PT0-002 CompTIA PenTest+ Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA PT0-002 CompTIA PenTest+ Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following tools would be best to use to conceal data in various kinds of image files?
During a vulnerability scanning phase, a penetration tester wants to execute an Nmap scan using custom NSE scripts stored in the following folder:
/home/user/scripts
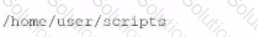
Which of the following commands should the penetration tester use to perform this scan?
A penetration tester is doing an assessment for a company that requires an external command-and-control server. The command-and-control tool should be able to use multiple types of payloads (PowerShell. SMB. and binaries) and centralize the management of compromised systems. Which of the following tools should the tester use?
As part of active reconnaissance, penetration testers need to determine whether a protection mechanism is in place to safeguard the target’s website against web application attacks. Which of the following methods would be the most suitable?
As part of an active reconnaissance, a penetration tester intercepts and analyzes network traffic, including API requests and responses. Which of the following can be gained by capturing and examining the API traffic?
A penetration tester managed to exploit a vulnerability using the following payload:
IF (1=1) WAIT FOR DELAY '0:0:15'
Which of the following actions would best mitigate this type ol attack?
A penetration tester is hired to test a client’s systems. The client's systems are hosted by the client at its headquarters. The production environment is hosted by a private cloud-hosting company. Which of the following would be the most important for the penetration tester to determine before beginning the test?
A penetration tester would like to crack a hash using a list of hashes and a predefined set of rules. The tester runs the following command: hashcat.exe -a 0 .\hash.txt .\rockyou.txt -r .\rules\replace.rule
Which of the following is the penetration tester using to crack the hash?
A penetration tester is attempting to perform reconnaissance on a customer's external-facing footprint and reviews a summary of the fingerprinting scans:
SSH servers: 23
NTP servers: 4
Rsync servers: 5
LDAP servers: 2
Which of the following OSs is the organization most likely using?
Which of the following documents should be consulted if a client has an issue accepting a penetration test report that was provided?
A penetration tester is conducting an assessment on 192.168.1.112. Given the following output:
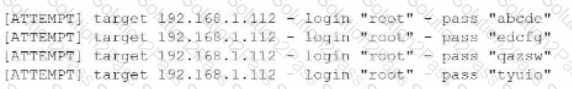
Which of the following is the penetration tester conducting?
A security engineer is trying to bypass a network IPS that isolates the source when the scan exceeds 100 packets per minute. The scope of the scan is to identify web servers in the 10.0.0.0/16 subnet.
Which of the following commands should the engineer use to achieve the objective in the least amount of time?
Which of the following tools would be the best to use to intercept an HTTP response at an API, change its content, and forward it back to the origin mobile device?
During a security assessment, a penetration tester decides to implement a simple TCP port scanner to check the open ports from 1000 to 2000. Which of the following Python scripts would achieve this task?
During an assessment of a web application, a penetration tester would like to test the application for blind SQL injection. Which of the following techniques should the penetration tester perform next?
A penetration tester is performing an assessment for an organization and must gather valid user credentials. Which of the following attacks would be best for the tester to use to achieve this objective?
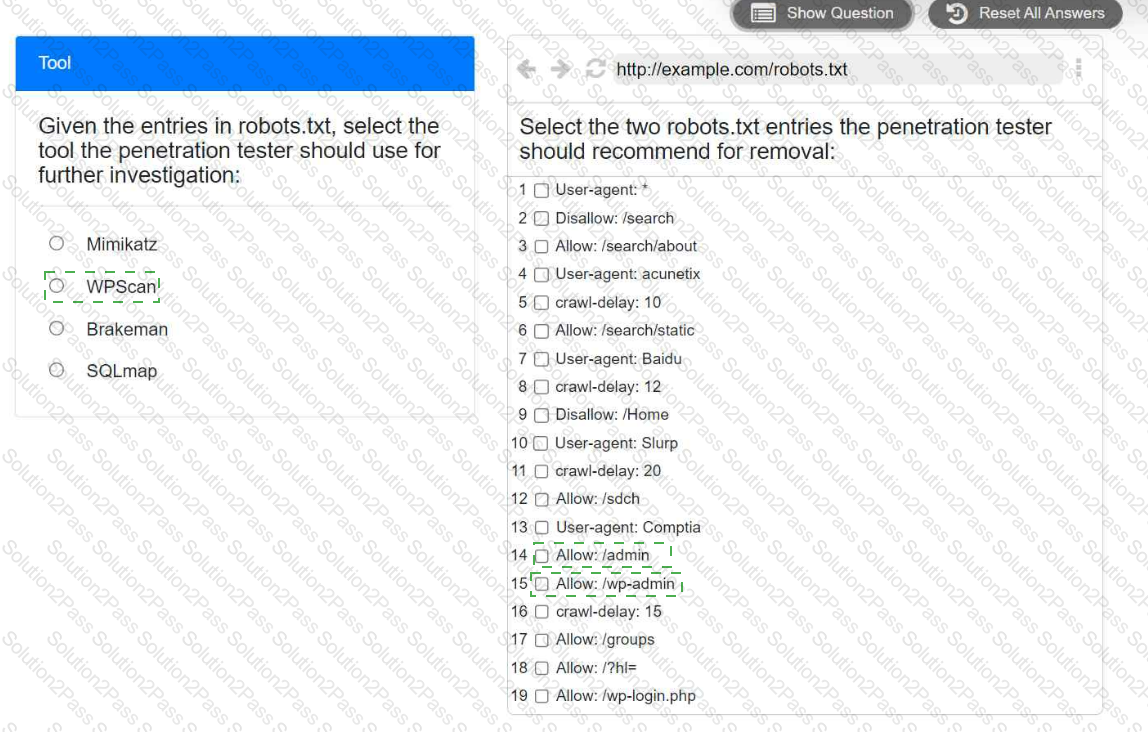
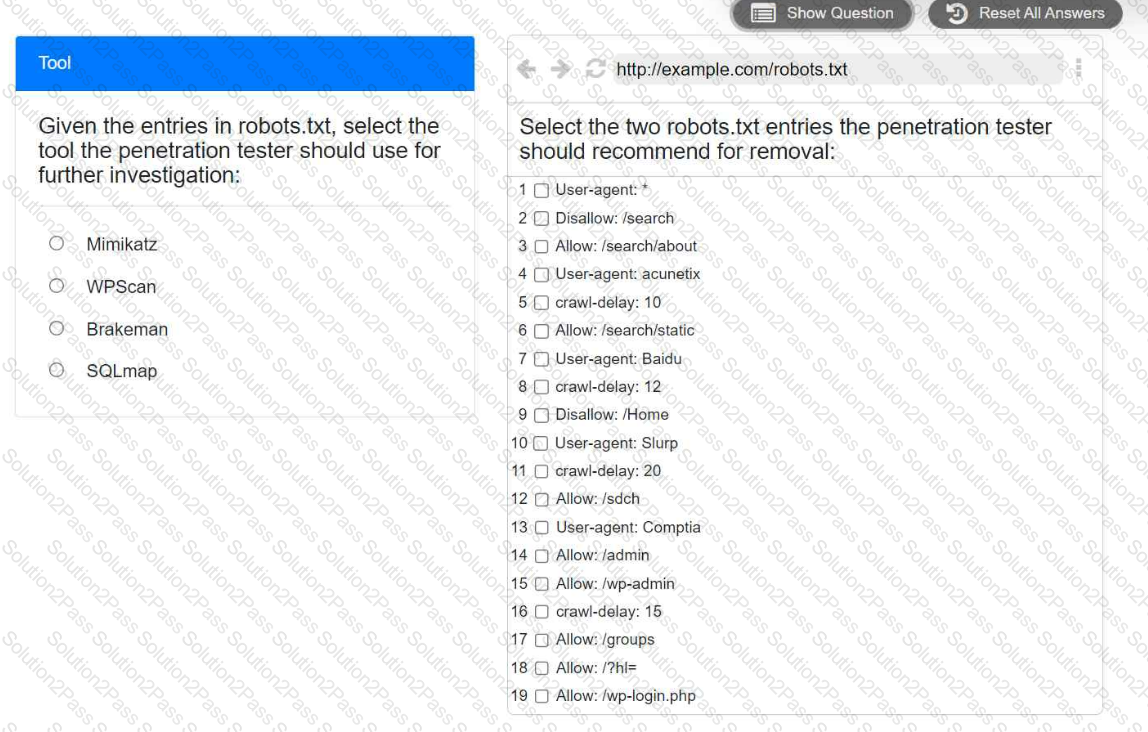
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS
Select the tool the penetration tester should use for further investigation.
Select the two entries in the robots.txt file that the penetration tester should recommend for removal.
A penetration tester is reviewing the security of a web application running in an laaS compute instance. Which of the following payloads should the tester send to get the running process credentials?