FC0-U61 CompTIA IT Fundamentals+ Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA FC0-U61 CompTIA IT Fundamentals+ Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following scripting languages is most likely to be used in a Linux command-line environment?
A programmer is generating results by iterating rows that provide values needed for one calculation. Which of the following functions best accomplishes this task?
A remote user, who is working from home, requires significant bandwidth to connect to the corporate systems.
Which of the following types of Internet service connections would BEST meet the user’s needs?
Which of the following are benefits of a security awareness training program9 (Select two).
A customer is looking for a device that uses tap to pay when making purchases. Which of the following technologies should the customer use?
Which of the following storage types is MOST vulnerable to magnetic damage?
Given the following pseudocode:
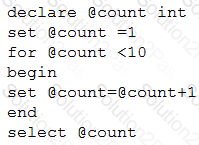
Which of the following is the output of the code?
Which of the following is best used to store many integers in one container?
Which of the following OS features would be best to use to remove unnecessary programs?
Which of the following best describes the differences between data and information?
Which of the following components is most likely to have a dedicated, active cooling method to prevent it from overheating during operation?
Which of the following is something that would likely need a copyright?
The IT department has established a new password policy for employees. Specifically, the policy reads:
Passwords must not contain common dictionary words
Passwords must contain at least one special character.
Passwords must be different from the las six passwords used.
Passwords must use at least one capital letter or number.
Which of the following practices are being employed? (Select TWO).
Which of the following interfaces is best for viewing database performance information?
Employee information is stored in a database. Which of the following BEST describes where all of an
employee’s information is stored?
A company has installed an application that only requires a workstation to function. Which of the following
architecture types is this application using?
Which of the following BEST describes a kilobyte?
Which of the following is a reason for using a UPS?
An engineer has been assigned the task of establishing network connectivity in a remote area where telephone lines are readily available but other infrastructure is limited. Which of the following technologies would be the best solution?
Ann, the president of a company, has requested assistance with choosing the appropriate Internet connectivity for her home. The home is in a remote location and has no connectivity to existing infrastructure. Which of the following Internet service types should MOST likely be used?
