalated to first in order to comply with industry best practices?
An auditor is reviewing an evidence log associated with a cybercrime. The auditor notices that a gap exists between individuals who were responsible for holding onto and transferring the evidence between individuals responsible for the investigation. Which of the following best describes the evidence handling process that was not properly followed?
