PT0-002 CompTIA PenTest+ Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA PT0-002 CompTIA PenTest+ Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A penetration tester fuzzes an internal server looking for hidden services and applications and obtains the following output:
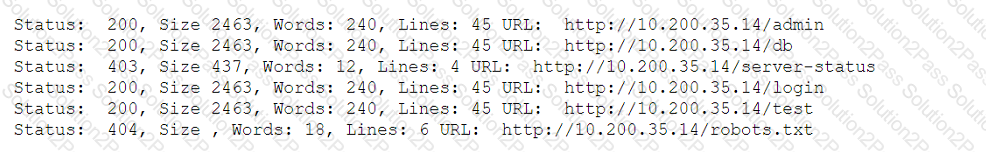
Which of the following is the most likely explanation for the output?
A penetration tester approaches a company employee in the smoking area and starts a conversation about the company's recent social event. After a few minutes, the employee holds the badge-protected door open for the penetration tester and both enter the company's building. Which of the following attacks did the penetration tester perform?
Which of the following components should a penetration tester most likely include in a report at the end of an assessment?
A vulnerability assessor is looking to establish a baseline of all IPv4 network traffic on the local VLAN without a local IP address. Which of the following Nmap command sequences would best provide this information?
Which of the following would be the most efficient way to write a Python script that interacts with a web application?
Which of the following is the most important aspect to consider when calculating the price of a penetration test service for a client?
Which of the following legal concepts specifically outlines the scope, deliverables, and timelines of a project or engagement?
A penetration tester is enumerating shares and receives the following output:
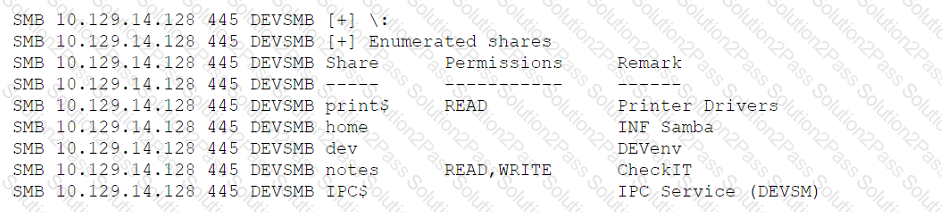
Which of the following should the penetration tester enumerate next?
A penetration tester wants to find the password for any account in the domain without locking any of the accounts. Which of the following commands should the tester use?
Within a Python script, a line that states print (var) outputs the following:
[{'1' : 'CentOS', '2' : 'Ubuntu'), {'1' : 'Windows 10', '2' : 'Windows Server 2016'}]
Which of the following objects or data structures is var ?
A client asks a penetration tester to retest its network a week after the scheduled maintenance window. Which of the following is the client attempting to do?
During an assessment, a penetration tester emailed the following Python script to CompTIA's employees:
import pyHook, sys, logging, pythoncom, datetime
log_file='C:\\Windows\\Temp\\log_comptia.txt' def KbrdEvent(event):
logging.basicConfig(filename=log_file,level=logging.DEBUG, format='%(messages)s') chr(event.Ascii)
logging.log(10, chr(event.Ascii))
return True
hooks_manager = pyHook.HookManager()
hooks_manager.KeyDown = KbrdEvent
hooks_manager.HookKeyboard()
pythoncom.PumpMessages()
Which of the following is the intended effect of this script?
During a code review assessment, a penetration tester finds the following vulnerable code inside one of the web application files:
<% String id = request.getParameter("id"); %>
Employee ID: <%= id %>
Which of the following is the best remediation to prevent a vulnerability from being exploited, based on this code?
Which of the following tools can a penetration tester use to brute force a user password over SSH using multiple threads?
A penetration tester is conducting an on-path link layer attack in order to take control of a key fob that controls an electric vehicle. Which of the following wireless attacks would allow a penetration tester to achieve a successful attack?
After obtaining a reverse shell connection, a penetration tester runs the following command: www-data@server!2:sudo -1
User www-data may run the following commands on serverl2: (root) NOPASSWD: /usr/bin/vi
Which of the following is the fastest way to escalate privileges on this server?
An organization's Chief Information Security Officer debates the validity of a critical finding from a penetration assessment that was completed six months ago. Which of the following post-report delivery activities would have most likely prevented this scenario?
After compromising a remote host, a penetration tester is able to obtain a web shell. A firewall is blocking outbound traffic. Which of the following commands would allow the penetration tester to obtain an interactive shell on the remote host?
